Cybersecurity scientists have uncovered a PlugX sample that employs sneaky procedures to infect connected removable USB media gadgets in get to propagate the malware to further systems.
“This PlugX variant is wormable and infects USB gadgets in this kind of a way that it conceals alone from the Windows working file technique,” Palo Alto Networks Unit 42 researchers Mike Harbison and Jen Miller-Osborn claimed. “A user would not know their USB gadget is infected or quite possibly used to exfiltrate data out of their networks.”
The cybersecurity company explained it uncovered the artifact through an incident reaction effort following a Black Basta ransomware attack from an unnamed target. Among the other tools found in the compromised atmosphere contain the Gootkit malware loader and the Brute Ratel C4 crimson group framework.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The use of Brute Ratel by the Black Basta team was beforehand highlighted by Development Micro in Oct 2022, with the computer software shipped as a next-stage payload by means of a Qakbot phishing campaign. The attack chain has considering that been made use of versus a substantial, regional energy outfit based in the southeastern U.S., according to Quadrant Security.
Nevertheless, there is no evidence that ties PlugX, a backdoor thoroughly shared throughout many Chinese nation-point out groups, or Gootkit to the Black Basta ransomware gang, suggesting that it could have been deployed by other actors.
The USB variant of PlugX is noteworthy for the simple fact that it utilizes a unique Unicode character named non-breaking house (U+00A0) to disguise documents in a USB gadget plugged into a workstation.
“The whitespace character stops the Windows working program from rendering the listing identify, concealing it rather than leaving a anonymous folder in Explorer,” the scientists stated, outlining the novel technique.
Finally, a Windows shortcut (.LNK) file developed in the root folder of the flash travel is utilized to execute the malware from the hidden directory. The PlugX sample is not only tasked with implanting the malware on the host, but also copying it on any removable gadget that might be related to it by camouflaging it within a recycle bin folder.
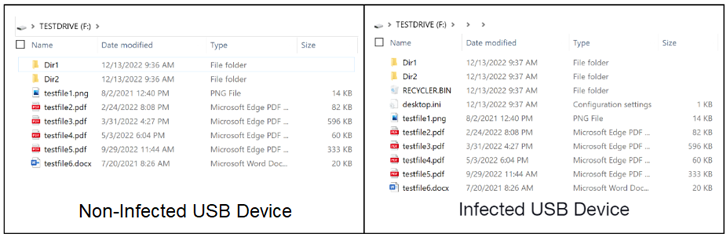
The shortcut file, for its section, carries the exact same title as that of the USB product and appears as a travel icon, with the current information or directories on the root of the removable machine moved to a hidden folder made inside of the “shortcut” folder.
“Every time the shortcut file from the contaminated USB system is clicked, the PlugX malware launches Windows Explorer and passes the directory route as a parameter,” Device 42 said. “This then shows the information on the USB system from within just the concealed directories and also infects the host with the PlugX malware.”
The approach financial institutions on the actuality that Windows File Explorer (beforehand Windows Explorer) by default does not clearly show hidden items. But the clever twist listed here is that the malicious files inside of the so-identified as recycle bin do not get shown when with the environment enabled.
This correctly usually means that the rogue files can only be considered on a Unix-like operating method like Ubuntu or by mounting the USB device in a forensic resource.
“At the time a USB product is uncovered and contaminated, any new data files published to the USB unit root folder article-an infection are moved to the hidden folder in the USB product,” the scientists reported. “Because the Windows shortcut file resembles that of a USB unit and the malware shows the victim’s data files, they unwittingly keep on to distribute the PlugX malware.”
Device 42 explained it also found out a 2nd variant of PlugX that, in addition to infecting USB units, even further copies all Adobe PDF and Microsoft Term data files from the host to another concealed folder on the USB gadget developed by the malware.
The use of USB drives as a usually means to exfiltrate precise files of desire from its targets indicates an attempt on part of the menace actors to leap about air-gapped networks.
With the most up-to-date improvement, PlugX joins the ranks of other malware people this sort of as ANDROMEDA and Raspberry Robin that have additional the functionality to spread via contaminated USB drives.
“The discovery of these samples implies PlugX development is nonetheless alive and properly among the at least some technically expert attackers, and it remains an active risk,” the scientists concluded.
Uncovered this post exciting? Abide by us on Twitter and LinkedIn to browse additional exclusive content we write-up.
Some sections of this article are sourced from:
thehackernews.com

 Security is Key to Business Transformation, Say IT Chiefs
Security is Key to Business Transformation, Say IT Chiefs