Cybersecurity researchers have detailed a “uncomplicated but economical” persistence mechanism adopted by a somewhat nascent malware loader termed Colibri, which has been noticed deploying a Windows information and facts stealer acknowledged as Vidar as component of a new marketing campaign.
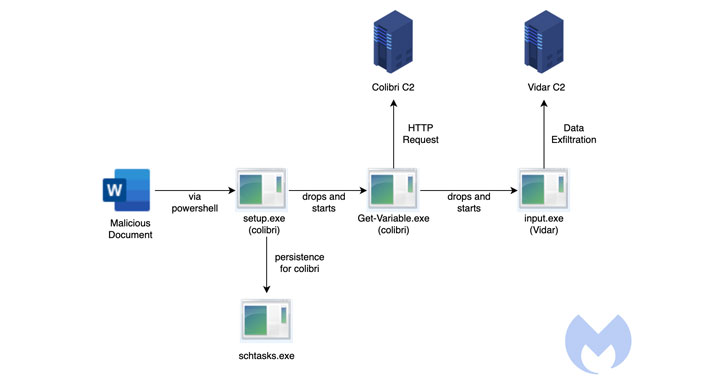
“The attack commences with a malicious Word document deploying a Colibri bot that then delivers the Vidar Stealer,” Malwarebytes Labs reported in an examination. “The document contacts a distant server at (securetunnel[.]co) to load a distant template named ‘trkal0.dot’ that contacts a destructive macro,” the researchers additional.
First documented by FR3D.HK and Indian cybersecurity business CloudSEK before this 12 months, Colibri is a malware-as-a-support (MaaS) system which is engineered to fall supplemental payloads on to compromised methods. Early signs of the loader appeared on Russian underground message boards in August 2021.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“This loader has many tactics that assist steer clear of detection,” CloudSEK researcher Marah Aboud noted previous thirty day period. “This incorporates omitting the IAT (Import Handle Table) along with the encrypted strings to make the examination much more tricky.”

The marketing campaign attack chain noticed by Malwarebytes takes benefit of a procedure referred to as remote template injection to obtain the Colibri loader (“set up.exe”) by means of a weaponized document.
The loader then makes use of a earlier undocumented persistence technique to endure equipment reboots, but not ahead of dropping its own duplicate to the area “%APPDATA%LocalMicrosoftWindowsApps” and naming it “Get-Variable.exe.”
