Substantial-severity security vulnerabilities have been disclosed in different endpoint detection and reaction (EDR) and antivirus (AV) merchandise that could be exploited to switch them into information wipers.
“This wiper runs with the permissions of an unprivileged consumer still has the means to wipe pretty much any file on a program, such as method documents, and make a computer totally unbootable,” SafeBreach Labs researcher Or Yair mentioned. “It does all that with no implementing code that touches the focus on files, generating it entirely undetectable.”
EDR computer software, by structure, are capable of continually scanning a device for probably suspicious and malicious data files, and getting proper motion, these types of as deleting or quarantining them.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The plan, in a nutshell, is to trick vulnerable security items into deleting respectable data files and directories on the process and render the equipment inoperable by building use of specifically crafted paths.

This is reached by using advantage of what is actually termed a junction place (aka gentle url), where a directory serves as an alias to yet another listing on the pc.
Place in different ways, between the window the EDR program identifies a file as malicious and attempts to delete the file from the method, the attacker uses a junction to position the software program in direction of a different path, like C: generate.
The strategy, however, failed to result in a wipe as EDRs prevented further accessibility to a file right after it was flagged as malicious. What is actually more, really should the rogue file be deleted by the person, the software was intelligent enough to detect the deletion and quit by itself from acting on it.
The final option arrived in the form of a wiper resource, dubbed Aikido, that triggers the privileged delete by building a destructive file at a decoy directory and not granting it any permission, resulting in the EDRs to postpone the delete right up until following reboot.
Given this new attack interval, all an adversary has to do is delete the listing containing the rogue file, produce a junction to place to the focus on directory to be deleted, and reboot the process.
Prosperous weaponization of the procedure could end result in the deletion of procedure documents like motorists, blocking the functioning process from booting. It can also be abused to get rid of all information from administrator user directories.
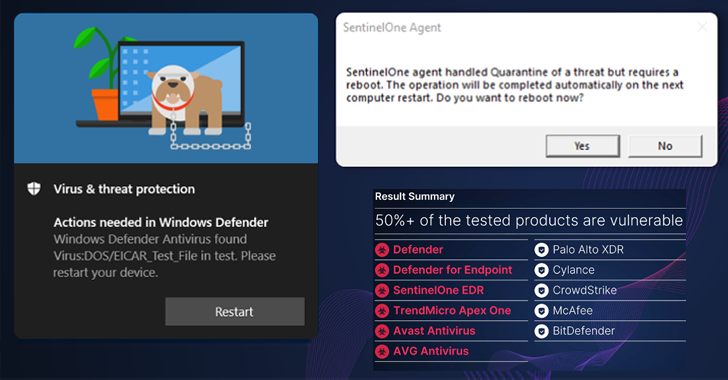
Out of 11 security products and solutions that were being examined, six had been found susceptible to the zero-day wiper exploit, prompting the distributors to launch updates to handle the shortcoming –
- CVE-2022-37971 (CVSS rating: 7.1) – Microsoft Defender and Defender for Endpoint
- CVE-2022-45797 (CVSS score: N/A) – Craze Micro Apex One
- CVE-2022-4173 (CVSS score: 8.8) – Avast and AVG Antivirus
“The wiper executes its malicious actions employing the most reliable entity on the program — the EDR or AV,” Yair said. “EDRs and AVs do not protect against by themselves from deleting files.”
Discovered this posting attention-grabbing? Comply with us on Twitter and LinkedIn to go through extra unique content material we submit.
Some sections of this article are sourced from:
thehackernews.com

 Chaos RAT Used to Enhance Linux Cryptomining Attacks
Chaos RAT Used to Enhance Linux Cryptomining Attacks