The Russian-talking cybercrime group termed RedCurl is leveraging a respectable Microsoft Windows component called the Application Compatibility Assistant (PCA) to execute malicious commands.
“The Method Compatibility Assistant Provider (pcalua.exe) is a Windows company created to detect and address compatibility issues with older programs,” Pattern Micro reported in an evaluation released this thirty day period.
“Adversaries can exploit this utility to empower command execution and bypass security limits by utilizing it as an alternate command-line interpreter. In this investigation, the risk actor takes advantage of this resource to obscure their pursuits.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

RedCurl, which is also named Earth Kapre and Red Wolf, is known to be active considering that at least 2018, orchestrating company cyber espionage attacks from entities located in Australia, Canada, Germany, Russia, Slovenia, the U.K., Ukraine, and the U.S.
In July 2023, F.A.C.C.T. disclosed that a important Russian financial institution and an Australian corporation had been qualified by the risk actor in November 2022 and May possibly 2023 to pilfer confidential corporate secrets and personnel info.
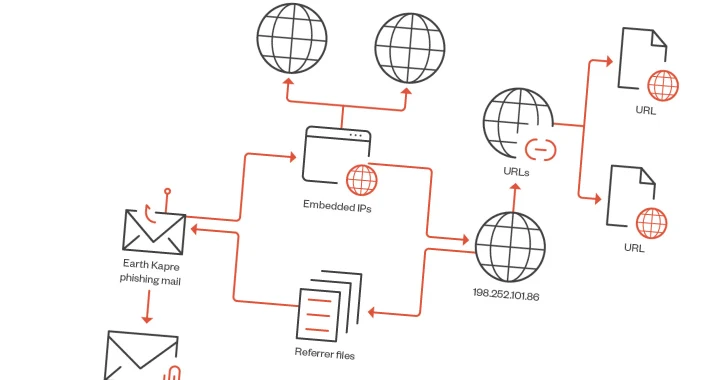
The attack chain examined by Craze Micro involves the use of phishing email messages containing malicious attachments (.ISO and .IMG documents) to activate a multi-phase approach that starts off with the use of cmd.exe to download a respectable utility referred to as curl from a distant server, which then functions as a channel to provide a loader (ms.dll or ps.dll).
The malicious DLL file, in convert, leverages PCA to spawn a downloader process that normally takes care of setting up a link with the exact domain utilized by curl to fetch the loader.
Also used in the attack is the use of the Impacket open up-source program for unauthorized command execution.
The connections to Earth Kapre stem from overlaps in the command-and-command (C2) infrastructure as perfectly as similarities with known downloader artifacts employed by the group.
“This case underscores the ongoing and energetic risk posed by Earth Kapre, a risk actor that targets a assorted variety of industries across a number of nations,” Development Micro reported.

“The actor employs sophisticated tactics, these kinds of as abusing PowerShell, curl, and Method Compatibility Assistant (pcalua.exe) to execute destructive instructions, showcasing its perseverance to evading detection inside qualified networks.”
The development comes as the Russian country-state team known as Turla (aka Iron Hunter, Pensive Ursa, Solution Blizzard, Snake, Uroburos, Venomous Bear, and Waterbug) has begun utilizing a new wrapper DLL codenamed Pelmeni to deploy the .NET-based mostly Kazuar backdoor.
Pelmeni – which masquerades as libraries similar to SkyTel, NVIDIA GeForce Encounter, vncutil, or ASUS – is loaded by means of DLL side-loading. At the time this spoofed DLL is called by the respectable computer software put in on the equipment, it decrypts and launches Kazuar, Lab52 mentioned.
Found this post attention-grabbing? Adhere to us on Twitter and LinkedIn to go through a lot more special information we article.
Some sections of this posting are sourced from:
thehackernews.com

 Ande Loader Malware Targets Manufacturing Sector in North America
Ande Loader Malware Targets Manufacturing Sector in North America