Researchers have disclosed a new large-scale cryptocurrency mining campaign concentrating on the NPM JavaScript bundle repository.
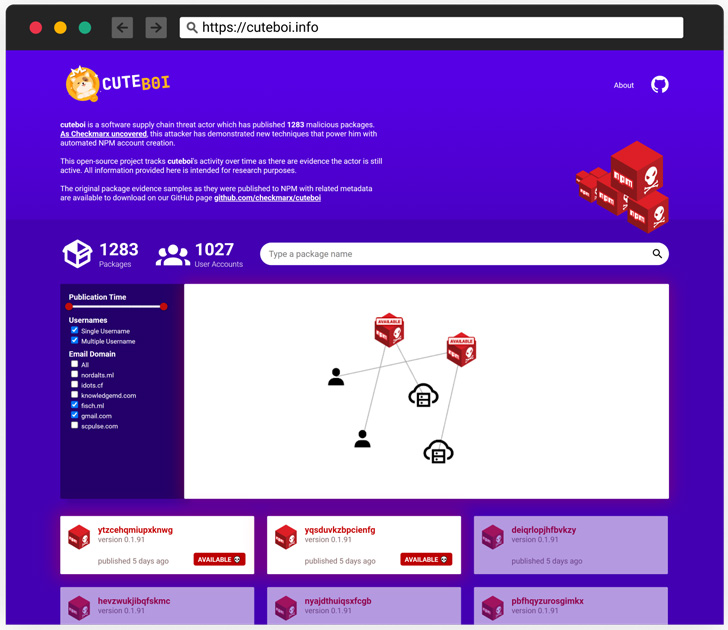
The destructive exercise, attributed to a program source chain danger actor dubbed CuteBoi, involves an array of 1,283 rogue modules that were being printed in an automatic style from in excess of 1,000 various person accounts.
“This was performed using automation which contains the ability to move the NPM 2FA obstacle,” Israeli software security screening enterprise Checkmarx said. “This cluster of packages would seem to be a section of an attacker experimenting at this level.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
All the released deals in question are stated to harbor in the vicinity of-equivalent supply code from an already current bundle named eazyminer that’s made use of to mine Monero by means of employing unused means on web servers.
One noteworthy modification involves the URL to which the mined cryptocurrency should be despatched, while setting up the rogue modules will not carry about a negative outcome.
“The copied code from eazyminer features a miner features intended to be brought on from within another system and not as a standalone resource,” researcher Aviad Gershon said. “The attacker did not change this attribute of the code and for that rationale, it is not going to run upon installation.”
Like observed in the case of Pink-LILI previously this 12 months, the deals are revealed by way of an automation method that enables the danger actor to defeat two-factor authentication (2FA) protections.
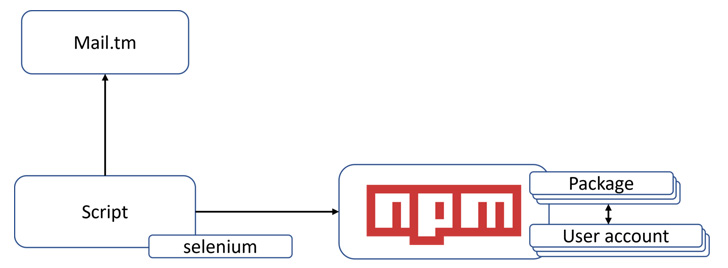
Nevertheless, even though the former associated location up a personalized server and employing a mix of instruments like Selenium and Interactsh to programmatically produce an NPM consumer account and defeat 2FA, CuteBoi depends on a disposable email company referred to as mail.tm.

The free system also provides a Relaxation API, “enabling courses to open up disposable mailboxes and browse the acquired e-mails despatched to them with a straightforward API connect with,” letting the danger actor to circumvent the 2FA problem when producing a user account.
The findings coincide with yet another NPM-similar common computer software provide chain attack dubbed IconBurst that’s engineered to harvest delicate knowledge from forms embedded in downstream cellular programs and web-sites.
Located this report appealing? Abide by THN on Facebook, Twitter and LinkedIn to study extra special material we article.
Some areas of this posting are sourced from:
thehackernews.com


 Maui ransomware actively targeting US healthcare organizations
Maui ransomware actively targeting US healthcare organizations