An unknown threat actor compromised an software applied by multiple entities in Pakistan to provide ShadowPad, a successor to the PlugX backdoor that is generally linked with Chinese hacking crews.
Targets provided a Pakistan authorities entity, a general public sector lender, and a telecommunications supplier, in accordance to Development Micro. The infections took spot in between mid-February 2022 and September 2022.
The cybersecurity enterprise mentioned the incident could be the final result of a offer-chain attack, in which a legitimate piece of computer software applied by targets of interest is trojanized to deploy malware capable of gathering delicate facts from compromised units.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
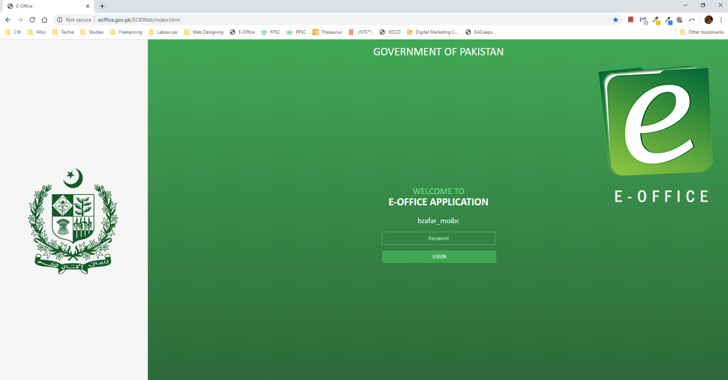
The attack chain normally takes the variety of a destructive installer for E-Workplace, an software made by the Countrywide Data Technology Board (NITB) of Pakistan to assist federal government departments go paperless.
It is at the moment not distinct how the backdoored E-Office installer was delivered to the targets. That said, there is no proof to date that the develop ecosystem of the Pakistani govt company in problem has been compromised.
This raises the risk that the menace actor attained the authentic installer and tampered it to involve malware, and then subsequently lured victims into running the trojanized edition by using social engineering attacks.
“A few information had been additional to the respectable MSI installer: Telerik.Windows.Data.Validation.dll, mscoree.dll, and mscoree.dll.dat,” Trend Micro researcher Daniel Lunghi claimed in an up to date assessment posted right now.
Telerik.Windows.Knowledge.Validation.dll is a legitimate applaunch.exe file signed by Microsoft, which is vulnerable to DLL aspect-loading and is utilised to sideload mscoree.dll that, in switch, masses mscoree.dll.dat, the ShadowPad payload.
Pattern Micro stated the obfuscation tactics made use of to conceal DLL and the decrypted last-phase malware are an evolution of an solution earlier exposed by Good Systems in January 2021 in relationship with a Chinese cyber espionage campaign undertaken by the Winnti group (aka APT41).
Impending WEBINARShield From Insider Threats: Learn SaaS Security Posture Administration
Apprehensive about insider threats? We have got you included! Sign up for this webinar to check out practical techniques and the insider secrets of proactive security with SaaS Security Posture Management.
Be part of Right now
Other than ShadowPad, write-up-exploitation routines have entailed the use of Mimikatz to dump passwords and credentials from memory.
Attribution to a regarded threat actor has been hampered by a deficiency of evidence, although the cybersecurity enterprise explained it identified malware samples such as Deed RAT, which has been attributed to the Area Pirates (or Webworm) danger actor.
“This entire campaign was the result of a really capable danger actor that managed to retrieve and modify the installer of a governmental software to compromise at least 3 delicate targets,” Lunghi claimed.
“The reality that the threat actor has obtain to a new model of ShadowPad probably back links it to the nexus of Chinese menace actors, while we are unable to point to a particular group with confidence.”
Located this short article intriguing? Follow us on Twitter and LinkedIn to examine far more exceptional content material we publish.
Some components of this write-up are sourced from:
thehackernews.com

 VirusTotal Data Leak Exposes Some Registered Customers’ Details
VirusTotal Data Leak Exposes Some Registered Customers’ Details