Lively Directory (Advertisement) is a strong authentication and listing assistance applied by corporations around the world. With this ubiquity and electric power arrives the prospective for abuse. Insider threats present some of the most potentials for destruction. A lot of interior customers have in excess of-provisioned obtain and visibility into the internal network.
Insiders’ degree of accessibility and believe in in a network potential customers to one of a kind vulnerabilities. Network security generally focuses on trying to keep a menace actor out, not on current users’ security and probable vulnerabilities. Remaining on leading of possible threats suggests defending against inside and outdoors threats.
Active Directory Vulnerabilities
From the outside, a properly configured Ad area gives a secure authentication and authorization alternative. But with intricate social engineering and phishing email attacks, an present Advertisement person can develop into compromised. As soon as inside of, danger actors have many choices to attack Energetic Directory.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Insecure Units
With “Provide Your Possess Product” (BYOD) increasing, there is greater system aid and security complexity. If consumers connect a product that is previously compromised or has inadequate security measures, attackers have a very simple way to gain access to the inner network.
In the past, an attacker would have to sneak in to set up a destructive machine. Now, having said that, a person with a compromised machine does the difficult work for them. Moreover, lots of workers may also join their smartphones or tablets to the network. This usually means that, rather of a solitary work-issued laptop computer, you may perhaps have two or three user equipment that are not issue to the very same security actions.
Over-Provisioned Obtain
Introducing complexity to interior security is the typical issue of about-provisioned obtain. Companies normally have a tendency to expand accessibility in its place of proscribing it. A single act of advantage to clear up a trouble can have the unintended consequence of generating a opportunity attack vector, which is then typically forgotten.
For those customers that are also directors, there is not usually a hugely secure “Administrative” account established to separate the distinct accessibility degrees. In this way, the advantage of allowing Administrative duties by way of a standard user account opens the door to rampant abuse thanks to a compromised and really privileged account.
Weak Password Procedures
Quite a few businesses, specifically greater ones, may possibly have weaker password guidelines thanks to the numerous apps they aid. Not all applications are the similar, and some do not support the hottest security criteria. Illustrations of this contain those people that do not assistance LDAP signing or TLS in excess of LDAP with LDAPS.
A weak password coverage coupled with a deficiency of multi-factor authentication would make it straightforward to crack a retrieved hash by means of a method these types of as Keberoasting by using a privileged inside account. This is in stark distinction to a potent password coverage and multi-factor authentication, which helps make it a great deal tougher to get accessibility to a process or network by cracking a hash.
Ideal Tactics for Securing Energetic Directory
To safe Active Listing, there are lots of finest methods to adhere to. Dependent on the beforehand outlined security themes, listed here are various:
- Prohibit access to devices and networks to those people with a respectable business enterprise need to have.
- Be certain connected gadgets satisfy a minimum regular of security.
- Configure Lively Listing securely with LDAP signing and LDAPS specifications, often rotate the KRBTGT password and use team-managed assistance accounts (gMSA) to rotate provider account qualifications.
- Enable multi-factor authentication and a strong password plan, augmented by alternatives such as Specops Password Policy.
- Separate permissions from the common person account and assign them to distinctive administrative accounts.
- Guarantee that customers know the hazards of phishing e-mails and social engineering, these types of as clicking on attachments.
Instruction end users to recognize likely phishing e-mail and social engineering attacks is vital. On top of that, people need to be discouraged from clicking on any attachments, and organizations must use programs that scan for malicious information. These steps can assist to cut down the risk of a prosperous attack.
But, suppose that Advertisement has previously been compromised. An organization can and must consider an in-depth look into the permissions assigned to lively and non-energetic or decommissioned buyers and devices. Are there approaches to independent permissions from normal person accounts and assign them to special administrative accounts with a better security level?
Enabling multi-factor authentication with a solid password policy is important for developing some of the strongest protections obtainable. As many social engineering attacks count on understanding and compromising a user’s external websites in which a reused password could present a foothold, an group will have to mandate sturdy passwords.
Retaining Lively Directory Secure with Specops Password Policy
Underpinning a lot of of the security recommendations is a potent password plan. The default Lively Directory configurations and consumer tools are insufficient. To guarantee people comply with password guidelines such as NIST, CJIS, and PCI, and block weak passwords, companies can use Specops Password Plan. It offers your firm the ability to produce personalized dictionary lists and block user names, exhibit names, certain phrases, consecutive figures, incremental passwords, and reusing a element of the latest password when giving serious-time comments for consumers.
The Breached Password Protection add-on further more enhances security by alerting users in actual-time if their chosen password is on a checklist of breached passwords. It also offers in-depth scanning to detect more than 3 billion compromised passwords on accounts throughout an Ad domain.
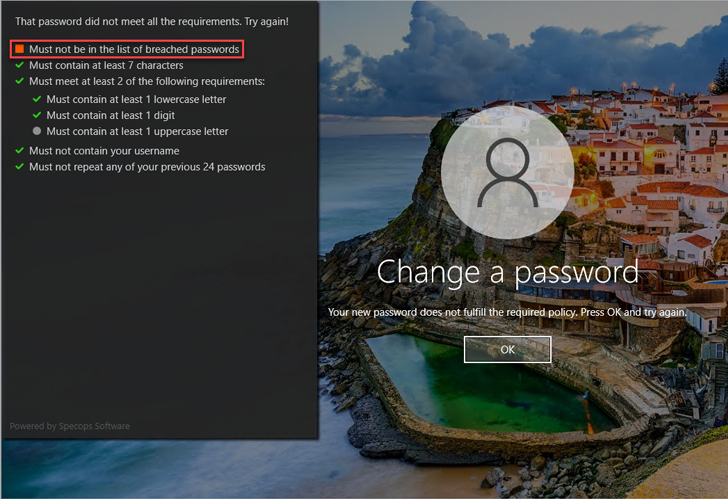 Source
Source
Shielding Lively Listing from Insider Threats
Though it might be impossible to shield versus every menace, by taking in-depth looks into current authorization constructions, energetic users, and the technical implementation of Energetic Directory, an organization can go a very long way to securing its environment. With Specops Password Coverage, take your password coverage to the upcoming amount as a result of Breached Password Defense and mandating distinctive and secure passwords throughout the board.
Uncovered this posting attention-grabbing? Observe us on Twitter and LinkedIn to read additional exclusive content material we submit.
Some pieces of this posting are sourced from:
thehackernews.com


 Security Researchers Spot $36m BEC Attack
Security Researchers Spot $36m BEC Attack