A new menace actor acknowledged as AtlasCross has been observed leveraging Crimson Cross-themed phishing lures to supply two beforehand undocumented backdoors named DangerAds and AtlasAgent.
NSFOCUS Security Labs described the adversary as owning a “higher technical level and careful attack attitude,” incorporating that “the phishing attack activity captured this time is component of the attacker’s targeted strike on certain targets and is its principal suggests to accomplish in-domain penetration.”
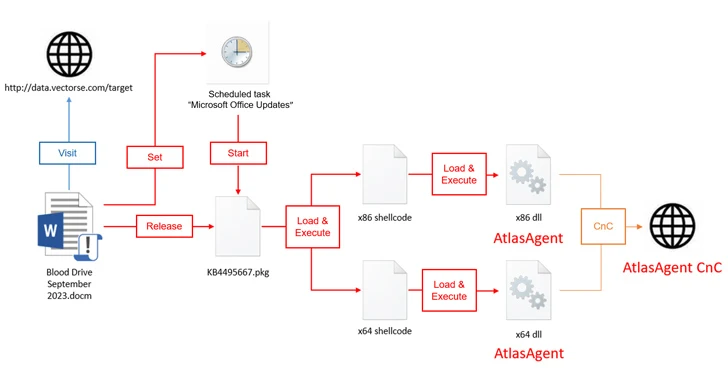
The attack chains start off with a macro-laced Microsoft doc that purports to be about a blood donation push from the American Crimson Cross that, when launched, operates the destructive macro to established up persistence, exfiltrate technique metadata to a distant server (information.vectorse[.]com) that’s a sub-domain of a reputable web page belonging to a structural and engineering organization primarily based in the U.S.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Future WEBINARFight AI with AI — Battling Cyber Threats with Next-Gen AI Instruments
Ready to tackle new AI-pushed cybersecurity troubles? Be part of our insightful webinar with Zscaler to tackle the rising menace of generative AI in cybersecurity.
Supercharge Your Skills
It also extracts a file named KB4495667.pkg (codenamed DangerAds), which, subsequently acts as a loader to launch shellcode that potential customers to the deployment of AtlasAgent, a C++ malware able of collecting procedure facts, shellcode operation, and running instructions to get a reverse shell as well as inject code into a thread in the specified system.
Both of those AtlasAgent and DangerAds include evasive capabilities to make it less likely to be uncovered by security resources.
AtlasCross is suspected to have breached general public network hosts by exploiting recognized security vulnerabilities and turning them into command-and-handle (C2) servers. NSFOCUS claimed it determined 12 distinctive compromised servers in the U.S.
The legitimate identification of AtlasCross and its backers now stays a puzzle.
“At this latest phase, AtlasCross has a relatively limited scope of activity, largely concentrating on qualified attacks from unique hosts within a network domain,” the enterprise mentioned. “On the other hand, the attack processes they employ are extremely strong and mature.”
Observed this write-up fascinating? Stick to us on Twitter and LinkedIn to read far more unique information we put up.
Some sections of this write-up are sourced from:
thehackernews.com

 Researchers Uncover a New GPU Side-Channel Vulnerability Leaking Sensitive Data
Researchers Uncover a New GPU Side-Channel Vulnerability Leaking Sensitive Data