New findings from cybersecurity business JFrog exhibit that malware focusing on the npm ecosystem can evade security checks by having advantage of an “unpredicted actions” in the npm command line interface (CLI) device.
npm CLI’s set up and audit instructions have designed-in abilities to check a bundle and all of its dependencies for recognised vulnerabilities, effectively acting as a warning system for builders by highlighting the flaws.
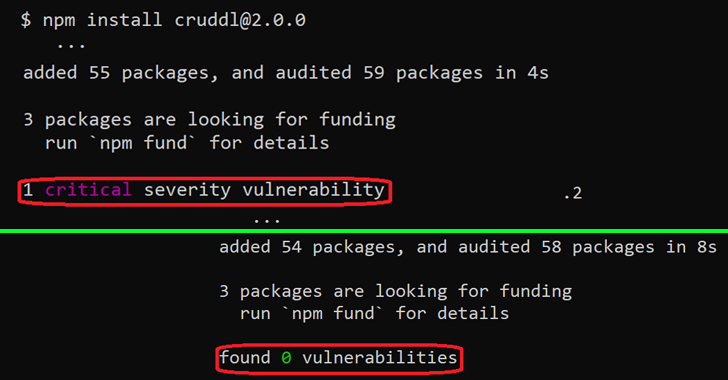
But as JFrog founded, the security advisories are not exhibited when the deals adhere to specific variation formats, making a circumstance wherever critical flaws could be launched into their techniques both directly or via the package’s dependencies.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

Specially, the trouble occurs only when the set up package edition consists of a hyphen (e.g., 1.2.3-a), which is included to denote a pre-launch edition of an npm module.
While the venture maintainers handle the discrepancy involving frequent npm package variations and pre-launch variations as an intended performance, this also helps make it ripe for abuse by attackers seeking to poison the open up source ecosystem.
“Risk actors could exploit this behavior by intentionally planting susceptible or malicious code in their innocent-looking packages which will be integrated by other developers owing to important performance or as a blunder due to an infection strategies these kinds of as typosquatting or dependency confusion,” Or Peles mentioned.
In other text, an adversary could publish a seemingly benign package that’s in the pre-launch edition structure, which could then be perhaps picked up by other builders and not be alerted to the point that the package deal is destructive in spite of proof to the opposite.
The advancement the moment all over again reiterates how the software program provide chain is developed as a chain of rely on involving different get-togethers, and how a compromise of one particular hyperlink can have an affect on all downstream programs that take in the rogue 3rd-party dependency.
To counter these kinds of threats, it can be suggested that developers stay away from installing npm deals with a pre-release variation, unless of course the source is acknowledged to be absolutely trustworthy.
Uncovered this post attention-grabbing? Adhere to THN on Fb, Twitter and LinkedIn to go through extra distinctive written content we post.
Some pieces of this report are sourced from:
thehackernews.com

 Hyundai vulnerability allowed remote hacking of locks, engine
Hyundai vulnerability allowed remote hacking of locks, engine