Cybersecurity researchers have identified an ongoing attack marketing campaign which is leveraging phishing emails to supply malware known as SSLoad.
The campaign, codenamed FROZEN#SHADOW by Securonix, also involves the deployment of Cobalt Strike and the ConnectWise ScreenConnect remote desktop software package.
“SSLoad is created to stealthily infiltrate methods, get delicate details and transmit its results back to its operators,” security scientists Den Iuzvyk, Tim Peck, and Oleg Kolesnikov mentioned in a report shared with The Hacker News.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“Once inside of the system, SSLoad deploys many backdoors and payloads to manage persistence and stay clear of detection.”
Attack chains involve the use of phishing messages to randomly focus on organizations in Asia, Europe, and the Americas, with e-mail that contains one-way links that guide to the retrieval of a JavaScript file that kicks off the an infection stream.

Earlier this month, Palo Alto Networks uncovered at minimum two diverse strategies by which SSLoad is distributed, one which entails the use of website contact types to embed booby-trapped URLs and an additional involving macro-enabled Microsoft Term files.
The latter is also noteworthy for the point that malware functions as a conduit for offering Cobalt Strike, though the former has been utilised to supply a distinctive malware known as Latrodectus, a probably successor to IcedID.
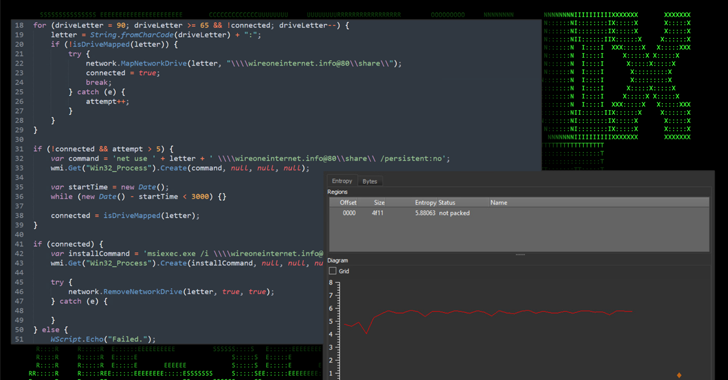
The obfuscated JavaScript file (“out_czlrh.js”), when launched and operate using wscript.exe, retrieves an MSI installer file (“slack.msi”) by connecting to a network share situated at “\wireoneinternet[.]info@80share” and operates it using msiexec.exe.
The MSI installer, for its aspect, contacts an attacker-controlled domain to fetch and execute the SSLoad malware payload applying rundll32.exe, subsequent which it beacons to a command-and-regulate (C2) server alongside with information about the compromised program.
The initial reconnaissance stage paves the way for Cobalt Strike, a legitimate adversary simulation application, which is then applied to obtain and put in ScreenConnect, thereby allowing for the threat actors to remotely commandeer the host.

“With full entry to the procedure the threat actors began attempting to get qualifications and obtain other critical method specifics,” the researchers reported. “At this stage they started scanning the sufferer host for credentials stored in information as nicely as other perhaps delicate files.”
The attackers have also been noticed pivoting to other programs in the network, such as the area controller, finally infiltrating the victim’s Windows area by producing their individual domain administrator account.
“With this amount of obtain, they could get into any linked machine in the area,” the researchers said. “In the finish, this is the worst circumstance state of affairs for any firm as this level of persistence accomplished by the attackers would be amazingly time consuming and high-priced to remediate.”
The disclosure will come as the AhnLab Security Intelligence Centre (ASEC) exposed that Linux units are becoming infected with an open up-supply distant access trojan identified as Pupy RAT.
Found this post attention-grabbing? Comply with us on Twitter and LinkedIn to read through much more special material we put up.
Some elements of this article are sourced from:
thehackernews.com

 Major Security Flaws Expose Keystrokes of Over 1 Billion Chinese Keyboard App Users
Major Security Flaws Expose Keystrokes of Over 1 Billion Chinese Keyboard App Users