The Clear Tribe risk actor has been connected to a new marketing campaign aimed at Indian federal government corporations with trojanized variations of a two-factor authentication alternative referred to as Kavach.
“This team abuses Google commercials for the function of malvertising to distribute backdoored variations of Kavach multi-authentication (MFA) apps,” Zscaler ThreatLabz researcher Sudeep Singh explained in a Thursday evaluation.
The cybersecurity corporation mentioned the innovative persistent menace team has also done very low-volume credential harvesting attacks in which rogue internet websites masquerading as formal Indian govt websites had been established up to lure unwitting end users into getting into their passwords.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Clear Tribe, also acknowledged by the monikers APT36, Procedure C-Significant, and Mythic Leopard, is a suspected Pakistan adversarial collective that has a record of striking Indian and Afghanistan entities.
The hottest attack chain is not the initial time the threat actor has set its sights on Kavach (meaning “armor” in Hindi), a required app demanded by people with email addresses on the @gov.in and @nic.in domains to indication in to the email company as a next layer of authentication.
Previously this March, Cisco Talos uncovered a hacking marketing campaign that employed pretend Windows installers for Kavach as a decoy to infect government staff with CrimsonRAT and other artifacts.
One of their prevalent practices is the mimicking of respectable government, armed forces, and connected businesses to activate the killchain. The most current campaign conducted by the menace actor is no exception.
“The danger actor registered various new domains hosting web web pages masquerading as the formal Kavach app obtain portal,” Singh stated. “They abused the Google Ads’ compensated search element to drive the malicious domains to the top rated of Google search effects for end users in India.”
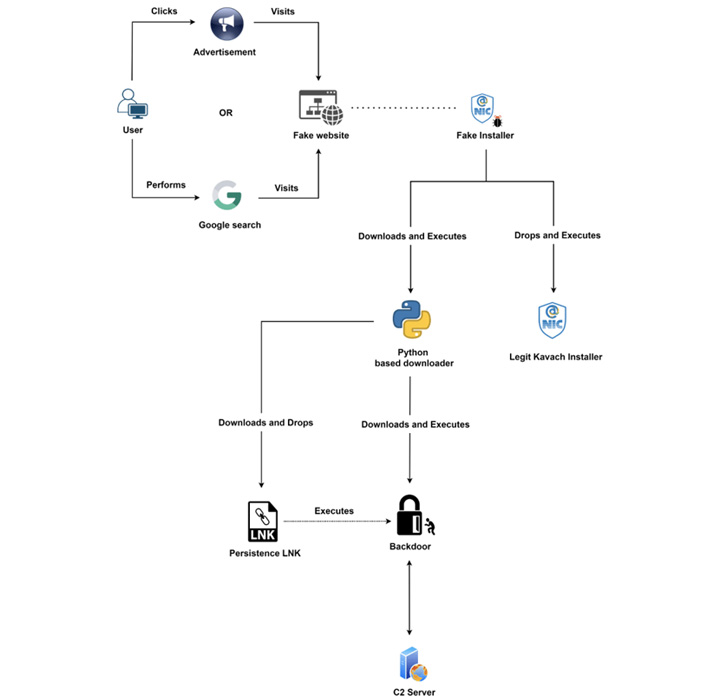
Because May possibly 2022, Transparent Tribe is also explained to have distributed backdoored variations of the Kavach application through attacker-managed application suppliers that claim to present cost-free program downloads.
This web page is also surfaced as a prime consequence in Google lookups, efficiently acting as a gateway to redirect buyers hunting for the app to the .NET-based mostly fraudulent installer.
The team, commencing August 2022, has also been observed utilizing a formerly undocumented knowledge exfiltration device codenamed LimePad, which is made to add data files of fascination from the infected host to the attacker’s server.

Zscaler stated it also identified a domain registered by Clear Tribe spoofing the login webpage of the Kavach app that was only exhibited accessed from an Indian IP deal with, or else redirected the customer to the household website page of India’s Countrywide Informatics Centre (NIC).
The website page, for its component, is equipped to capture the credentials entered by the target and send them to a remote server for carrying out even more attacks in opposition to governing administration-related infrastructure.
The use of Google ads and LimePad points to the risk actor’s ongoing makes an attempt at evolving and refining its practices and malware toolset.
“APT-36 continues to be one particular of the most commonplace highly developed persistent threat teams focused on concentrating on people doing the job in Indian governmental organizations,” Singh explained. “Apps utilised internally at the Indian authorities organizations are a common decision of social engineering theme made use of by the APT-36 team.”
Observed this posting exciting? Follow THN on Facebook, Twitter and LinkedIn to read extra unique articles we article.
Some pieces of this posting are sourced from:
thehackernews.com


 “Disturbing” Rise in Nation State Activity, Microsoft Reports
“Disturbing” Rise in Nation State Activity, Microsoft Reports