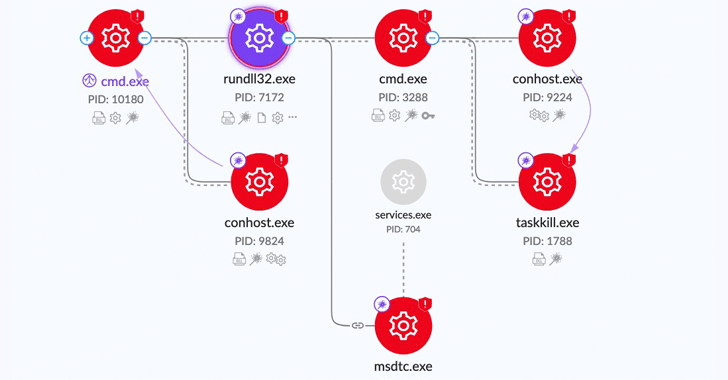
The risk actors guiding the CatB ransomware procedure have been observed making use of a strategy called DLL search order hijacking to evade detection and launch the payload.
CatB, also referred to as CatB99 and Baxtoy, emerged late past calendar year and is stated to be an “evolution or immediate rebrand” of a different ransomware pressure known as Pandora centered on code-level similarities.
It is really really worth noting that the use of Pandora has been attributed to Bronze Starlight (aka DEV-0401 or Emperor Dragonfly), a China-centered threat actor that’s recognised to employ short-lived ransomware families as a ruse to probable conceal its accurate goals.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
1 of the crucial defining attributes of CatB is its reliance on DLL hijacking by means of a reputable company called Microsoft Dispersed Transaction Coordinator (MSDTC) to extract and launch the ransomware payload.
“On execution, CatB payloads count on DLL look for get hijacking to drop and load the malicious payload,” SentinelOne researcher Jim Walter reported in a report revealed very last week. “The dropper (versions.dll) drops the payload (oci.dll) into the Procedure32 listing.”
The dropper is also liable for carrying out anti-analysis checks to decide if the malware is staying executed in a digital surroundings, and in the end abusing the MSDTC service to inject the rogue oci.dll made up of the ransomware into the msdtc.exe executable upon method restart.
“The [MSDTC] configurations improved are the identify of the account underneath which the company should operate, which is adjusted from Network Service to Neighborhood Method, and the services start off possibility, which is altered from Demand from customers get started to Vehicle commence for persistency if a restart happens,” Minerva Labs researcher Natalie Zargarov described in a past analysis.
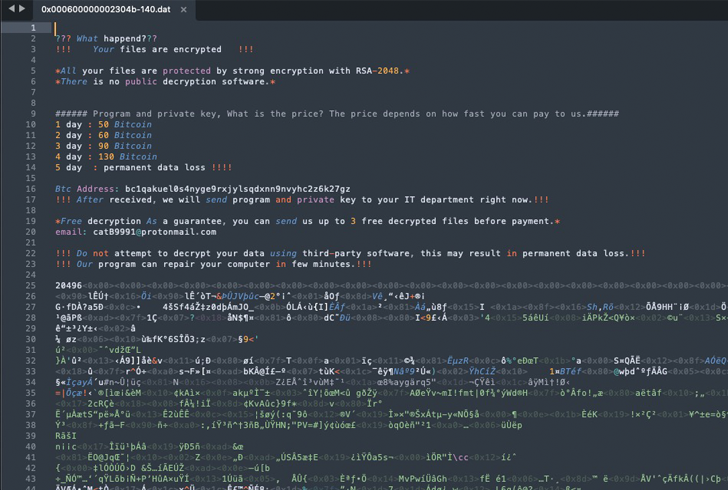
1 hanging factor of the ransomware is its absence of a ransom note. As an alternative, each individual encrypted file is up-to-date with a message urging the victims to make a Bitcoin payment.
WEBINARDiscover the Concealed Potential risks of Third-Party SaaS Apps
Are you conscious of the risks associated with third-party application entry to your firm’s SaaS apps? Sign up for our webinar to study about the varieties of permissions staying granted and how to lessen risk.
RESERVE YOUR SEAT
An additional trait is the malware’s ability to harvest delicate facts these kinds of as passwords, bookmarks, heritage from web browsers Google Chrome, Microsoft Edge (and Internet Explorer), and Mozilla Firefox.
“CatB joins a extensive line of ransomware families that embrace semi-novel procedures and atypical behaviors these as appending notes to the head of data files,” Walter mentioned. “These behaviors surface to be implemented in the curiosity of detection evasion and some level of anti-investigation trickery.”
This is not the first time the MSDTC company has been weaponized for malicious reasons. In Might 2021, Trustwave disclosed a novel malware dubbed Pingback that employed the identical technique to achieve persistence and bypass security options.
Uncovered this posting interesting? Abide by us on Twitter and LinkedIn to browse extra unique information we write-up.
Some components of this write-up are sourced from:
thehackernews.com

 Scam Robocalls Forecast to Cost $58bn This Year
Scam Robocalls Forecast to Cost $58bn This Year