The Raspberry Robin worm is turning out to be an access-as-a-support malware for deploying other payloads, which includes IcedID, Bumblebee, TrueBot (aka Silence), and Clop ransomware.
It is “part of a complex and interconnected malware ecosystem, with inbound links to other malware people and alternate an infection approaches past its authentic USB push unfold,” the Microsoft Security Danger Intelligence Middle (MSTIC) mentioned in a detailed produce-up.
Raspberry Robin, also referred to as QNAP Worm owing to the use of compromised QNAP storage servers for command-and-handle, is the identify offered to a malware by cybersecurity enterprise Purple Canary that spreads to Windows techniques through infected USB drives.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
MSTIC is trying to keep tabs on the action group guiding the USB-based Raspberry Robin bacterial infections as DEV-0856, incorporating it truly is informed of at minimum four confirmed entry points that all have the probable end target of deploying ransomware.
The tech giant’s cybersecurity staff reported that Raspberry Robin has advanced from a broadly distributed worm with no observed publish-infection steps to a single of the major malware distribution platforms at this time energetic.
According to telemetry data collected from Microsoft Defender for Endpoint, about 3,000 units spanning nearly 1,000 corporations have encountered at minimum a person Raspberry Robin payload-related alert in the very last 30 days.
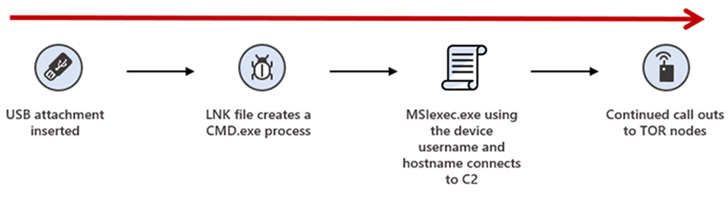
The most up-to-date progress provides to escalating proof of post-exploitation things to do linked to Raspberry Robin, which, in July 2022, was identified performing as a conduit to produce the FakeUpdates (aka SocGholish) malware.
This FakeUpdates exercise has also been adopted by pre-ransomware behavior attributed to a risk cluster tracked by Microsoft as DEV-0243 (aka Evil Corp), the infamous Russian cybercrime syndicate driving the Dridex trojan and a command-and-regulate (C2) framework known as TeslaGun.
Microsoft, in Oct 2022, reported it detected Raspberry Robin being used in article-compromise exercise attributed to a unique threat actor it has codenamed DEV-0950 and which overlaps with groups monitored publicly as FIN11 and TA505.
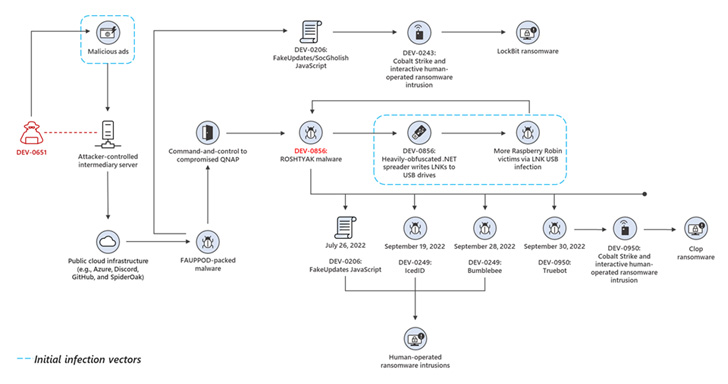
Even though the names FIN11 and TA505 have usually been used interchangeably, Google-owned Mandiant (previously FireEye) describes FIN11 as a subset of activity beneath the TA505 team.
It is really also worth pointing out the conflation of Evil Corp and TA505, although Proofpoint assesses “TA505 to be various than Evil Corp,” suggesting that these clusters share partial tactical commonalities with just one one more.

“From a Raspberry Robin infection, the DEV-0950 action led to Cobalt Strike arms-on-keyboard compromises, in some cases with a Truebot infection noticed in between the Raspberry Robin and Cobalt Strike phase,” the researcher mentioned. “The exercise culminated in deployments of the Clop ransomware.”
Microsoft also theorized that the actors at the rear of these Raspberry Robin-associated malware strategies are spending the worm’s operators for payload supply, enabling them to move away from phishing as a vector to purchase new victims.
What’s much more, a cybercriminal actor dubbed DEV-0651 has been linked to the distribution of another artifact called Fauppod through the abuse of genuine cloud providers, which displays code similarities to Raspberry Robin and also drops the FakeUpdates malware.
The Windows maker additional famous wih medium self confidence that Fauppod represents the earliest known url in the Raspberry Robin infection chain for propagating the latter through LNK files to USB drives.
To add to the attack puzzle, IBM Security X-Pressure, early past thirty day period, discovered purposeful similarities between a loader ingredient utilised in the Raspberry Robin infection chain and the Dridex malware. Microsoft is attributing this code-level relationship to Fauppod adopting Dridex’s approaches to keep away from execution in certain environments.
“Raspberry Robin’s an infection chain is a puzzling and intricate map of many infection points that can lead to a lot of distinct results, even in scenarios the place two hosts are contaminated at the same time,” Microsoft explained.
Located this short article attention-grabbing? Adhere to THN on Facebook, Twitter and LinkedIn to examine extra unique content material we article.
Some elements of this post are sourced from:
thehackernews.com


 Information security vs cyber security vs network security: What are the differences?
Information security vs cyber security vs network security: What are the differences?