A enormous marketing campaign has infected more than 4,500 WordPress web sites as section of a prolonged-jogging operation that’s been thought to be active given that at the very least 2017.
According to GoDaddy-owned Sucuri, the bacterial infections require the injection of obfuscated JavaScript hosted on a destructive domain named “observe[.]violetlovelines[.]com” that is built to redirect people to unwelcome websites.
The most up-to-date operation is said to have been active considering the fact that December 26, 2022, in accordance to knowledge from urlscan.io. A prior wave observed in early December 2022 impacted extra than 3,600 sites, whilst an additional set of attacks recorded in September 2022 ensnared a lot more than 7,000 internet sites.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The rogue code is inserted in the WordPress index.php file, with Sucuri noting that it has taken off this kind of adjustments from more than 33,000 files on the compromised sites in the earlier 60 days.
“In current months, this malware marketing campaign has slowly switched from the notorious faux CAPTCHA press notification scam pages to black hat ‘ad networks’ that alternate concerning redirects to legitimate, sketchy, and purely malicious web sites,” Sucuri researcher Denis Sinegubko claimed.
Hence when unsuspecting buyers land on one particular of the hacked WordPress sites, a redirect chain is brought on by usually means of a traffic path program, landing the victims on webpages serving sketchy ads about products that ironically block unwelcome adverts.
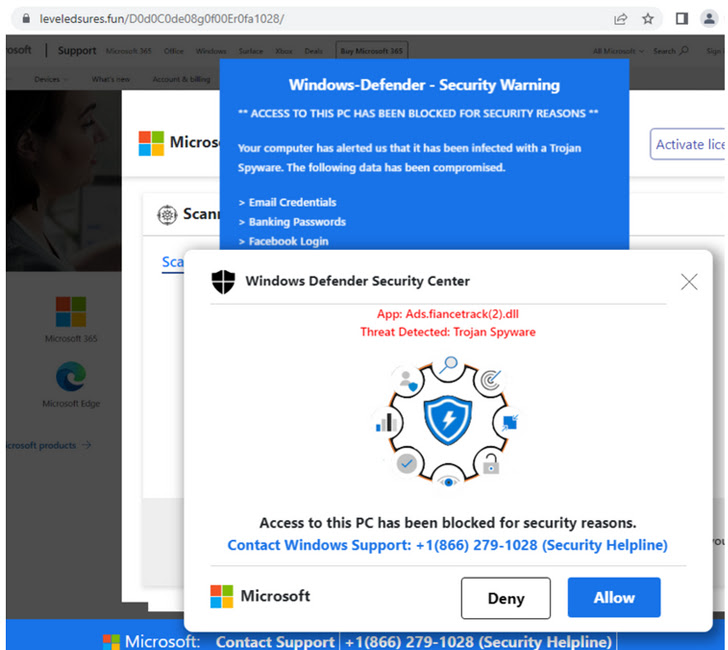
Even a lot more troublingly, the site for a person such ad blocker named Crystal Blocker is engineered to show misleading browser update alerts to trick the end users into putting in its extension depending on the web browser employed.
The browser extension is utilized by almost 110,000 users spanning Google Chrome (60,000+), Microsoft Edge (40,000+), and Mozilla Firefox (8,635).
“And when the extensions without a doubt have advertisement blocking functionality, there is no guarantee that they are safe to use — and may perhaps include undisclosed capabilities in the present-day version or in potential updates,” Sinegubko stated.
Some of the redirects also slide into the outright nefarious category, with the contaminated web sites acting as a conduit for initiating push-by downloads.
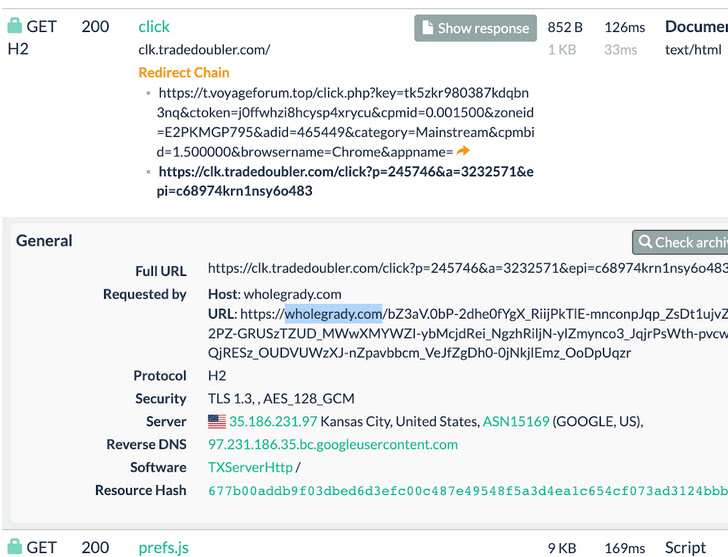
This also includes retrieving from Discord CDN an data-stealing malware acknowledged as Raccoon Stealer, which is capable of plundering sensitive details such as passwords, cookies, autofill knowledge from browsers, and crypto wallets.
The results occur as threat actors are placing up lookalike internet websites for a variety of legitimate software package to distribute stealers and trojans through destructive ads in Google lookup benefits.
Google has because stepped in to block a person of the rogue domains included in the redirect plan, classifying it as an unsafe site that installs “unwelcome or malicious program on visitors’ computer systems.”
To mitigate these kinds of threats, WordPress website entrepreneurs are encouraged to improve passwords and update mounted themes and plugins as nicely as eliminate these that are unused or deserted by their builders.
Observed this post interesting? Comply with us on Twitter and LinkedIn to browse a lot more special content material we post.
Some sections of this article are sourced from:
thehackernews.com


 Ticketmaster Claims Bot Attack Disrupted Taylor Swift Tour Sales
Ticketmaster Claims Bot Attack Disrupted Taylor Swift Tour Sales