Taiwanese enterprise QNAP has rolled out fixes for a set of medium-severity flaws impacting QTS and QuTS hero, some of which could be exploited to accomplish code execution on its network-connected storage (NAS) appliances.
The issues, which effects QTS 5.1.x and QuTS hero h5.1.x, are shown down below –
- CVE-2024-21902 – An incorrect authorization assignment for critical resource vulnerability that could enable authenticated end users to read through or modify the resource through a network
- CVE-2024-27127 – A double free vulnerability that could make it possible for authenticated customers to execute arbitrary code via a network
- CVE-2024-27128, CVE-2024-27129, and CVE-2024-27130 – A set of buffer overflow vulnerabilities that could make it possible for authenticated buyers to execute arbitrary code by means of a network
All the shortcomings, that require a valid account on NAS gadgets, have been resolved in QTS 5.1.7.2770 establish 20240520 and QuTS hero h5.1.7.2770 make 20240520. Aliz Hammond of watchTowr Labs has been credited with identifying and reporting the flaws on January 3, 2024.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

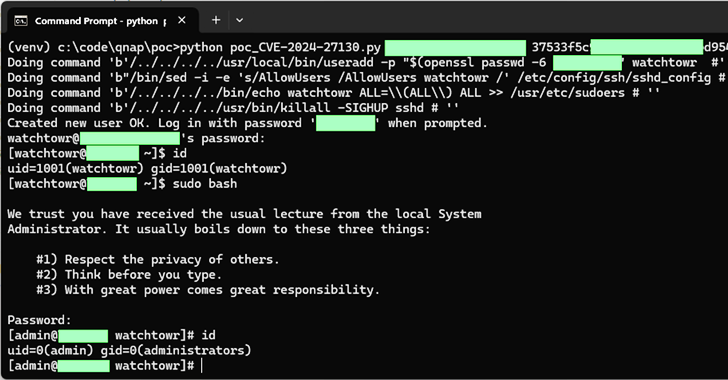
“The CVE-2024-27130 vulnerability, which has been noted less than WatchTowr ID WT-2023-0054, is induced by the unsafe use of the ‘strcpy’ functionality in the No_Guidance_ACL operate, which is used by the get_file_size request in the share.cgi script,” QNAP stated.
“This script is used when sharing media with external buyers. To exploit this vulnerability, an attacker calls for a legitimate ‘ssid’ parameter, which is generated when a NAS consumer shares a file from their QNAP system.”
It also pointed out that all QTS 4.x and 5.x versions have Deal with House Layout Randomization (ASLR) enabled, creating it tricky for an attacker to exploit the vulnerability.
The patches arrived 4 times after the Singapore-dependent cybersecurity organization released specifics about a total of 15 vulnerabilities, together with 4 individual bugs that could be weaponized to bypass authentication and execute arbitrary code.

The vulnerabilities – tracked from CVE-2023-50361 as a result of CVE-2023-50364 – have been settled by QNAP on April 25, 2024, adhering to disclosure in December 2023.
It truly is really worth noting that the firm has yet to launch fixes for CVE-2024-27131, which has been explained by watchTowr as a scenario of “Log spoofing by means of x-forwarded-for [that] makes it possible for users to bring about downloads to be recorded as asked for from arbitrary supply location.”
QNAP said CVE-2024-27131 is not an genuine vulnerability but fairly a style option that necessitates a modify in the UI specifications inside of the QuLog Heart. This is anticipated to be remediated in QTS 5.2..
Information about four other vulnerabilities described by watchTowr are at the moment withheld, with three of them now below evaluation. The fourth issue has been assigned a CVE ID and will be fastened in the future release.

watchTowr stated it was compelled to go public with the flaws previous week right after QNAP unsuccessful to address them within just the stipulated 90-working day community disclosure period of time and that it was generous by supplying the company “many extensions” to give the enterprise plenty of time.
In reaction, QNAP explained it regretted the coordination issues, stating it is really committing to releasing fixes for superior- or critical-severity flaws inside 45 times. Fixes for medium-severity vulnerabilities will be launched inside of 90 days.
“We apologize for any inconvenience this may have caused and are dedicated to improving our security measures repeatedly,” it included. “Our target is to operate carefully with researchers globally to make sure the maximum excellent of security for our solutions.”
With vulnerabilities in QNAP NAS products exploited in the earlier by ransomware attackers, people are advised to the most up-to-date variations of QTS and QuTS hero as before long as doable to mitigate possible threats.
Located this report intriguing? Stick to us on Twitter and LinkedIn to examine much more exceptional material we publish.
Some components of this short article are sourced from:
thehackernews.com

 Zoom Adopts NIST-Approved Post-Quantum End-to-End Encryption for Meetings
Zoom Adopts NIST-Approved Post-Quantum End-to-End Encryption for Meetings