An ongoing examination into an up-and-coming cryptocurrency mining botnet known as KmsdBot has led to it getting unintentionally taken down.
KmsdBot, as christened by the Akamai Security Intelligence Response Group (SIRT), came to gentle mid-November 2022 for its capability to brute-force systems with weak SSH credentials.
The botnet strikes the two Windows and Linux equipment spanning a large selection of microarchitectures with the principal aim of deploying mining software program and corralling the compromised hosts into a DDoS bot.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

Some of the significant targets involved gaming corporations, technology companies, and luxurious motor vehicle companies.
Akamai researcher Larry W. Cashdollar, in a new update, spelled out how instructions despatched to the bot to recognize its operation in a controlled setting inadvertently neutralized the malware.
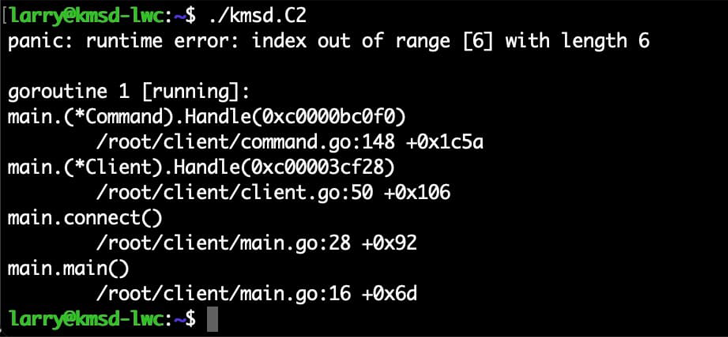
“Curiously, right after just one solitary improperly formatted command, the bot stopped sending instructions,” Cashdollar reported. “It truly is not just about every day you come throughout a botnet that the danger actors on their own crash their very own handiwork.”
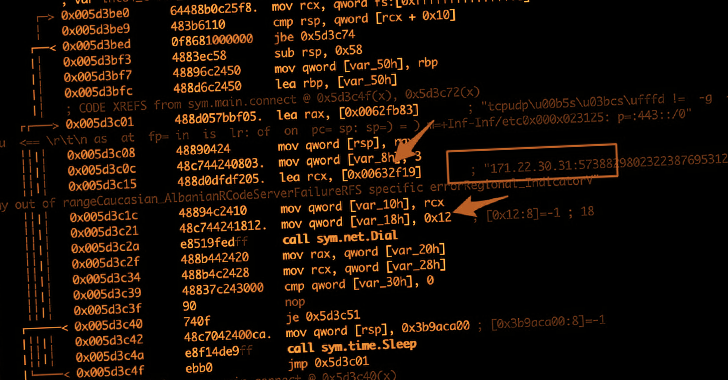
This, in turn, was built attainable owing to the deficiency of an error-checking mechanism crafted into the source code to validate the gained instructions.
Especially, an instruction issued devoid of a room involving the concentrate on web-site and the port brought about the total Go binary running on the infected machine to crash and stop interacting with its command-and-regulate server, correctly killing the botnet.
The point that KmsdBot isn’t going to have a persistence mechanism also signifies that the malware operator will have to re-infect the machines once more and re-establish the infrastructure from scratch.
“This botnet has been likely right after some pretty massive luxury brands and gaming organizations, and still, with 1 failed command it simply cannot continue,” Cashdollar concluded. “This is a powerful instance of the fickle mother nature of technology and how even the exploiter can be exploited by it.”
Found this post appealing? Observe us on Twitter and LinkedIn to browse extra exclusive content we write-up.
Some elements of this posting are sourced from:
thehackernews.com

 LastPass Reveals Another Customer Data Breach
LastPass Reveals Another Customer Data Breach