Hundreds of databases on Amazon Relational Databases Provider (Amazon RDS) are exposing particular identifiable information (PII), new results from Mitiga, a cloud incident reaction business, exhibit.
“Leaking PII in this manner gives a possible treasure trove for danger actors – either in the course of the reconnaissance section of the cyber eliminate chain or extortionware/ransomware strategies,” researchers Ariel Szarf, Doron Karmi, and Lionel Saposnik claimed in a report shared with The Hacker Information.
This includes names, email addresses, phone numbers, dates of start, marital status, car rental information, and even corporation logins.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Amazon RDS is a web company that would make it achievable to set up relational databases in the Amazon Web Products and services (AWS) cloud. It provides aid for unique database engines these as MariaDB, MySQL, Oracle, PostgreSQL, and SQL Server.
The root cause of the leaks stems from a element known as public RDS snapshots, which lets for generating a backup of the whole databases natural environment operating in the cloud and can be accessed by all AWS accounts.
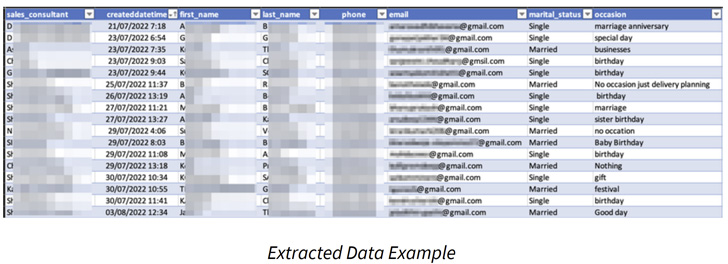
“Make confident when sharing a snapshot as public that none of your non-public information and facts is provided in the community snapshot,” Amazon cautions in its documentation. “When a snapshot is shared publicly, it offers all AWS accounts permission both to copy the snapshot and to produce DB circumstances from it.”
The Israeli corporation, which carried out the exploration from September 21, 2022, to October 20, 2022, reported it discovered 810 snapshots that were being publicly shared for different length, beginning from a handful of hours to weeks, producing them ripe for abuse by destructive actors.

Of the 810 snapshots, more than 250 of the backups had been exposed for 30 times, suggesting that they ended up most likely neglected.
Primarily based on the mother nature of the data uncovered, adversaries could possibly steal the facts for monetary attain or leverage it to get a better grasp of a firm’s IT ecosystem, which could then act as a stepping stone for covert intelligence accumulating endeavours.
It’s hugely suggested that RDS snapshots are not publicly accessible in get to avert likely leak or misuse of sensitive details or any other type of security danger. It truly is also advised to encrypt snapshots where by relevant.
Observed this article appealing? Comply with THN on Fb, Twitter and LinkedIn to read through extra special content we publish.
Some components of this report are sourced from:
thehackernews.com


 7 Reasons to Choose an MDR Provider
7 Reasons to Choose an MDR Provider