Threat actors have been noticed leveraging the QEMU open-source components emulator as tunneling application through a cyber attack focusing on an unnamed “big organization” to hook up to their infrastructure.
Though a number of respectable tunneling resources like Chisel, FRP, ligolo, ngrok, and Plink have been employed by adversaries to their benefit, the improvement marks the very first QEMU that has been utilized for this intent.
“We discovered that QEMU supported connections involving digital machines: the -netdev possibility creates network units (backend) that can then join to the digital devices,” Kaspersky scientists Grigory Sablin, Alexander Rodchenko, and Kirill Magaskin mentioned.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“Every single of the a lot of network products is defined by its variety and supports added solutions.”

In other words and phrases, the plan is to build a virtual network interface and a socket-type network interface, therefore letting the virtual equipment to converse with any remote server.
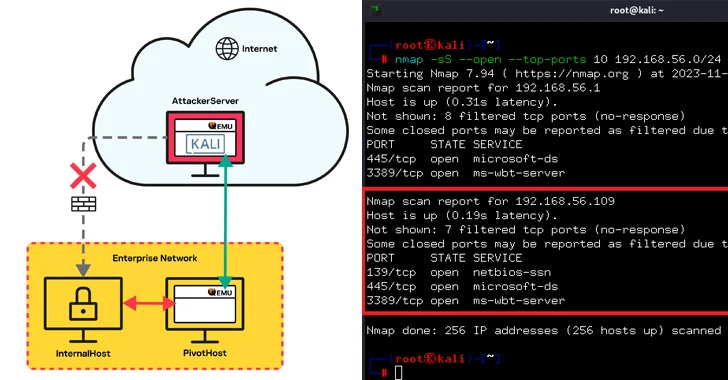
The Russian cybersecurity organization claimed it was able to use QEMU to established up a network tunnel from an inner host in just the business network that didn’t have internet entry to a pivot host with internet entry, which connects to the attacker’s server on the cloud running the emulator.

The results exhibit that threat actors are constantly diversifying their attack procedures to mix their destructive targeted traffic with true action and fulfill their operational objectives.
“Destructive actors applying legitimate tools to accomplish several attack methods is nothing at all new to incident reaction professionals,” the scientists reported.
“This more supports the notion of multi-degree safety, which handles both of those responsible endpoint security, and specialised remedies for detecting and shielding from elaborate and targeted attacks including human-operated kinds.”
Found this post interesting? Comply with us on Twitter and LinkedIn to examine additional special material we article.
Some sections of this write-up are sourced from:
thehackernews.com

 CISA Warns of Actively Exploited JetBrains TeamCity Vulnerability
CISA Warns of Actively Exploited JetBrains TeamCity Vulnerability