New findings have recognized connections in between an Android spyware termed DragonEgg and yet another refined modular iOS surveillanceware device named LightSpy.
DragonEgg, along with WyrmSpy (aka AndroidControl), was to start with disclosed by Lookout in July 2023 as a strain of malware able of gathering delicate facts from Android equipment. It was attributed to the Chinese country-point out group.
On the other hand, particulars about LightSpy arrived to light in March 2020 as section of a marketing campaign dubbed Operation Poisoned News in which Apple iPhone buyers in Hong Kong have been specific with watering gap attacks to put in the spy ware.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

Now, according to Dutch mobile security company ThreatFabric, the attack chains involve the use of a trojanized Telegram app that is made to obtain a next-phase payload (smallmload.jar), which, in transform, is configured to download a third part codenamed Core.
More examination of the artifacts has disclosed that the implant has been actively taken care of considering the fact that at the very least December 11, 2018, with the most current model released on July 13, 2023.
The main module of LightSpy (i.e., DragonEgg) features as an orchestrator plugin responsible for accumulating the gadget fingerprint, developing get hold of with a remote server, awaiting further guidance, and updating by itself as perfectly as the plugins.
“LightSpy Core is very adaptable in conditions of configuration: operators can precisely manage the spyware applying the updatable configuration,” ThreatFabric mentioned, noting that WebSocket is used for command delivery and HTTPS is applied for data exfiltration.
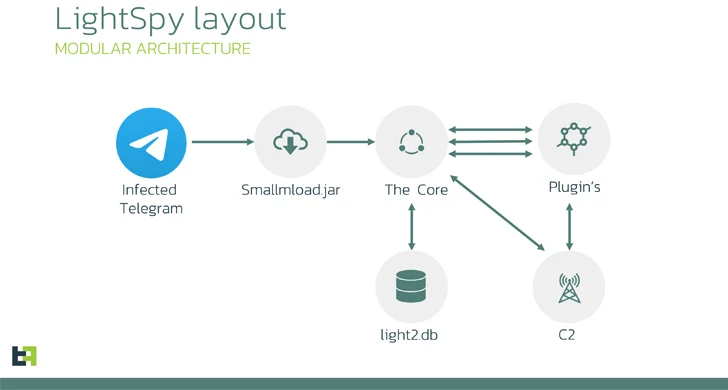
Some of the notable plugins incorporate a locationmodule that tracks victims’ exact destinations, soundrecord that can seize ambient audio as well as from WeChat VOIP audio discussions, and a monthly bill module to gather payment record from WeChat Pay.
LightSpy’s command-and-manage (C2) contains numerous servers situated in Mainland China, Hong Kong, Taiwan, Singapore, and Russia, with the malware and WyrmSpy sharing the identical infrastructure.

ThreatFabric reported it also recognized a server hosting knowledge from 13 exclusive phone numbers belonging to Chinese cell phone operators, elevating the possibility that the knowledge possibly represents the tests numbers of LightSpy builders or victims’.
The backlinks amongst DragonEgg and LightSpy stem from similarities in configuration designs, runtime composition and plugins, and the C2 communication structure.
“The way the threat actor group dispersed the initial destructive phase inside of popular messenger was a clever trick,” the business claimed.
“There were quite a few positive aspects of that: the implant inherited all the access permissions that the provider application had. In the case of messenger, there were being a large amount of non-public permissions this kind of as digicam and storage access.”
Observed this short article attention-grabbing? Stick to us on Twitter and LinkedIn to browse additional exclusive written content we put up.
Some elements of this article are sourced from:
thehackernews.com

 Wing Disrupts the Market by Introducing Affordable SaaS Security
Wing Disrupts the Market by Introducing Affordable SaaS Security