Cybersecurity researchers have disclosed facts of a now-patched bug in Box’s multi-factor authentication (MFA) system that could be abused to fully sidestep SMS-dependent login verification.
“Making use of this strategy, an attacker could use stolen credentials to compromise an organization’s Box account and exfiltrate delicate information with no accessibility to the victim’s phone,” Varonis researchers mentioned in a report shared with The Hacker News.
The cybersecurity firm explained it reported the issue to the cloud company provider on November 2, 2021, post which fixes were issued by Box.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

MFA is an authentication approach that relies on a mix of components this kind of as a password (anything only the person knows) and a short-term one particular-time password aka TOTP (anything only the consumer has) to offer people a next layer of defense towards credential stuffing and other account takeover attacks.
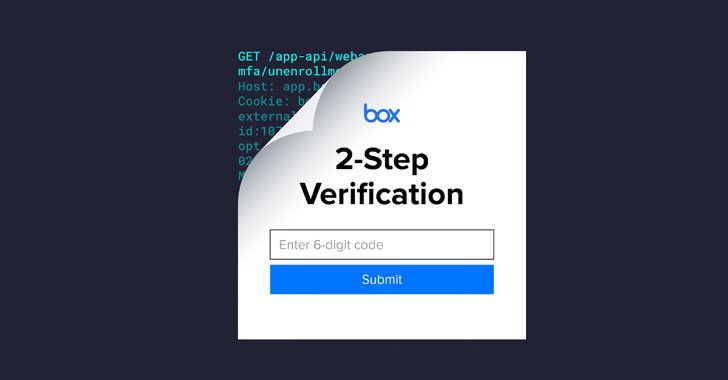
This two-action authentication can both require sending the code as an SMS or alternatively, accessed through an authenticator application or a components security essential. Thus, when a Box person who is enrolled for SMS verification logs in with a valid username and password, the support sets a session cookie and redirects the consumer to a webpage exactly where the TOTP can be entered to acquire obtain to the account.
The bypass determined by Varonis is a consequence of what the researchers called a mixup of MFA modes. It occurs when an attacker indications in with the victim’s qualifications and abandons the SMS-based mostly authentication in favor of a unique procedure that utilizes, say, the authenticator app to effectively finish the login merely by furnishing the TOTP linked with their possess Box account.
“Box misses that the sufferer hasn’t enrolled [in] an authenticator application, and as an alternative blindly accepts a valid authentication passcode from a fully unique account without having to start with examining that it belonged to the person that was logging in,” the scientists reported. “This created it achievable to entry the victim’s Box account with out accessing their phone or notifying the consumer by way of SMS.”
Place differently, Box not only did not check irrespective of whether the target was enrolled in an authenticator app-primarily based verification (or any other technique barring SMS), it also did not validate that the code entered is from an authenticator application which is truly connected to the target who is attempting to log in.
The findings occur a small over a month immediately after Varonis disclosed a very similar strategy that could empower malicious actors to get all over authenticator-centered verification by “unenroll[ing] a person from MFA right after providing a username and password but ahead of delivering the next factor.”
“The /mfa/unenrollment endpoint did not demand the consumer to be fully authenticated in order to eliminate a TOTP system from a user’s account,” the researchers famous in early December 2021.
“MFA is only as good as the developer producing the code [and] can deliver a untrue feeling of security,” the scientists concluded. “Just because MFA is enabled does not essentially imply an attacker need to get bodily obtain to a victim’s gadget to compromise their account.”
Discovered this posting appealing? Abide by THN on Facebook, Twitter and LinkedIn to read additional distinctive articles we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Organizations Face a ‘Losing Battle’ Against Vulnerabilities
Organizations Face a ‘Losing Battle’ Against Vulnerabilities