Ransomware actors and cryptocurrency scammers have joined nation-point out actors in abusing cloud mining providers to launder digital property, new findings expose.
“Cryptocurrency mining is a important part of our industry, but it also holds particular charm to undesirable actors, as it supplies a implies to purchase dollars with a thoroughly thoroughly clean on-chain unique supply,” blockchain analytics business Chainalysis explained in a report shared with The Hacker Information.
Earlier this March, Google Mandiant disclosed North Korea-based mostly APT43’s use of the hash rental and cloud mining products and services to obscure the forensic trail and wash the stolen cryptocurrency “clean.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

Cloud mining products and services let end users to hire a personal computer program and use that computer’s hash electric power to mine cryptocurrencies with no getting to manage the mining hardware themselves.
But according to Chainalysis, it can be not just country-point out hacking crews who are leveraging such expert services in the wild.
In one illustration highlighted by the corporation, mining swimming pools and wallets related with ransomware actors have been employed to ship money to a “extremely active deposit deal with” at an unnamed mainstream crypto trade.
This contains $19.1 million from 4 ransomware wallet addresses and $14.1 million from three mining swimming pools, with a considerable chunk of the cash routed by using a network of intermediary wallets and pools.
“In this circumstance, the mining pool functions likewise to a mixer in that it obfuscates the origin of cash and results in the illusion that the cash are proceeds from mining fairly than from ransomware,” Chainalysis mentioned.
In a sign that the trend is attaining traction, the cumulative value of property despatched from ransomware wallets to exchanges by mining pools has surged from significantly less than $10,000 in Q1 2018 to pretty much $50 million in Q1 2023.
Future WEBINAR🔐 Mastering API Security: Being familiar with Your True Attack Surface area
Learn the untapped vulnerabilities in your API ecosystem and consider proactive steps towards ironclad security. Be a part of our insightful webinar!
Be part of the Session.wn-button,.wn-label,.wn-label:right afterexhibit:inline-block.check_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px reliable #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-major-left-radius:25px-moz-border-radius-topleft:25px-webkit-border-base-proper-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-dimension:13pxmargin:20px 0font-fat:600letter-spacing:.6pxcolor:#596cec.wn-label:soon afterwidth:50pxheight:6pxcontent:”border-major:2px strong #d9deffmargin: 8px.wn-titlefont-sizing:21pxpadding:10px 0font-fat:900textual content-align:leftline-peak:33px.wn-descriptiontextual content-align:leftfont-sizing:15.6pxline-top:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-colour:#4469f5font-size:15pxcolor:#fff!importantborder:0line-peak:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-body weight:500letter-spacing:.2px
Which is not all. As many as 372 trade deposit addresses have been located to acquire at least $1 million value of cryptocurrency from mining swimming pools and any quantity from ransomware addresses considering the fact that January 2018.
“In general, the knowledge suggests that mining swimming pools may perhaps play a essential purpose in lots of ransomware actors’ funds laundering system,” Chainalysis reported.
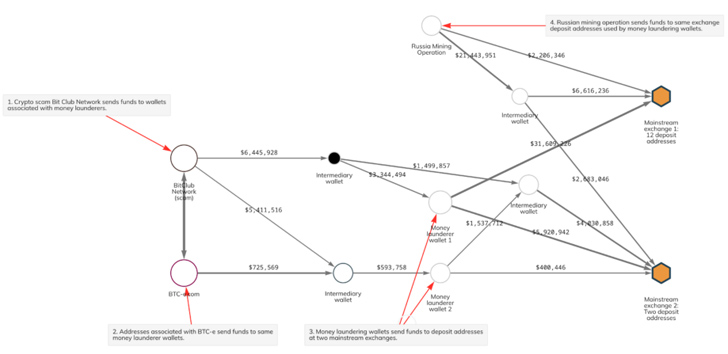
Mining swimming pools have also gained a put in the playbooks of fraud operators like the BitClub Network, who have been identified commingling their illicit Bitcoin proceeds with assets received from a Russia-primarily based Bitcoin mining operation and BTC-e, a crypto exchange that was established up to facilitate the laundering of cash stolen in the infamous Mt. Gox hack.
“Crypto scammers and money launderers functioning on their behalf are also applying mining swimming pools as component of their income laundering system,” the company said. “Deposit addresses [with receipts of at least $1 million worth of crypto from mining pools] have gained just under $1.1 billion worth of cryptocurrency from fraud-similar addresses given that 2018.”
Identified this write-up interesting? Abide by us on Twitter and LinkedIn to read through much more exclusive written content we put up.
Some pieces of this posting are sourced from:
thehackernews.com


 Study Reveals Ransomware as Most Popular Cybercrime Service
Study Reveals Ransomware as Most Popular Cybercrime Service