Cybersecurity scientists have uncovered an ongoing social engineering campaign that bombards enterprises with spam e-mail with the target of obtaining first entry to their environments for observe-on exploitation.
“The incident will involve a risk actor frustrating a user’s email with junk and contacting the consumer, featuring aid,” Quick7 researchers Tyler McGraw, Thomas Elkins, and Evan McCann claimed.
“The risk actor prompts impacted consumers to download remote checking and administration software like AnyDesk or make use of Microsoft’s developed-in Swift Support element in get to build a remote link.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The novel marketing campaign is stated to be underway because late April 2024, with the e-mails primarily consisting of newsletter indicator-up confirmation messages from legitimate corporations and carried out so with an goal to overwhelm email safety remedies.
The impacted buyers are then approached more than phone phone calls by masquerading as the company’s IT workforce, tricking them into setting up a distant desktop software below the guise of resolving the email issues.
The remote access to their computer system is subsequently leveraged to down load extra payloads to harvest qualifications and maintain persistence on the hosts.

This is accomplished by executing a variety of batch scripts, a single of which also establishes get hold of with a command-and-regulate (C2) server to obtain a legitimate copy of OpenSSH for Windows and in the end launch a reverse shell to the server.
In a person incident noticed by the cybersecurity business, the danger actors driving the marketing campaign unsuccessfully tried to deploy Cobalt Strike beacons to other belongings inside the compromised network.
Whilst there is no evidence of ransomware currently being executed as component of the campaign, Quick7 stated the exercise overlaps with beforehand discovered attack indicators associated with the Black Basta ransomware operators.
The attack chain has also been made use of to deliver further remote monitoring and management instruments like ConnectWise ScreenConnect as perfectly as a remote accessibility trojan referred to as NetSupport RAT, which has been just lately put to use by FIN7 actors as section of a malvertising campaign.
This is specifically noteworthy in light-weight of the fact that FIN7 actors are suspected to have shut ties with Black Basta. Even though FIN7 in the beginning used place-of-sale (PoS) malware to carry out economical fraud, it has due to the fact pivoted to ransomware functions, possibly in the ability of an affiliate or conducting its personal operations less than the names DarkSide and BlackMatter.
“Soon after properly getting obtain to the compromised asset, Rapid7 observed the threat actor trying to deploy Cobalt Strike beacons, disguised as a reputable Dynamic Connection Library (DLL) named 7z.DLL, to other assets in the similar network as the compromised asset working with the Impacket toolset,” Fast7 reported.
Phorpiex Distributes LockBit Black
The progress will come as Proofpoint uncovered facts of a new LockBit Black (aka LockBit 3.) ransomware marketing campaign that leverages the Phorpiex (aka Trik) botnet as a conduit to provide email messages that contains the ransomware payload.
Thousands and thousands of messages are believed to have been despatched out throughout the higher-volume campaign that began on April 24, 2024. It truly is at the moment not clear who is guiding the attack.
“The LockBit Black sample from this marketing campaign was very likely developed from the LockBit builder that was leaked for the duration of the summer months of 2023,” Proofpoint researchers explained.
“The LockBit Black builder has delivered risk actors with entry to proprietary and complex ransomware. The combination of this with the longstanding Phorpiex botnet amplifies the scale of these types of threat campaigns and will increase odds of effective ransomware attacks.”
Insights into the Mallox Ransomware Team
Ransomware attacks have also been observed brute-forcing Microsoft SQL servers to deploy the Mallox file-encrypting malware by using a .NET-based loader named PureCrypter, in accordance to Sekoia.

A closed ransomware group running from the European area, Mallox is known to be distributed because at least June 2021. It acquired prominence in mid-2022 pursuing its transition to a ransomware-as-a-services (RaaS) model and a double extortion technique.
Two distinctive on line personas linked with the team, specifically Mallx and RansomR, have been noticed actively recruiting affiliates for the procedure on various underground boards.
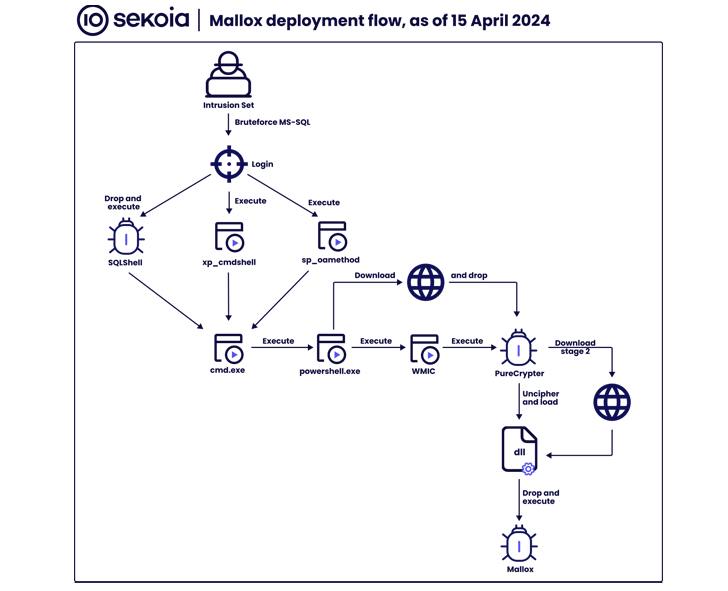
Even further analysis of the threat actor’s info exfiltration server and their dark web infrastructure has unveiled the names of unique “workers” members, like Admin, Help, Maestro, Group, Neuroframe, Panda, Grindr, Hiervos, and Vampire.
“Mallox is almost surely an opportunistic intrusion established impacting corporations in many verticals, notably the producing, the retail and the technology ones,” the organization claimed.
“Even though Mallox reps actively seek out high-income targets (as indicated in recruitment posts on cybercrime community forums), most of the ransomware’s victims recognized in open-resource are smaller and center measurement enterprises.”
Observed this post interesting? Adhere to us on Twitter and LinkedIn to read far more special information we submit.
Some parts of this short article are sourced from:
thehackernews.com


 Apple and Google Launch Cross-Platform Feature to Detect Unwanted Bluetooth Tracking Devices
Apple and Google Launch Cross-Platform Feature to Detect Unwanted Bluetooth Tracking Devices