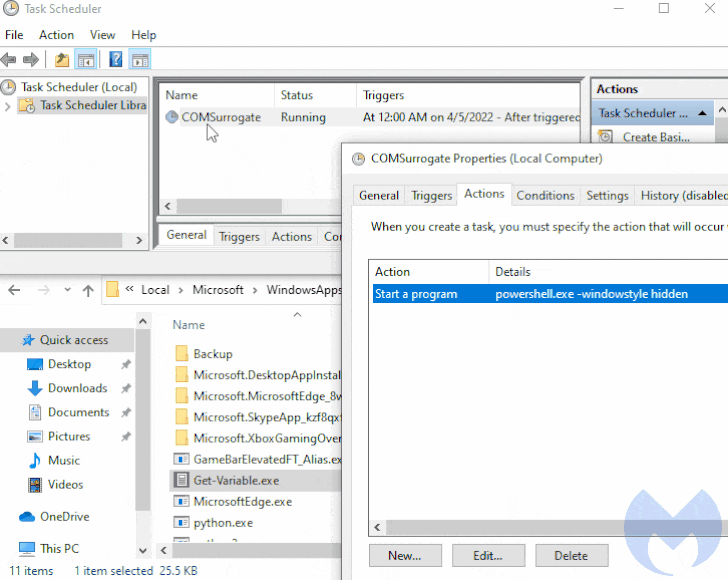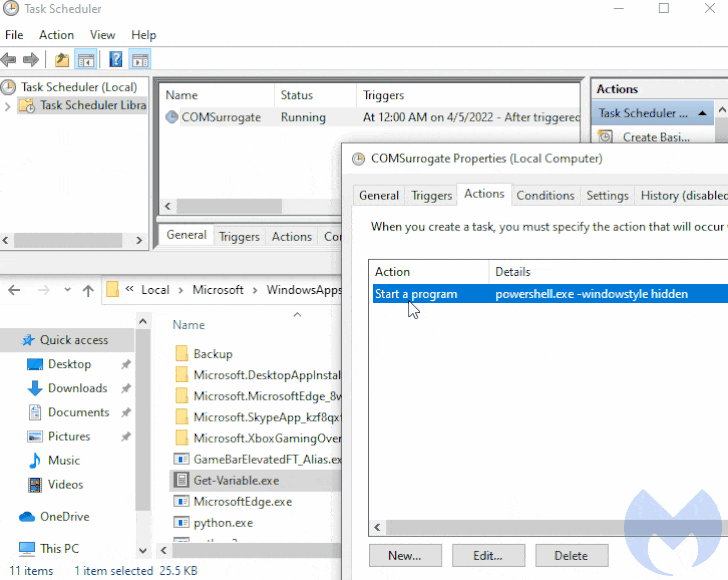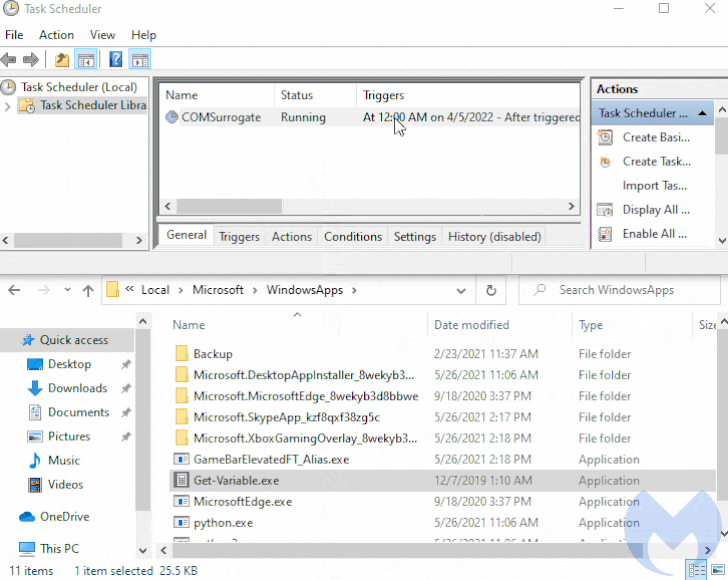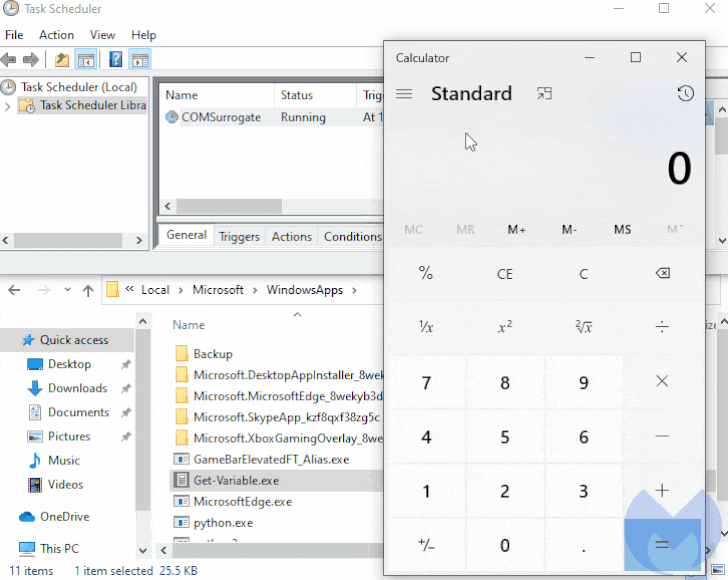
It does this by producing a scheduled process on programs operating Windows 10 and previously mentioned, with the loader executing a command to start PowerShell with a hidden window (i.e., -WindowStyle Hidden) to conceal the destructive action from getting detected.
“It so transpires that Get-Variable is a valid PowerShell cmdlet (a cmdlet is a light-weight command used in the Windows PowerShell setting) which is employed to retrieve the benefit of a variable in the recent console,” the researchers spelled out.
But given the point that PowerShell is executed by default in the WindowsApps path, the command issued throughout the scheduled task development results in the execution of the malicious binary in the location of its reputable counterpart.
This effectively indicates that “an adversary can very easily accomplish persistence [by] combining a scheduled job and any payload (as lengthy as it is termed Get-Variable.exe and put in the suitable site),” the researcher stated.
The most recent findings occur as cybersecurity organization Trustwave past month in depth an email-dependent phishing marketing campaign that leverages Microsoft Compiled HTML Assistance (CHM) data files to distribute the Vidar malware in an energy to fly under the radar.
Identified this report interesting? Follow THN on Fb, Twitter and LinkedIn to read far more distinctive material we put up.
Some areas of this short article are sourced from:
thehackernews.com


 Employee Info Among 13 Million Records Leaked by Fox News
Employee Info Among 13 Million Records Leaked by Fox News