A hacking group dubbed OilAlpha with suspected ties to Yemen’s Houthi movement has been connected to a cyber espionage campaign focusing on growth, humanitarian, media, and non-governmental companies in the Arabian peninsula.
“OilAlpha utilised encrypted chat messengers like WhatsApp to launch social engineering attacks against its targets,” cybersecurity business Recorded Long term claimed in a technological report revealed Tuesday.
“It has also utilised URL backlink shorteners. Per victimology evaluation, it seems a vast majority of the targeted entities ended up Arabic-language speakers and operated Android devices.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
OilAlpha is the new cryptonym specified by Recorded Long term to two overlapping clusters beforehand tracked by the enterprise under the names TAG-41 and TAG-62 because April 2022. TAG-XX (shorter for Danger Action Team) is the short-term moniker assigned to emerging risk teams.
The evaluation that the adversary is acting in the fascination of the Houthi motion is based on the actuality that the infrastructure utilized in the attacks is just about exclusively related with Community Telecommunication Company (PTC), a Yemeni telecom support service provider subjected to Houthi’s regulate.
That acquiring explained, the persistent use of PTC property will not exclude the probability of a compromise by an not known 3rd-party. Recorded Upcoming, nonetheless, mentioned that it did not find any evidence to again up this line of reasoning.
An additional factor is the use of malicious Android-primarily based programs to very likely surveil delegates involved with Saudi Arabian federal government-led negotiations. These apps mimicked entities tied to the Saudi Arabian governing administration and a humanitarian corporation in the U.A.E.
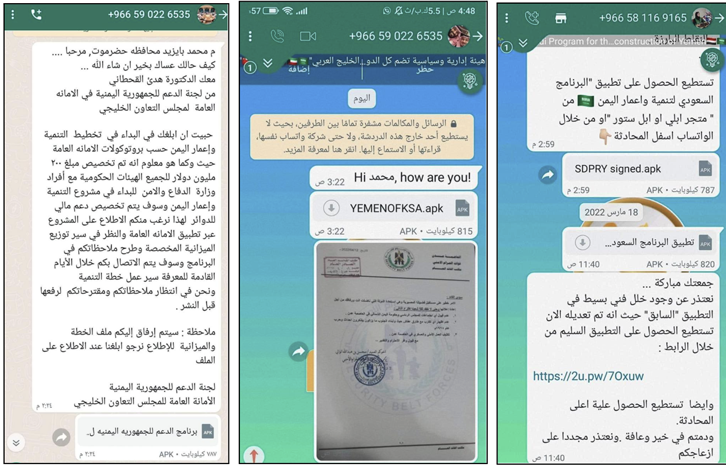
The attack chains start with potential targets – political representatives, media personalities, and journalists – getting the APK documents straight from WhatsApp accounts working with Saudi Arabian telephone numbers by masquerading the apps as belonging to UNICEF, NGOs, and other relief businesses.
The apps, for their aspect, act as a conduit to drop a distant obtain trojan named SpyNote (aka SpyMax) that comes with a plethora of features to seize delicate information and facts from contaminated equipment.
Approaching WEBINARLearn to Cease Ransomware with Serious-Time Defense
Join our webinar and master how to quit ransomware attacks in their tracks with genuine-time MFA and service account safety.
Help you save My Seat!
“OilAlpha’s concentrate in targeting Android units is not astonishing because of to the superior saturation of Android devices in the Arabian Peninsula location,” Recorded Future said.
The cybersecurity corporation said it also observed njRAT (aka Bladabindi) samples speaking with command-and-regulate (C2) servers connected with the group, indicating that it is concurrently making use of desktop malware in its functions.
“OilAlpha released its attacks at the behest of a sponsoring entity, namely Yemen’s Houthis,” it theorized. “OilAlpha could be specifically affiliated to its sponsoring entity, or could also be working like a contracting party.”
“Whilst OilAlpha’s exercise is pro-Houthi, there is inadequate evidence to advise that Yemeni operatives are dependable for this risk activity. Exterior threat actors like Lebanese or Iraqi Hezbollah, or even Iranian operators supporting the IRGC, might have led this danger activity.”
Uncovered this article exciting? Adhere to us on Twitter and LinkedIn to go through extra unique content material we publish.
Some pieces of this article are sourced from:
thehackernews.com

 Acronis Launches EDR Solution with Potential for AI Integration
Acronis Launches EDR Solution with Potential for AI Integration