Threat actors are utilizing an open up-resource rootkit referred to as Reptile to concentrate on Linux systems in South Korea.
“Not like other rootkit malware that ordinarily only deliver concealment abilities, Reptile goes a action further by providing a reverse shell, allowing for threat actors to quickly take control of programs,” the AhnLab Security Crisis Reaction Middle (ASEC) reported in a report released this week.
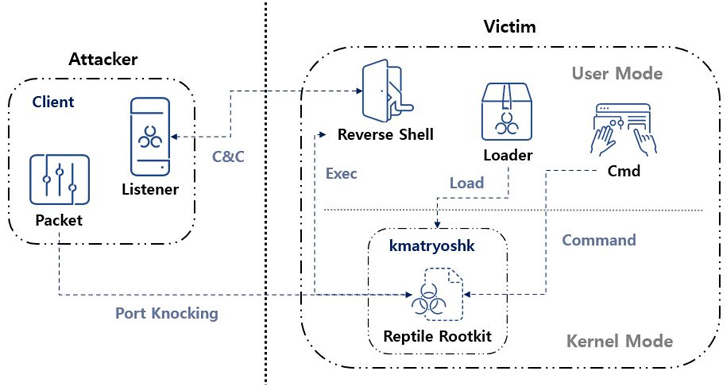
“Port knocking is a method wherever the malware opens a distinct port on an contaminated technique and goes on standby. When the threat actor sends a magic packet to the program, the gained packet is used as a foundation to build a link with the C&C server.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
A rootkit is a malicious software package software that is designed to provide privileged, root-degree accessibility to a device although concealing its presence. At the very least four different campaigns have leveraged Reptile considering that 2022.

The to start with use of the rootkit was recorded by Development Micro in May possibly 2022 in link with an intrusion set tracked as Earth Berberoka (aka GamblingPuppet), which has been discovered to use the malware to disguise connections and procedures associated to a cross-platform Python trojan acknowledged as Pupy RAT in attacks aimed at gambling web-sites in China.
Then in March 2023, Google-owned Mandiant thorough a established of attacks mounted by a suspected China-joined threat actor dubbed UNC3886 that used zero-working day flaws in Fortinet appliances to deploy a range of personalized implants as properly as Reptile.
ExaTrack, that identical thirty day period, exposed a Chinese hacking group’s use of a Linux malware termed Mélofée which is centered on Reptile. Lastly, in June 2023, a cryptojacking procedure uncovered by Microsoft applied a shell script backdoor to download Reptile in purchase to obscure its boy or girl procedures, documents, or their written content.
A nearer assessment of Reptile reveals the use of a loader, which employs a device termed kmatryoshka to decrypt and load the rootkit’s kernel module into memory, just after which it opens a distinct port and awaits for the attacker to transmit a magic packet to the host around protocols these types of as TCP, UDP, or ICMP.

“The information acquired by the magic packet consists of the C&C server address,” ASEC said. “Centered on this, a reverse shell connects to the C&C server.”
It’s value noting that the use of magic packets to activate the destructive action has been noticed previously in a different rootkit named Syslogk, which was documented by Avast previous calendar year.
The South Korean cybersecurity company reported it also detected an attack case in the place that associated the use of Reptile, while bearing some tactical similarities to Mélofée.
“Reptile is a Linux kernel method rootkit malware that offers a concealment feature for files, directories, procedures, and network communications,” ASEC reported. “Nonetheless, Reptile by itself also delivers a reverse shell, making systems with Reptile mounted vulnerable to staying hijacked by danger actors.”
Uncovered this posting fascinating? Follow us on Twitter and LinkedIn to examine additional distinctive content material we article.
Some parts of this article are sourced from:
thehackernews.com


 Microsoft Addresses Critical Power Platform Flaw After Delays and Criticism
Microsoft Addresses Critical Power Platform Flaw After Delays and Criticism