A complex stealer-as-a-ransomware menace dubbed RedEnergy has been noticed in the wild targeting electrical power utilities, oil, gas, telecom, and equipment sectors in Brazil and the Philippines via their LinkedIn web pages.
The malware “possesses the capacity to steal info from various browsers, enabling the exfiltration of delicate information, whilst also incorporating different modules for carrying out ransomware pursuits,” Zscaler scientists Shatak Jain and Gurkirat Singh claimed in a the latest evaluation.
The aim, the scientists observed, is to couple info theft with encryption with the purpose of inflicting most hurt to the victims.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The starting off point for the multi-stage attack is a FakeUpdates (aka SocGholish) marketing campaign that tricks consumers into downloading JavaScript-based malware under the guise of web browser updates.
What will make it novel is the use of dependable LinkedIn web pages to concentrate on victims, redirecting buyers clicking on the site URLs to a bogus landing site that prompts them to update their web browsers by clicking on the suitable icon (Google Chrome, Microsoft Edge, Mozilla Firefox, or Opera), doing so which outcomes in the down load a destructive executable.
Pursuing a thriving breach, the malicious binary is employed as a conduit to set up persistence, perform the genuine browser update, and also fall a stealer capable of covertly harvesting sensitive details and encrypting the stolen information, leaving the victims at risk of probable knowledge decline, publicity, or even the sale of their precious info.
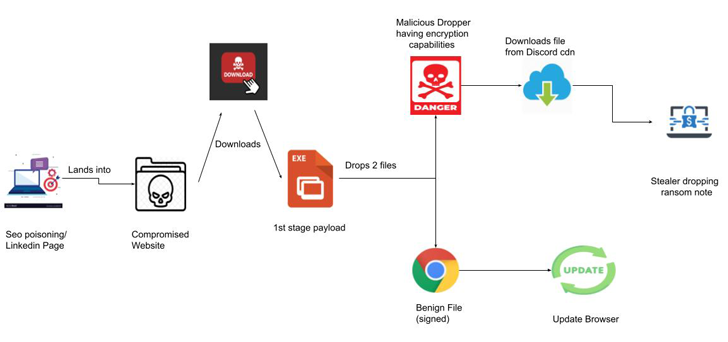
Zscaler mentioned it discovered suspicious interactions having location over a File Transfer Protocol (FTP) connection, increasing the likelihood that beneficial information is getting exfiltrated to actor-managed infrastructure.
In the ultimate phase, RedEnergy’s ransomware part proceeds to encrypt the user’s knowledge, suffixing the “.FACKOFF!” extension to each and every encrypted file, deleting current backups, and dropping a ransom observe in each individual folder.
Upcoming WEBINAR🔐 Privileged Accessibility Management: Study How to Conquer Essential Problems
Learn distinct methods to conquer Privileged Account Management (PAM) difficulties and degree up your privileged obtain security tactic.
Reserve Your Place
Victims are expected to make a payment of .005 BTC (about $151) to a cryptocurrency wallet described in the note to regain obtain to the files. RedEnergy’s twin features as a stealer and ransomware symbolize an evolution of the cybercrime landscape.
The improvement also follows the emergence of a new RAT-as-a-ransomware risk category in which distant obtain trojans these as Venom RAT and Anarchy Panel RAT have been geared up with ransomware modules to lock many file extensions guiding encryption barriers.
“It is essential for persons and businesses to training utmost warning when accessing internet websites, primarily those connected from LinkedIn profiles,” the researchers claimed. “Vigilance in verifying the authenticity of browser updates and being cautious of unpredicted file downloads is paramount to shield versus these kinds of destructive campaigns.”
Found this short article fascinating? Comply with us on Twitter and LinkedIn to read much more exclusive material we post.
Some parts of this post are sourced from:
thehackernews.com

 Secrets, Secrets Are No Fun. Secrets, Secrets (Stored in Plain Text Files) Hurt Someone
Secrets, Secrets Are No Fun. Secrets, Secrets (Stored in Plain Text Files) Hurt Someone