Israeli spy ware maker NSO Team deployed at the very least 3 novel “zero-simply click” exploits from iPhones in 2022 to infiltrate defenses erected by Apple and deploy Pegasus, according to the latest findings from Citizen Lab.
“NSO Group buyers greatly deployed at the very least 3 iOS 15 and iOS 16 zero-simply click exploit chains against civil modern society targets close to the world,” the interdisciplinary laboratory dependent at the University of Toronto mentioned.
NSO Team is the maker of Pegasus, a advanced cyber weapon that is capable of extracting delicate facts saved in a device – e.g., messages, spots, photographs, and contact logs, amongst other folks — in true-time. It can be normally shipped to specific iPhones employing zero-click on and/or zero-working day exploits.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
When it has been pitched as a instrument for regulation enforcement companies to fight major crimes these types of as baby sexual abuse and terrorism, it has also been deployed illegally by authoritarian governments to spy on human legal rights defenders, democracy advocates, journalists, dissidents, and other people.
The misuse of Pegasus prompted the U.S. authorities to increase NSO Team to its trade blocklist in late 2021, with Apple filing a lawsuit of its personal from the business for focusing on its consumers.
In July 2022, it emerged that the adware was utilised against Thai activists involved in the country’s pro-democracy protests in between Oct 2020 and November 2021 using two zero-simply click exploits named KISMET and FORCEDENTRY.
Two of the targets of the most up-to-date campaign unearthed by Citizen Lab include human legal rights defenders from Centro PRODH, which represents victims of the Mexican Army’s extrajudicial killings and disappearances. The intrusions happened in June 2022.
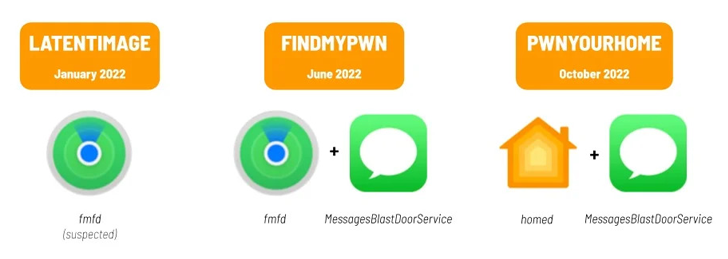
This entailed the use of three disparate exploit chains dubbed LATENTIMAGE, FINDMYPWN, and PWNYOURHOME that weaponized many flaws in iOS 15 and iOS 16 as zero-days to penetrate the devices and finally start Pegasus –
- LATENTIMAGE (iOS model 15.1.1, detected in January 2022) – An exploit that is suspected to contain the iPhone’s Uncover My function and SpringBoard
- FINDMYPWN (iOS variations 15.5 and 15.6, detected in June 2022) – A two-phase exploit that helps make use of Locate My functionality and iMessage
- PWNYOURHOME (iOS model 16..3, detected in Oct 2022) – A two-section exploit that brings together the HomeKit performance built into iPhones and iMessage to bypass BlastDoor protections
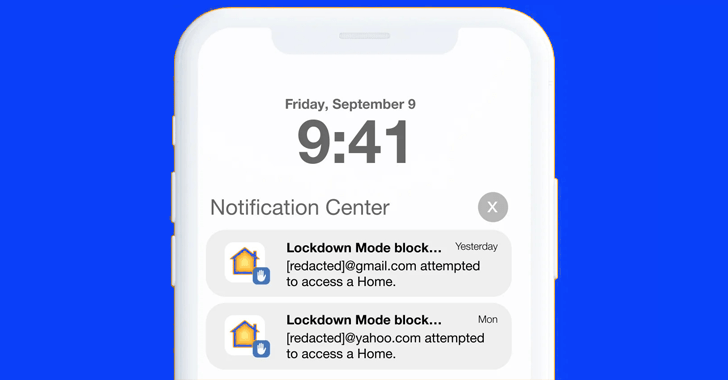
In an encouraging indication, Citizen Lab reported it observed proof of Lockdown Mode stepping in to block an tried PWNYOURHOME attack, warning buyers that it blocked unknown events with Gmail and Yahoo! accounts from hoping to “accessibility a Home.”
The advancement marks the initial publicly documented instance where Lockdown Manner, which is developed to decrease the iPhone’s attack floor, has correctly secured somebody from a compromise.
That mentioned, Citizen Lab pointed out that NSO Group “may have figured out a way to suitable the notification issue, these kinds of as by fingerprinting Lockdown Method.” Apple has given that transported numerous security enhancements to HomeKit in iOS 16.3.1 and sent out notifications to qualified victims in November and December 2022, and March 2023.
The results are the latest example of NSO’s evolving attack strategies to break into iPhones without the need of requiring any targets to acquire any motion to bring about the infection.
They also coincide with a new investigation from the New York Occasions uncovering Mexico’s use of Pegasus to goal human rights defenders in new months, detailing how the country turned the very first and most prolific person of the adware.
In still yet another indication of the pervasive character of these kinds of strategies, Jamf Threat Labs uncovered evidence of a human rights activist primarily based in the Center East as effectively as a Hungarian journalist being targeted with spy ware. Their names were not disclosed.
Forthcoming WEBINARDefend with Deception: Advancing Zero Trust Security
Uncover how Deception can detect innovative threats, cease lateral motion, and improve your Zero Believe in method. Be part of our insightful webinar!
Save My Seat!
The attack targeting the journalist’s iPhone is also important for the reality that the gadget was an iPhone 6s, which is no extended compatible with the hottest iOS version, indicating threat actors’ penchant for exploiting identified and not known vulnerabilities to fulfill their ambitions.
Whilst Apple does again-port fixes for critical flaws to more mature gadgets (the current model supported by iPhone 6s is iOS 15.7.5), it is critical to observe that not all vulnerabilities are tackled for legacy units.
“As a outcome, risk actors can go on to exploit unpatched vulnerabilities that have been patched on more recent supported devices, probably supplying attackers extra time and extra information and facts to obtain remote accessibility to qualified products,” Jamf mentioned.
To safeguard towards spyware attacks, it’s advisable to apply the latest operating technique updates, upgrade outdated gadgets to more recent iPhone or iPad versions, and think about enabling Lockdown Mode.
The U.K. Countrywide Cyber Security Centre (NCSC), in an advisory launched on April 19, 2023, cautioned the “proliferation of industrial cyber applications will pose a increasing danger to businesses and people globally.”
“The business proliferation of cyber resources and companies lowers the barrier to entry to state and non-condition actors in acquiring capacity and intelligence that they would not if not be equipped to develop or obtain,” the agency said.
Identified this report interesting? Stick to us on Twitter and LinkedIn to go through extra exclusive information we publish.
Some components of this report are sourced from:
thehackernews.com

 Recycled Network Devices Exposing Corporate Secrets
Recycled Network Devices Exposing Corporate Secrets