Extra than 200 Android apps masquerading as physical fitness, photo modifying, and puzzle apps have been noticed distributing spy ware known as Facestealer to siphon person credentials and other worthwhile data.
“Equivalent to Joker, a different piece of mobile malware, Facestealer changes its code usually, hence spawning a lot of variants,” Trend Micro analysts Cifer Fang, Ford Quin, and Zhengyu Dong explained in a new report. “Given that its discovery, the spyware has constantly beleaguered Google Participate in.”
Facestealer, to start with documented by Medical doctor Web in July 2021, refers to a team of fraudulent applications that invade the official app market for Android with the target of plundering delicate data these as Fb login qualifications.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
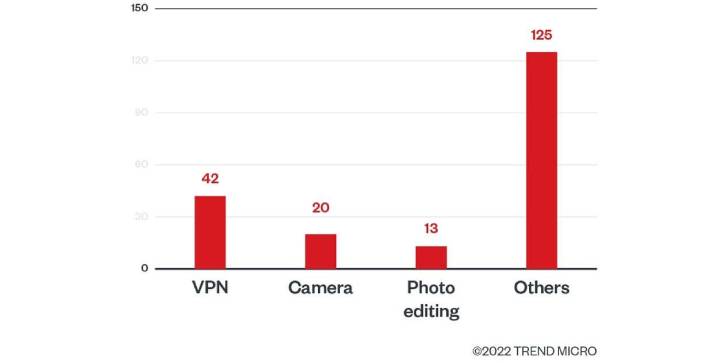
Of the 200 applications, 42 are VPN expert services, followed by a digital camera (20) and picture enhancing apps (13). In addition to harvesting credentials, the apps are also made to accumulate Facebook cookies and individually identifiable information and facts connected with a victim’s account.
Additionally, Craze Micro disclosed that it uncovered in excess of 40 rogue cryptocurrency miner applications that concentrate on buyers interested in virtual cash with malware created to trick people into viewing advertisements and having to pay for membership providers.
Some of the pretend crypto applications, such as Cryptomining Farm Your have Coin, choose it 1 phase even further by also making an attempt to steal non-public keys and mnemonic phrases (or seed phrases) that are made use of to get well accessibility to a cryptocurrency wallet.
To steer clear of slipping victim to this sort of fraud applications, it truly is advisable that customers verify adverse assessments, verify the legitimacy of the developers, and stay away from downloading apps from third-party application stores.
New examine analyzes destructive Android applications put in in the wild
The results occur as scientists from NortonLifeLock and Boston University published what they termed the “major on-machine review” of potentially damaging apps (PHAs) on Android-based on 8.8 million PHAs put in on above 11.7 million devices between 2019 and 2020.
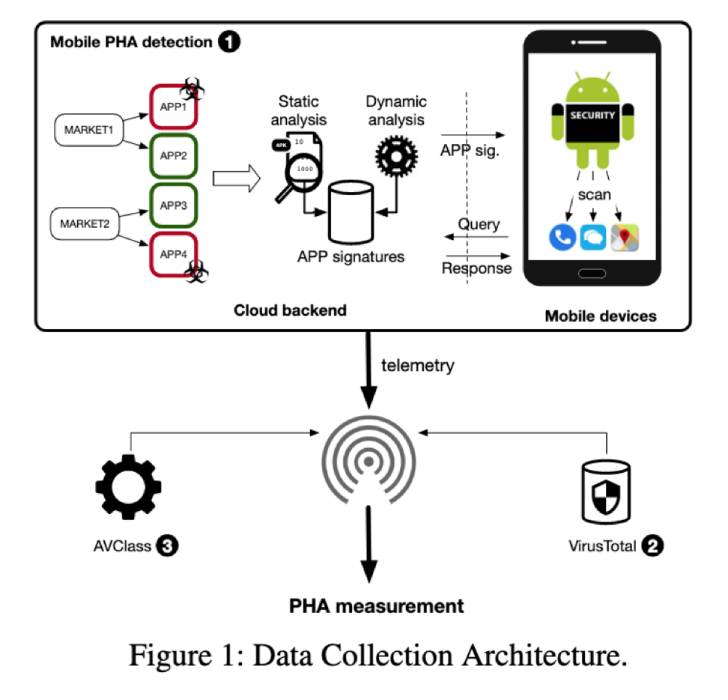
“PHAs persist on Google Participate in for 77 days on typical and 34 days on third-party marketplaces,” the examine famous, pointing out the delay amongst when PHAs are recognized and when they are eradicated, including 3,553 apps exhibit inter-market place migration right after being taken down.

On prime of that, the investigation also displays that PHAs linger for a considerably for a longer period interval on normal when customers change devices and immediately install the apps when restoring from a backup.
As lots of as 14,000 PHAs are said to have been transferred to 35,500 new Samsung equipment by employing the Samsung Smart Change mobile app, with the applications lasting on the telephones for a time period of approximately 93 days.
“The Android security model severely boundaries what cell security goods can do when detecting a destructive app, permitting PHAs to persist for lots of days on target devices,” the academics said. “The recent warning procedure used by cellular security programs is not effective in convincing customers to immediately uninstall PHAs.”
Located this report intriguing? Follow THN on Facebook, Twitter and LinkedIn to go through far more exceptional articles we put up.
Some areas of this short article are sourced from:
thehackernews.com


 US and EU Move Closer on Cyber in New Trade Pact
US and EU Move Closer on Cyber in New Trade Pact