A Chinese-talking state-of-the-art persistent threat (APT) actor codenamed MirrorFace has been attributed to a spear-phishing marketing campaign concentrating on Japanese political institutions.
The action, dubbed Procedure LiberalFace by ESET, particularly concentrated on users of an unnamed political party in the nation with the intention of providing an implant termed LODEINFO and a hitherto unseen credential stealer named MirrorStealer.
The Slovak cybersecurity firm explained the marketing campaign was introduced a minimal more than a 7 days prior to the Japanese House of Councillors election that took position on July 10, 2022.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
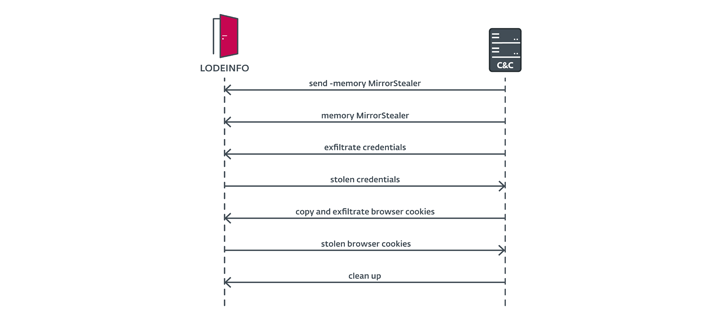
“LODEINFO was used to produce further malware, exfiltrate the victim’s credentials, and steal the victim’s files and e-mail,” ESET researcher Dominik Breitenbacher mentioned in a technical report printed Wednesday.

MirrorFace is said to share overlaps with yet another danger actor tracked as APT10 (aka Bronze Riverside, Cicada, Earth Tengshe, Stone Panda, and Potassium) and has a historical past of striking corporations and companies primarily based in Japan.
Without a doubt, a pair of studies from Kaspersky in November 2022 connected LODEINFO infections targeting media, diplomatic, governmental and community sector companies, and believe-tanks in Japan to Stone Panda.
ESET, on the other hand, said it hasn’t discovered evidence to tie the attacks to a earlier identified APT group, insteading monitoring it as a standalone entity. It also described LODEINFO as a “flagship backdoor” exclusively used by MirrorFace.
The spear-phishing e-mails, despatched on June 29, 2022, purported to be from the political party’s PR department, urging the recipients to share the hooked up videos on their possess social media profiles to “protected victory” in the elections.
Nonetheless, the videos ended up self-extracting WinRAR archives developed to deploy LODEINFO on the compromised equipment, allowing for using screenshots, logging keystrokes, killing procedures, exfiltrating data files, and executing supplemental files and instructions.
Also delivered was the MirrorStealer credential grabber that is capable of plundering passwords from browsers and email clients like Becky!, which is largely made use of in Japan.
“When MirrorStealer had collected the qualifications and saved them in %temp%31558.txt, the operator utilised LODEINFO to exfiltrate the qualifications,” Breitenbacher discussed, considering that it “won’t have the functionality to exfiltrate the stolen info.”
The attacks further produced use of a next-phase LODEINFO malware that comes with capabilities to operate portable executable binaries and shellcode.
“MirrorFace proceeds to goal for superior-benefit targets in Japan,” ESET explained. “In Operation LiberalFace, it precisely targeted political entities making use of the then-upcoming House of Councillors election to its edge.”
Observed this report attention-grabbing? Adhere to us on Twitter and LinkedIn to study additional distinctive written content we write-up.
Some sections of this post are sourced from:
thehackernews.com

 Microsoft Reclassifies SPNEGO Extended Negotiation Security Vulnerability as Critical RCE
Microsoft Reclassifies SPNEGO Extended Negotiation Security Vulnerability as Critical RCE