Cybersecurity companies in the US and United kingdom yesterday issued a joint advisory about a enormous ongoing malware menace infecting Taiwanese corporation QNAP’s network-hooked up storage (NAS) appliances.
Identified as QSnatch (or Derek), the facts-stealing malware is claimed to have compromised 62,000 equipment given that reports emerged very last Oct, with a higher degree of infection in Western Europe and North America.
“All QNAP NAS products are likely susceptible to QSnatch malware if not up to date with the most current security fixes,” the US Cybersecurity and Infrastructure Security Company (CISA) and the UK’s Countrywide Cyber Security Centre (NCSC) stated in the notify.
“Further more, once a device has been contaminated, attackers can protect against administrators from successfully running firmware updates.”
The manner of compromise, i.e., the an infection vector, continue to stays unclear, but CISA and NCSC stated the 1st campaign possible began in 2014 and ongoing until mid-2017 prior to intensifying in excess of the final few months to infect about 7,600 devices in the US and approximately 3,900 products in the Uk.
More than 7,000 NAS equipment were focused with the malware in Germany alone, according to the German Laptop or computer Unexpected emergency Reaction Crew (CERT-Bund) as of Oct 2019.
Though the infrastructure applied by the lousy actors in both campaigns is not now energetic, the 2nd wave of attacks requires injecting the malware for the duration of the infection phase and subsequently utilizing a area era algorithm (DGA) to set up a command-and-regulate (C2) channel for distant communication with the infected hosts and exfiltrate delicate facts.
“The two strategies are distinguished by the first payload made use of as very well as some variances in capabilities,” the companies mentioned.
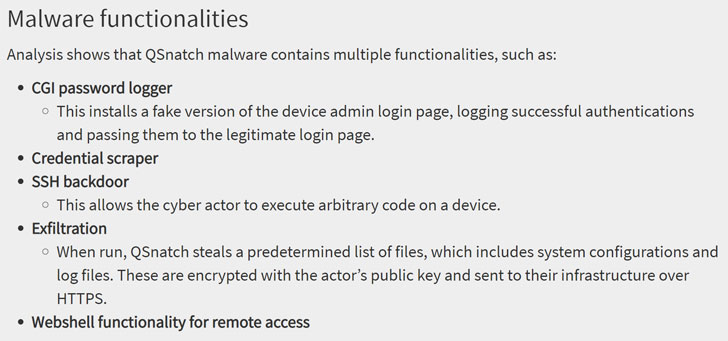
The hottest version of QSnatch arrives with a broad array of attributes, together with a CGI password logger that utilizes a phony admin login monitor to seize passwords, a credential scraper, an SSH backdoor able of executing arbitrary code, and a web shell operation to access the system remotely.
In addition, the malware gains persistence by blocking updates from having put in on the contaminated QNAP unit, which is finished by “redirecting core domain names utilized by the NAS to nearby out-of-day variations so updates can by no means be installed.”
The two companies have urged organizations to be certain their units have not been previously compromised, and if so, operate a whole factory reset on the system just before doing the firmware improve. It is also recommended to adhere to QNAP’s security advisory to prevent the infection by adhering to the actions shown here.
“Validate that you bought QNAP devices from reliable resources,” CISA and NCSC instructed as part of extra mitigation in opposition to QSnatch. “Block external connections when the gadget is supposed to be utilized strictly for inside storage.”
Found this article intriguing? Adhere to THN on Facebook, Twitter and LinkedIn to examine much more distinctive material we submit.


 Dave ShinyHunters hack exposes 7.5 million user information
Dave ShinyHunters hack exposes 7.5 million user information