Cryptocurrency organizations are currently being targeted as component of a new campaign that delivers a distant entry trojan called Parallax RAT.
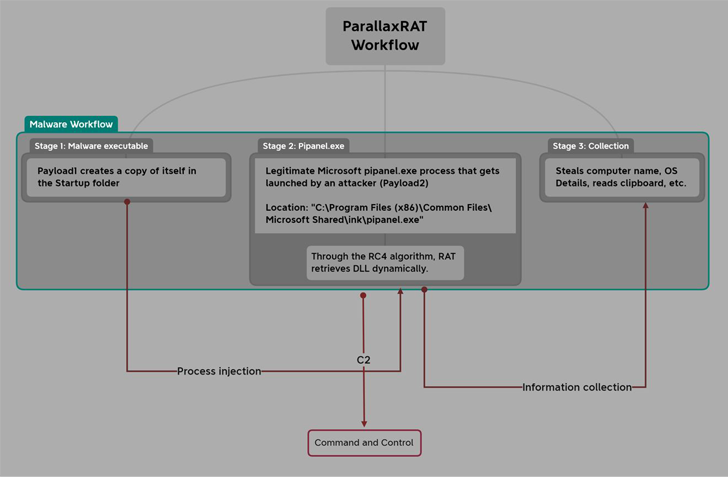
The malware “takes advantage of injection approaches to cover inside of authentic procedures, earning it difficult to detect,” Uptycs explained in a new report. “At the time it has been successfully injected, attackers can interact with their target by way of Windows Notepad that possible serves as a interaction channel.”
Parallax RAT grants attackers distant accessibility to sufferer equipment. It comes with features to add and obtain documents as effectively as record keystrokes and monitor captures.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
It has been place to use due to the fact early 2020 and was previously sent through COVID-19-themed lures. In February 2022, Proofpoint detailed a cybercrime menace actor dubbed TA2541 concentrating on aviation, aerospace, transportation, production, and protection industries working with different RATs, such as Parallax.
The to start with payload is a Visible C++ malware that employs the approach hollowing strategy to inject Parallax RAT into a legit Windows component termed pipanel.exe.
Parallax RAT, moreover gathering technique metadata, is also capable of accessing facts saved in the clipboard and even remotely rebooting or shutting down the compromised device.
One particular notable element of the attacks is the use of the Notepad utility to initiate discussions with the victims and instructing them to link to an actor-controlled Telegram channel.
Uptycs’ investigation of the Telegram chat reveals that the menace actor has an interest in crypto corporations this sort of as investment decision companies, exchanges, and wallet assistance providers.
The modus operandi entails looking general public sources like DNSdumpster for figuring out mail servers belonging to the specific providers via their mail exchanger (MX) records and sending phishing e-mail bearing the Parallax RAT malware.
The improvement will come as Telegram is increasingly turning into a hub for legal pursuits, enabling risk actors to manage their operations, distribute malware, and facilitate the sale of stolen knowledge, and other illegal merchandise in component owing to the platform’s lax moderation endeavours.
“A person rationale why Telegram is attractive to cybercriminals is its alleged developed-in encryption and the ability to create channels and massive, non-public teams,” KELA disclosed in an exhaustive evaluation printed very last thirty day period.
“These characteristics make it difficult for law enforcement and security researchers to keep an eye on and observe felony activity on the system. In addition, cybercriminals generally use coded language and choice spellings to connect on Telegram, creating it even far more hard to decipher their conversations.”
Observed this article attention-grabbing? Adhere to us on Twitter and LinkedIn to read much more special material we put up.
Some sections of this posting are sourced from:
thehackernews.com

 US Gov. Agencies Have 30 Days to Remove TikTok, Canada Follows Suit
US Gov. Agencies Have 30 Days to Remove TikTok, Canada Follows Suit