Cybersecurity researchers have disclosed a security flaw in the Opera web browser for Microsoft Windows and Apple macOS that could be exploited to execute any file on the fundamental working method.
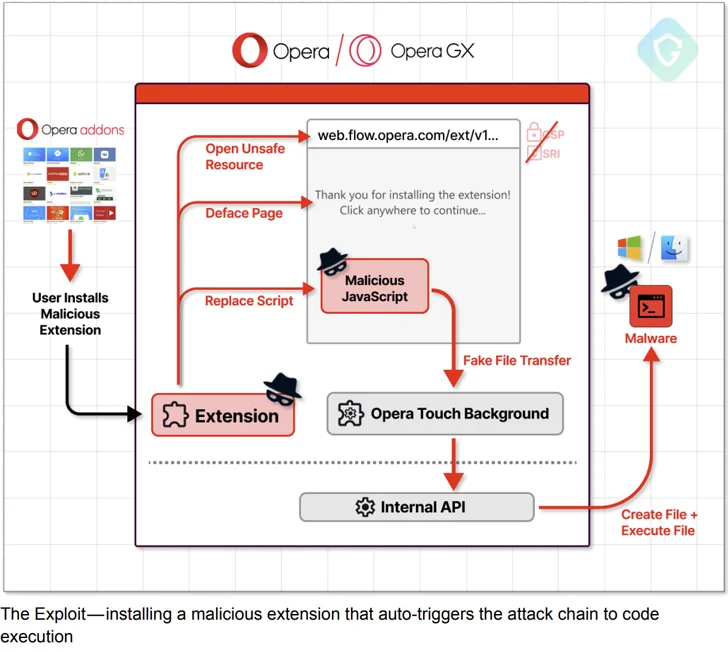
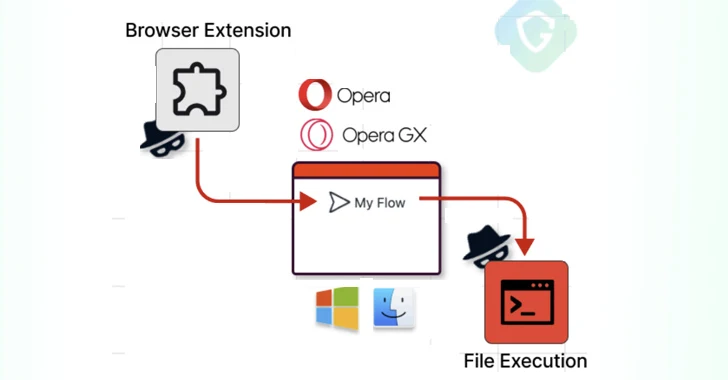
The remote code execution vulnerability has been codenamed MyFlaw by the Guardio Labs research group owing to the truth that it usually takes advantage of a element called My Flow that can make it feasible to sync messages and data files concerning cell and desktop products.
“This is accomplished by way of a managed browser extension, effectively bypassing the browser’s sandbox and the whole browser procedure,” the organization stated in a statement shared with The Hacker Information.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The issue impacts the two the Opera browser and Opera GX. Subsequent liable disclosure on November 17, 2023, it was resolved as part of updates delivered on November 22, 2023.
My Circulation features a chat-like interface to trade notes and information, the latter of which can be opened by way of a web interface, meaning a file can be executed outside the house of the browser’s security boundaries.

It is pre-installed in the browser and facilitated by suggests of a created-in (or interior) browser extension identified as “Opera Contact Background,” which is dependable for speaking with its cellular counterpart.
This also indicates that the extension comes with its individual manifest file specifying all the expected permissions and its behavior, which include a house identified as externally_connectable that declares which other web web pages and extensions can link to it.
In the situation of Opera, the domains that can discuss to the extension need to match the designs “*.movement.opera.com” and “.flow.op-test.net” – equally managed by the browser seller alone.
“This exposes the messaging API to any web page that matches the URL patterns you specify,” Google notes in its documentation. “The URL sample will have to include at least a 2nd-level area.”
Guardio Labs said it was able to unearth a “long-overlooked” edition of the My Flow landing web page hosted on the domain “web.circulation.opera.com” using the urlscan.io web site scanner instrument.

“The page itself appears very the exact as the present just one in generation, but alterations lie below the hood: Not only that it lacks the [content security policy] meta tag, but it also holds a script tag calling for a JavaScript file without any integrity look at,” the company mentioned.
“This is specifically what an attacker requirements – an unsafe, forgotten, vulnerable to code injection asset, and most importantly, has access to (quite) high permission indigenous browser API.”
The attack chain then hinges, making a specifically crafted extension that masquerades as a cell unit to pair with the victim’s personal computer and transmit an encrypted destructive payload by means of the modified JavaScript file to the host for subsequent execution by prompting the user to click anywhere on the monitor.

The conclusions emphasize the raising complexity of browser-based mostly attacks and the different vectors that can be exploited by risk actors to their gain.
“Even with working in sandboxed environments, extensions can be effective equipment for hackers, enabling them to steal details and breach browser security boundaries,” the company told The Hacker Information.
“This underscores the want for interior layout modifications at Opera and advancements in Chromium’s infrastructure. For occasion, disabling third-party extension permissions on devoted creation domains, identical to Chrome’s web keep, is proposed but has not yet been implemented by Opera.”
When reached for remark, Opera reported it moved quickly to close the security gap and employ a correct on the server side and that it is using ways to avoid this sort of issues from going on once again.
“Our existing framework employs an HTML conventional, and is the most secure choice that does not crack key operation,” the company stated. “Immediately after Guardio alerted us to this vulnerability, we taken off the induce of these issues and we are producing certain that related troubles will not seem in the foreseeable future.”
“We would like to thank Guardio Labs for their perform on uncovering and immediately alerting us to this vulnerability. This collaboration demonstrates how we operate with each other with security professionals and researchers close to the environment to enhance our very own efforts at protecting and bettering the security of our merchandise and ensuring our customers have a risk-free on line expertise.”
Identified this write-up appealing? Comply with us on Twitter and LinkedIn to go through a lot more unique material we put up.
Some components of this article are sourced from:
thehackernews.com

 High-Severity Flaws Uncovered in Bosch Thermostats and Smart Nutrunners
High-Severity Flaws Uncovered in Bosch Thermostats and Smart Nutrunners