Cybersecurity researchers have comprehensive the workings of a absolutely-featured malware loader dubbed PureCrypter that’s being purchased by cyber criminals to supply distant access trojans (RATs) and info stealers.
“The loader is a .NET executable obfuscated with SmartAssembly and can make use of compression, encryption, and obfuscation to evade antivirus software package goods,” Zscaler’s Romain Dumont explained in a new report.


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Some of the malware family members dispersed utilizing PureCrypter incorporate Agent Tesla, Arkei, AsyncRAT, AZORult, DarkCrystal RAT (DCRat), LokiBot, NanoCore, RedLine Stealer, Remcos, Snake Keylogger, and Warzone RAT.
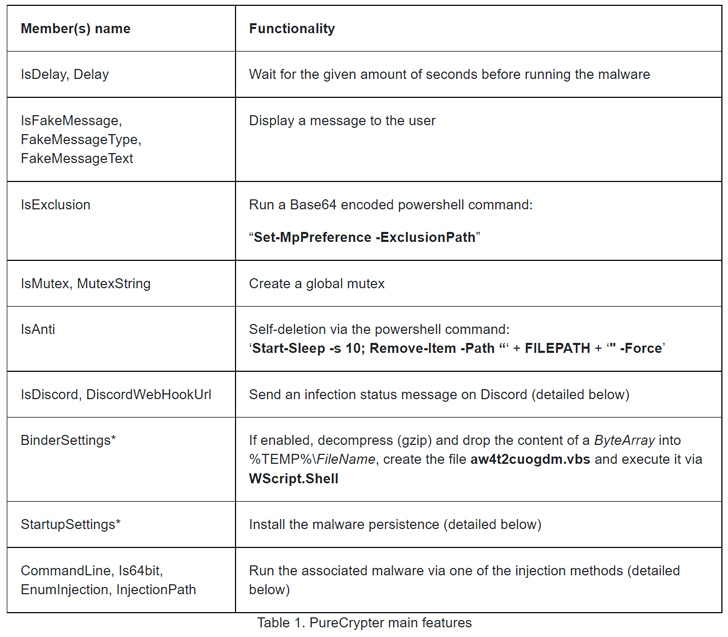
Bought for a cost of $59 by its developer named “PureCoder” for a a single-thirty day period plan (and $249 for a one-off life time buy) considering that at minimum March 2021, PureCrypter is advertised as the “only crypter in the marketplace that takes advantage of offline and on line shipping and delivery strategy.”
Crypters act as the to start with layer of protection against reverse engineering and are normally used to pack the malicious payload. PureCrypter also options what it says is an state-of-the-art mechanism to inject the embedded malware into indigenous procedures and a wide variety of configurable possibilities to reach persistence on startup and transform on extra choices to fly less than the radar.
Also available is a Microsoft Office macro builder and a downloader, highlighting the potential first an infection routes that can be employed to propagate the malware.

Curiously, although PureCoder helps make it a place to be aware that the “application was created for educational functions only,” its conditions of service (ToS) forbids buyers from uploading the software to malware scanning databases such as VirusTotal, Jotti, and MetaDefender.
“You are not authorized to scan the crypted file, as the crypter by itself has a crafted-in scanner,” the ToS further states.
In 1 sample analyzed by Zscaler, a disk picture file (.IMG) was observed to include a to start with-stage downloader that, in switch, retrieves and operates a second-stage module from a distant server, which subsequently injects the remaining malware payload within other processes like MSBuild.
PureCryter also offers a selection of noteworthy functions that makes it possible for it to clear away by itself from the compromised machine and report the infection status to the writer by using Discord and Telegram.
Discovered this write-up intriguing? Comply with THN on Facebook, Twitter and LinkedIn to study far more exceptional information we submit.
Some parts of this article are sourced from:
thehackernews.com

 Apple CEO Tim Cook Pushes Senate For Privacy Legislation
Apple CEO Tim Cook Pushes Senate For Privacy Legislation