A group of teachers from the North Carolina Condition College and Dokuz Eylul University have shown what they say is the “1st aspect-channel attack” on homomorphic encryption that could be exploited to leak details as the encryption approach is underway.
“Fundamentally, by checking ability consumption in a device that is encoding details for homomorphic encryption, we are ready to browse the info as it is remaining encrypted,” Aydin Aysu, just one of the authors of the examine, claimed. “This demonstrates that even upcoming era encryption technologies have to have defense versus aspect-channel attacks.”
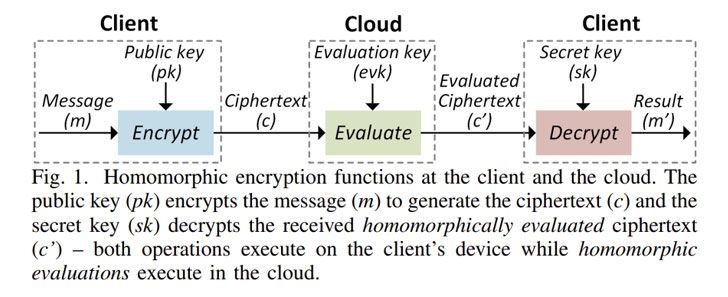
Homomorphic Encryption is a type of encryption that allows specified varieties of computation to be executed instantly on encrypted info with out obtaining to decrypt it in the very first area.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

It truly is also intended to be privacy-preserving in that it will allow sharing of delicate facts with other 3rd-party solutions, these as info analytics corporations, for more processing even though the fundamental details stays encrypted, and by extension, inaccessible to the provider company.
Set otherwise, the goal of homomorphic encryption is to facilitate the growth of conclude-to-end encrypted information storage and computation companies wherever the information owner under no circumstances wants to share their top secret keys with 3rd-party products and services.
The details leakage attack proposed by the researchers involves a vulnerability found in Microsoft SEAL, the tech giant’s open-resource implementation of the technology, which could be exploited in a way that makes it possible for the restoration of a piece of plaintext information that’s getting homomorphically encrypted, successfully undoing the privacy protections.
Exclusively, the attack, dubbed Expose, “targets the Gaussian sampling in the SEAL’s encryption period and can extract the full information with a one electric power measurement,” by getting benefit of a “electricity-centered side-channel leakage of Microsoft SEAL prior to v3.6 that implements the Brakerski/Lover-Vercauteren (BFV) protocol,” the researchers explained.
The scientists mentioned that SEAL variations 3.6, unveiled on December 3, 2020, and afterwards use a unique sampling algorithm, while cautioning that more recent versions of the library may possibly undergo from a “diverse vulnerability.”
“Encryption mistake is sampled from a Centered Binomial Distribution (CBD) by default except if ‘SEAL_USE_GAUSSIAN_NOISE’ is established to ON,” Kim Laine, Microsoft’s principal investigate manager who heads the Cryptography and Privacy Exploration Team, stated in the launch notes.
“Sampling from a CBD is continuous-time and quicker than sampling from a Gaussian distribution, which is why it is utilized by quite a few of the NIST PQC finalists,” Laine additional added.
Located this short article intriguing? Abide by THN on Facebook, Twitter and LinkedIn to study much more exceptional material we submit.
Some components of this report are sourced from:
thehackernews.com



 #CCSE22: The Latest Cybersecurity Workforce Trends
#CCSE22: The Latest Cybersecurity Workforce Trends