Ransomware groups are more and more switching to distant encryption in their attacks, marking a new escalation in techniques adopted by fiscally inspired actors to assure the good results of their strategies.
“Companies can have hundreds of desktops connected to their network, and with remote ransomware, all it can take is 1 underprotected product to compromise the full network,” Mark Loman, vice president of risk study at Sophos, said.
“Attackers know this, so they hunt for that one’ weak spot’ — and most companies have at least one. Distant encryption is going to keep a perennial difficulty for defenders.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
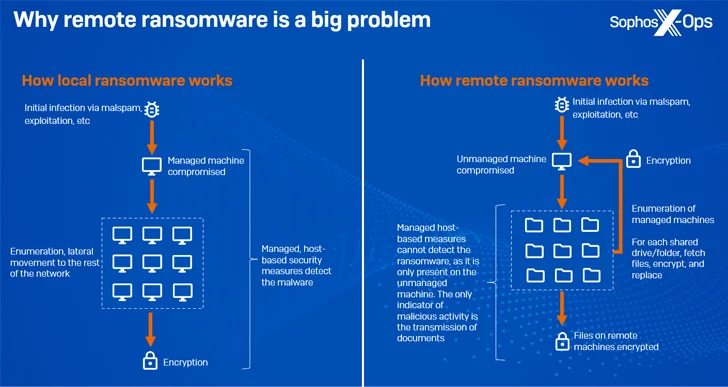
Remote encryption (aka distant ransomware), as the title implies, occurs when a compromised endpoint is applied to encrypt details on other units on the same network.
Impending WEBINAR Beat AI-Run Threats with Zero Rely on – Webinar for Security Industry experts
Conventional security actions will never slice it in modern earth. It truly is time for Zero Belief Security. Safe your information like never ever ahead of.
Sign up for Now
In October 2023, Microsoft unveiled that around 60% of ransomware attacks now involve malicious distant encryption in an effort and hard work to lessen their footprint, with extra than 80% of all compromises originating from unmanaged devices.
“Ransomware households identified to guidance distant encryption consist of Akira, ALPHV/BlackCat, BlackMatter, LockBit, and Royal, and it can be a procedure which is been all over for some time – as much back as 2013, CryptoLocker was targeting network shares,” Sophos mentioned.
A substantial advantage to this technique is that it renders system-centered remediation steps ineffective and the managed equipment can not detect the destructive activity given that it is only current in an unmanaged product.
The advancement will come amid broader shifts in the ransomware landscape, with the risk actors adopting atypical programming languages, focusing on outside of Windows programs, auctioning stolen info, and launching attacks just after business hrs and at weekends to thwart detection and incident reaction endeavours.
Sophos, in a report revealed final week, highlighted the “symbiotic – but frequently uneasy – connection” between ransomware gangs and the media, as a way to not only draw in consideration, but also to regulate the narrative and dispute what they perspective as inaccurate protection.
This also extends to publishing FAQs and press releases on their information leak sites, even such as immediate estimates from the operators, and correcting issues produced by journalists. An additional tactic is the use of catchy names and slick graphics, indicating an evolution of the professionalization of cyber crime.

“The RansomHouse team, for illustration, has a concept on its leak web site exclusively aimed at journalists, in which it offers to share info on a ‘PR Telegram channel’ prior to it is officially released,” Sophos observed.
Whilst ransomware groups like Conti and Pysa are known for adopting an organizational hierarchy comprising senior executives, procedure admins, builders, recruiters, HR, and authorized groups, there is proof to counsel that some have advertised options for English writers and speakers on criminal boards.
“Media engagement offers ransomware gangs with both tactical and strategic pros it permits them to use stress to their victims, whilst also enabling them to form the narrative, inflate their individual notoriety and egos, and more ‘mythologize’ themselves,” the business claimed.
Identified this post attention-grabbing? Comply with us on Twitter and LinkedIn to go through additional unique material we submit.
Some elements of this short article are sourced from:
thehackernews.com


 Product Explained: Memcyco’s Real-Time Defense Against Website Spoofing
Product Explained: Memcyco’s Real-Time Defense Against Website Spoofing