A new campaign carried out by Earth Preta signifies that nation-point out teams aligned with China are receiving increasingly proficient at bypassing security answers.
The threat actor, lively considering the fact that at minimum 2012, is tracked by the broader cybersecurity group under Bronze President, HoneyMyte, Mustang Panda, RedDelta, and Pink Lich.
Attack chains mounted by the group begin with a spear-phishing email to deploy a wide variety of applications for backdoor access, command-and-command (C2), and details exfiltration.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
These messages come bearing with malicious lure archives distributed by using Dropbox or Google Drive backlinks that utilize DLL side-loading, LNK shortcut information, and fake file extensions as arrival vectors to receive a foothold and drop backdoors like TONEINS, TONESHELL, PUBLOAD, and MQsTTang (aka QMAGENT).
Equivalent infection chains utilizing Google Travel hyperlinks have been observed providing Cobalt Strike as early as April 2021.
“Earth Preta tends to disguise destructive payloads in pretend files, disguising them as legitimate kinds — a technique that has been confirmed effective for avoiding detection,” Trend Micro claimed in a new investigation printed Thursday.
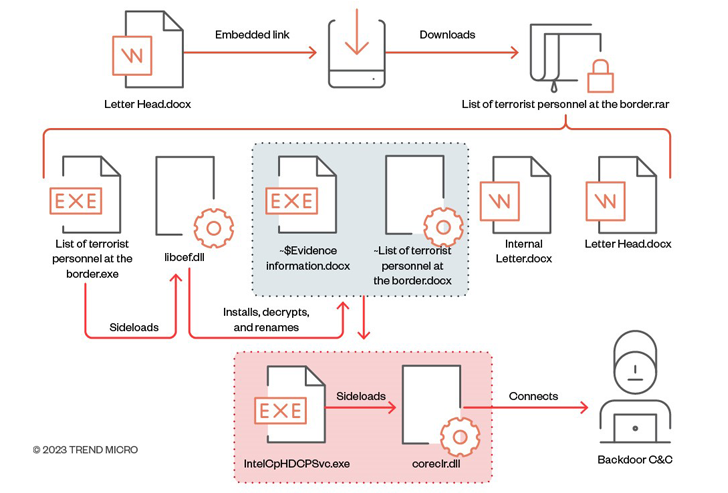
This entry stage strategy, which was 1st noticed late previous 12 months, has considering the fact that obtained a slight tweak wherein the download hyperlink to the archive is embedded within an additional decoy doc and the file is password-shielded in an try to sidestep email gateway answers.
“The documents can then be extracted within through the password provided in the document,” the researchers reported. “By employing this method, the destructive actor guiding the attack can effectively bypass scanning companies.”
Initial entry to the victim’s ecosystem is adopted by account discovery and privilege escalation phases, with Mustang Panda leveraging custom made instruments like ABPASS and CCPASS to circumvent Person Account Handle (UAC) in Windows 10.
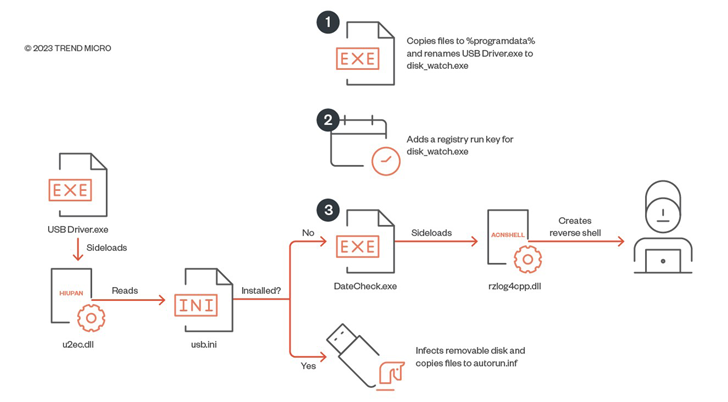
In addition, the risk actor has been noticed deploying malware these types of as “USB Driver.exe” (HIUPAN or MISTCLOAK) and “rzlog4cpp.dll” (ACNSHELL or BLUEHAZE) to install by themselves to detachable disks and make a reverse shell with the aim of laterally moving across the network.
WEBINARDiscover the Hidden Risks of 3rd-Party SaaS Applications
Are you knowledgeable of the hazards involved with 3rd-party application entry to your firm’s SaaS applications? Join our webinar to discover about the types of permissions remaining granted and how to limit risk.
RESERVE YOUR SEAT
Other utilities deployed include things like CLEXEC, a backdoor capable of executing instructions and clearing occasion logs COOLCLIENT and TROCLIENT, implants that are developed to record keystrokes as very well as read through and delete documents and PlugX.
“Aside from nicely-known reputable resources, the danger actors also crafted really customized resources utilised for exfiltration,” the scientists observed. This contains NUPAKAGE and ZPAKAGE, both equally of which are outfitted to gather Microsoft Office environment information.
The conclusions when once again spotlight the amplified operational tempo of Chinese cyber espionage actors and their steady expenditure in advancing their cyber weaponry to evade detection.
“Earth Preta is a capable and arranged threat actor that is repeatedly honing its TTPs, strengthening its enhancement abilities, and setting up a flexible arsenal of equipment and malware,” the scientists concluded.
Observed this report intriguing? Follow us on Twitter and LinkedIn to examine far more unique material we post.
Some parts of this posting are sourced from:
thehackernews.com

 Fifth of Execs Admit Security Flaws Cost Them New Biz
Fifth of Execs Admit Security Flaws Cost Them New Biz