A sophisticated Facebook phishing campaign has been noticed exploiting a zero-working day flaw in Salesforce’s email companies, making it possible for menace actors to craft focused phishing messages applying the company’s area and infrastructure.
“Individuals phishing strategies cleverly evade typical detection techniques by chaining the Salesforce vulnerability and legacy quirks in Facebook’s Web Video games system,” Guardio Labs researchers Oleg Zaytsev and Nati Tal mentioned in a report shared with The Hacker News.
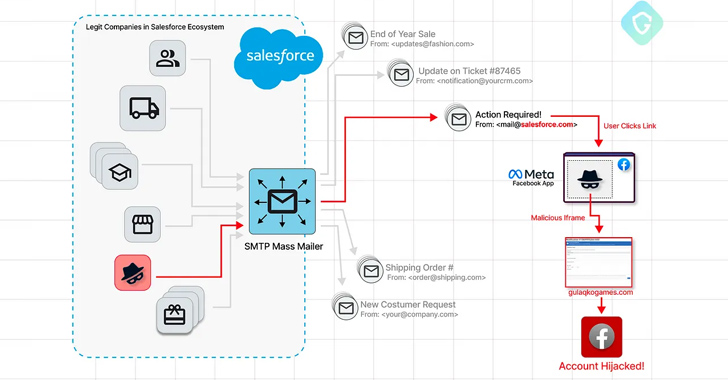
The email messages masquerade as coming from Meta, while remaining despatched from an email deal with with a “@salesforce.com” domain. They find to trick recipients into clicking on a backlink by declaring that their Facebook accounts are going through a “detailed investigation” because of to “suspicions of engaging in impersonation.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The objective is to immediate end users to a rogue landing webpage that is developed to capture the victim’s account credentials and two-factor authentication (2FA) codes. What will make the attack noteworthy is that the phishing package is hosted as a game underneath the Facebook apps system using the area applications.fb[.]com.

“So it really is a no-brainer why we have seen this email slipping as a result of conventional anti-spam and anti-phishing mechanisms. It involves legit one-way links (to facebook.com) and is sent from a legit email deal with of @salesforce.com, a person of the world’s major CRM suppliers,” the scientists discussed.
It really is really worth pointing out that Meta retired the Web Game titles aspect in July 2020, even though it truly is probable to keep aid for legacy game titles that were designed prior to its deprecation.
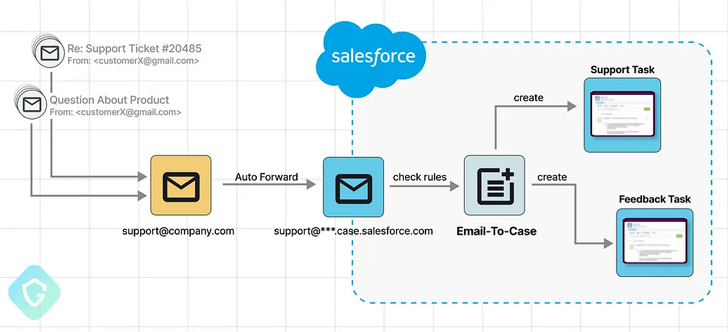
Although sending out email messages using a salesforce.com entails a validation action, Guardio Labs mentioned the scheme cleverly gets all over these protecting steps by configuring an Email-to-Circumstance inbound routing email handle that makes use of the salesforce.com domain and placing it up as the firm-extensive email deal with.
“This triggers the verification circulation that sends the email to this routing tackle, ending up as a new process in our procedure,” the researchers claimed, incorporating it sales opportunities to a state of affairs exactly where a salesforce.com email address can be confirmed just by clicking on the connection accompanying the request to incorporate the actor-managed deal with.

“From listed here you just go on and generate any type of phishing scheme, even concentrating on Salesforce clients directly with these forms of e-mails. And the earlier mentioned will conclude up in the victim’s inbox, bypassing anti-spam and anti-phishing mechanisms, and even marked as Crucial by Google.”
Following dependable disclosure on June 28, 2023, Salesforce dealt with the zero-day as of July 28, 2023, with new checks that avert the use of email addresses from the @salesforce.com area.
The improvement arrives as Cofense warned of greater phishing exercise that employs Google Accelerated Cell Webpages (AMP) URLs to bypass security checks and carry out credential theft.
“The prevalence of phishing attacks and ripoffs remains high, with lousy actors continuously testing the limitations of email distribution infrastructure and current security measures,” the researchers said.
“A about element of this ongoing fight is the exploitation of seemingly genuine products and services, such as CRMs, advertising and marketing platforms, and cloud-centered workspaces, to have out destructive actions.”
Uncovered this write-up attention-grabbing? Adhere to us on Twitter and LinkedIn to examine much more distinctive written content we put up.
Some pieces of this report are sourced from:
thehackernews.com

 Top Industries Significantly Impacted by Illicit Telegram Networks
Top Industries Significantly Impacted by Illicit Telegram Networks