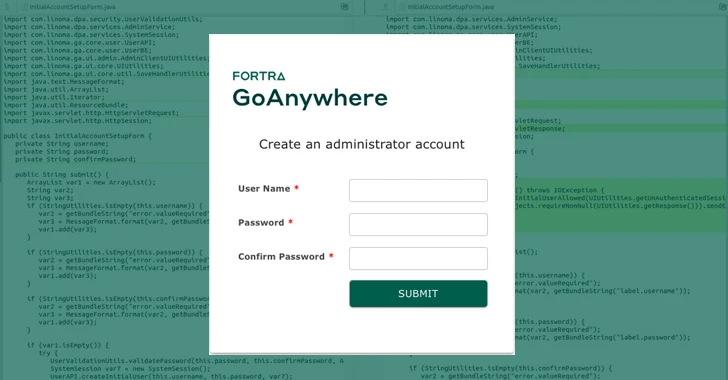
A critical security flaw has been disclosed in Fortra’s GoAnywhere Managed File Transfer (MFT) computer software that could be abused to generate a new administrator consumer.
Tracked as CVE-2024-0204, the issue carries a CVSS rating of 9.8 out of 10.
“Authentication bypass in Fortra’s GoAnywhere MFT prior to 7.4.1 makes it possible for an unauthorized person to develop an admin consumer via the administration portal,” Fortra claimed in an advisory introduced on January 22, 2024.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

Users who can not up grade to edition 7.4.1 can implement non permanent workarounds in non-container deployments by deleting the InitialAccountSetup.xhtml file in the install listing and restarting the solutions.
For container-deployed occasions, it’s proposed to replace the file with an vacant file and restart.
Mohammed Eldeeb and Islam Elrfai of Cairo-based Spark Engineering Consultants have been credited with finding and reporting the flaw in December 2023.
Cybersecurity firm Horizon3.ai, which posted a proof-of-concept (PoC) exploit for CVE-2024-0204, said the issue is the consequence of a route traversal weakness in the “/InitialAccountSetup.xhtml” endpoint that could be exploited to make administrative consumers.
“The simplest indicator of compromise that can be analyzed is for any new additions to the Admin Customers group in the GoAnywhere administrator portal Customers -> Admin People part,” Horizon3.ai security researcher Zach Hanley explained.

“If the attacker has still left this consumer listed here you may well be ready to notice its very last logon action listed here to gauge an approximate date of compromise.”
Even though there is no proof of active exploitation of CVE-2024-0204 in the wild, a different flaw in the exact merchandise (CVE-2023-0669, CVSS rating: 7.2) was abused by the Cl0p ransomware group to breach just about 130 victims last calendar year.
Observed this article appealing? Observe us on Twitter and LinkedIn to go through more special material we post.
Some elements of this post are sourced from:
thehackernews.com

 VexTrio: The Uber of Cybercrime – Brokering Malware for 60+ Affiliates
VexTrio: The Uber of Cybercrime – Brokering Malware for 60+ Affiliates