The infamous Emotet malware has returned with renewed vigor as part of a large-volume malspam marketing campaign intended to fall payloads like IcedID and Bumblebee.
“Hundreds of countless numbers of email messages per day” have been sent considering the fact that early November 2022, organization security enterprise Proofpoint mentioned very last 7 days, including, “the new exercise implies Emotet is returning to its total operation performing as a delivery network for major malware families.”
Amongst the primary nations targeted are the U.S., the U.K., Japan, Germany, Italy, France, Spain, Mexico, and Brazil.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The Emotet-connected exercise was past noticed in July 2022, even though sporadic bacterial infections have been documented considering that then. In mid-Oct, ESET disclosed that Emotet might be readying for a new wave of attacks, pointing out updates to its “systeminfo” module.
The malware, which is attributed to a threat actor acknowledged as Mummy Spider (aka Gold Crestwood or TA542), staged a revival of kinds late last calendar year right after its infrastructure was dismantled for the duration of a coordinated regulation enforcement operation in January 2021.
Europol called Emotet the “world’s most perilous malware” for its capacity to act as a “most important doorway opener for computer system systems” to deploy up coming-phase binaries that facilitate info theft and ransomware. It started out off in 2014 as a banking trojan before evolving into a botnet.
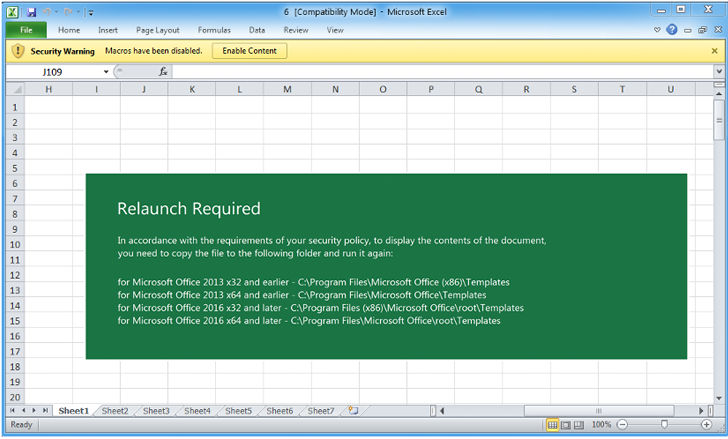
Infection chains involving the malware are acknowledged to employ generic lures as very well as the technique of email thread hijacking to entice recipients into opening macro-enabled Excel attachments.
“Next Microsoft’s the latest announcement that it would get started disabling macros by default in Workplace documents downloaded from the internet, several malware people have started migrating away from Office macros to other shipping mechanisms like ISO and LNK information,” Cisco Talos claimed before this month.
“For that reason, it is appealing to take note that this new marketing campaign of Emotet is applying its aged technique of distributing destructive Microsoft Business documents (maldocs) via email-based mostly phishing.
An different approach urges possible victims to duplicate the file to a Microsoft Business Template area – a dependable spot – and launch the entice document from there instead of having to explicitly allow macros to activate the get rid of-chain.
The renewed exercise has also been accompanied by alterations to the Emotet loader part, and addition of new instructions, and updates to the packer to resist reverse engineering.
1 of the adhere to-on payloads dispersed by way of Emotet is a brand new variant of the IcedID loader, which gets instructions to browse and ship file contents to a distant server, in addition to executing other backdoor instructions that allow for it to extract web browser details.
The use of IcedID is regarding as it truly is very likely a precursor for ransomware, the scientists pointed out. A different malware dropped via Emotet is Bumblebee, in accordance to Palo Alto Networks Unit 42.
“All round, these modifications manufactured to the client suggest the developers are trying to discourage researchers and decrease the amount of phony or captive bots that exist in just the botnet,” researchers Pim Trouerbach and Axel F reported.
“Emotet has not shown total features and constant adhere to-on payload shipping (that’s not Cobalt Strike) since 2021, when it was observed distributing The Trick and Qbot.”
Found this article intriguing? Observe THN on Fb, Twitter and LinkedIn to go through more distinctive content we put up.
Some pieces of this report are sourced from:
thehackernews.com


 How we test: Security software
How we test: Security software