A now-patched security flaw in Microsoft Outlook could be exploited by threat actors to obtain NT LAN Supervisor (NTLM) v2 hashed passwords when opening a specially crafted file.
The issue, tracked as CVE-2023-35636 (CVSS rating: 6.5), was addressed by the tech big as element of its Patch Tuesday updates for December 2023.
“In an email attack situation, an attacker could exploit the vulnerability by sending the specially crafted file to the user and convincing the person to open up the file,” Microsoft explained in an advisory produced final thirty day period.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
In a web-based mostly attack state of affairs, an attacker could host a site (or leverage a compromised website that accepts or hosts user-provided written content) that contains a specially crafted file developed to exploit the vulnerability.”

Set otherwise, the adversary would have to encourage customers to simply click a backlink, possibly embedded in a phishing email or sent by way of an instantaneous concept, and then deceive them into opening the file in query.
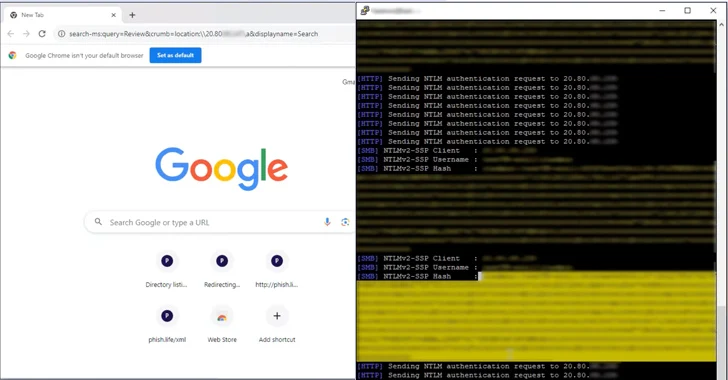
CVE-2023-35636 is rooted in the calendar-sharing function in the Outlook email application, whereby a destructive email concept is made by inserting two headers “Written content-Course” and “x-sharing-config-url” with crafted values in order to expose a victim’s NTLM hash during authentication.
Varonis security researcher Dolev Taler, who has been credited with discovering and reporting the bug, claimed NTLM hashes could be leaked by leveraging Windows Performance Analyzer (WPA) and Windows File Explorer. These two attack methods, on the other hand, keep on being unpatched.
“What makes this fascinating is that WPA attempts to authenticate using NTLM v2 above the open up web,” Taler mentioned.

“Usually, NTLM v2 really should be utilized when making an attempt to authenticate towards inside IP-address-centered providers. Even so, when the NTLM v2 hash is passing by means of the open internet, it is vulnerable to relay and offline brute-drive attacks.”
The disclosure comes as Verify Place unveiled a case of “forced authentication” that could be weaponized to leak a Windows user’s NTLM tokens by tricking a target into opening a rogue Microsoft Obtain file.
Microsoft, in October 2023, declared plans to discontinue NTLM in Windows 11 in favor of Kerberos for enhanced security owing to the reality that it does not assistance cryptographic strategies and is vulnerable to relay attacks.
Located this short article fascinating? Adhere to us on Twitter and LinkedIn to go through much more exceptional information we article.
Some areas of this post are sourced from:
thehackernews.com

 493 Companies Share Their SaaS Security Battles – Get Insights in this Webinar
493 Companies Share Their SaaS Security Battles – Get Insights in this Webinar