LockBit ransomware attacks are frequently evolving by building use of a large selection of tactics to infect targets whilst also using methods to disable endpoint security methods.
“The affiliate marketers that use LockBit’s solutions carry out their attacks in accordance to their choice and use diverse applications and approaches to achieve their target,” Cybereason security analysts Loïc Castel and Gal Romano reported. “As the attack progresses even further along the eliminate chain, the actions from unique cases are inclined to converge to related actions.”
LockBit, which operates on a ransomware-as-a-service (RaaS) design like most teams, was to start with observed in September 2019 and has because emerged as the most dominant ransomware strain this yr, surpassing other nicely-acknowledged groups like Conti, Hive, and BlackCat.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
This entails the malware authors licensing accessibility to affiliate marketers, who execute the attacks in exchange for applying their resources and infrastructure and receive as significantly as 80% of each individual profitable ransom payment acquired from the victims.
LockBit also makes use of the common procedure of double extortion to exfiltrate wide quantities of facts prior to encrypting the assets of the focus on, netting the cybercriminal syndicate no fewer than 850 victims on its details leak site as of May possibly 2022.
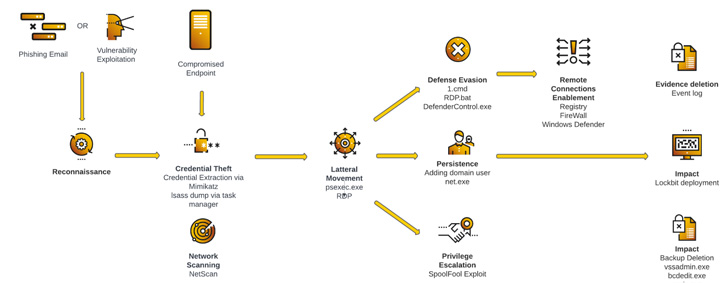 Attack Life Cycle – Scenario Examine 1
Attack Life Cycle – Scenario Examine 1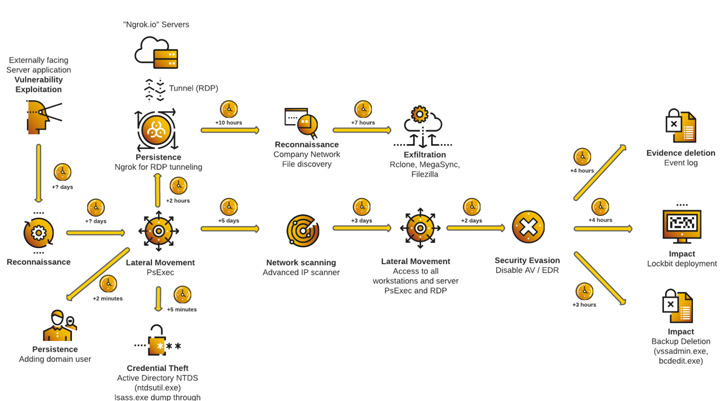 Attack Everyday living Cycle – Situation Examine 2
Attack Everyday living Cycle – Situation Examine 2
According to a leak web site info investigation by Palo Alto Networks Device 42, LockBit accounted for 46% of all ransomware-related breach functions for the to start with quarter of 2022. In June on your own, the group has been tied to 44 attacks, generating it the most energetic ransomware strain.
LockBit ransomware attacks are acknowledged to utilize numerous avenues for initial an infection: Exploiting publicly-exposed RDP ports, relying on phishing e-mail to obtain malicious payloads, or leveraging unpatched server flaws that allow the affiliates to attain distant accessibility to the focused network.
Pursuing this phase are reconnaissance and credential theft actions, which allow the actors to transfer laterally across the network, build persistence, escalate privileges, and launch the ransomware. This is also accompanied by running instructions to delete backups and subvert detection by firewalls and antivirus software.
In the a few years given that LockBit appeared on the scene, the RaaS scheme has acquired two noteworthy upgrades, with the risk actors debuting LockBit 2. in June 2021 and launching the 3rd installment of the company, LockBit 3., past month with aid for Zcash cryptocurrency payment solutions and a bug bounty plan — the first for a ransomware team.

The initiative statements to provide rewards of up to $1 million for getting security blind places in its site and locker software package, distributing outstanding strategies, doxing the head of the gang’s affiliate system, or determining techniques that could expose the IP of the server hosting the internet site on the TOR network.
The bug bounty plan is nonetheless a further sign that hacker teams are progressively functioning as reputable IT enterprises, incorporating HR departments, frequent characteristic releases, and even bonuses for resolving tough difficulties.
However, indications are that LockBit 3., also termed LockBit Black, is influenced by another ransomware loved ones identified as BlackMatter, a rebranded variation of DarkSide that shuttered in November 2021.
“Substantial parts of the code are ripped straight from BlackMatter/Darkside,” Emsisoft researcher Fabian Wosar explained in a tweet before this 7 days. “Guess it is very clear that LockBit acquired their filthy hands on a different group’s code.”
Located this post exciting? Abide by THN on Facebook, Twitter and LinkedIn to read through extra distinctive written content we submit.
Some pieces of this write-up are sourced from:
thehackernews.com

 EU inches closer to blocking Meta from sending personal data to US
EU inches closer to blocking Meta from sending personal data to US