Shutterstock
QNAP customers have been encouraged that cyber attackers are targeting its network-hooked up storage (NAS) merchandise with ransomware and have been encouraged to secure their devices at the earliest prospect.
Ransomware and brute-pressure cyber attacks have been “commonly focusing on” QNAP’s internet-going through NAS items, according to the producer which revealed a goods security statement on Friday.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
NAS drives that are uncovered to the internet with no any protection are specially susceptible to the attacks and end users are encouraged to revisit their security settings to be certain products are sufficiently safeguarded.
The scale of attacks is now unclear and QNAP also did not specify what strain of ransomware the attackers are working with, or where the attackers are primarily based. IT Pro has contacted QNAP for extra comment.
QNAP
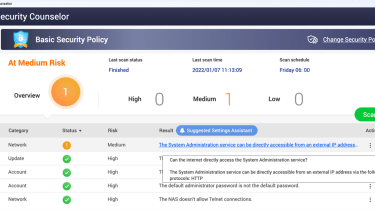
To examine if a NAS generate is susceptible to the attacks QNAP has observed, customers need to open up the QNAP Security Counselor on their NAS products and solutions. The NAS is at substantial risk if there is an artefact that reads: ‘The Technique Administration services can be specifically available from an exterior IP deal with by means of the adhering to protocols: HTTP’ on the dashboard. QNAP also has a guideline for customers on how to examine which ports on a router are exposed to the internet.
Securing the NAS
QNAP
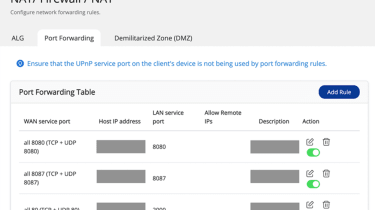
The 1st step to thoroughly secure vulnerable goods from the ongoing attacks is to disable the port forwarding purpose of the router. This can be completed via the administration interface of a user’s router. Users need to check out their configurations and disable the port forwarding environment of NAS administration service port which is established at port 8080 and 433 by default.
QNAP
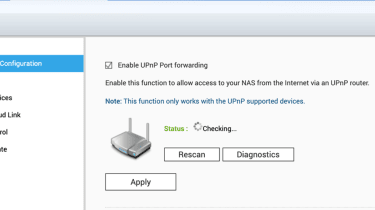
Users should lastly disable the common plug and engage in (UPnP) perform of their QNAP NAS product in the QTS menu in myQNAPcloud. To do this, end users can navigate to the ‘Auto Route Configuration’ tab in the QTS menu and unselect ‘Enable UPnP Port forwarding’.
Some components of this post are sourced from:
www.itpro.co.uk


 FlexBooker Reveals Major Customer Data Breach
FlexBooker Reveals Major Customer Data Breach