Cybersecurity scientists have found a new superior-severity security flaw in PaperCut print management program for Windows that could final result in remote code execution underneath unique situations.
Tracked as CVE-2023-39143 (CVSS rating: 8.4), the flaw impacts PaperCut NG/MF prior to version 22.1.3. It has been described as a mix of a path traversal and file add vulnerability.
“CVE-2023-39143 enables unauthenticated attackers to possibly go through, delete, and add arbitrary information to the PaperCut MF/NG software server, resulting in distant code execution in specified configurations,” Horizon3.ai’s Naveen Sunkavally stated.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The cybersecurity agency claimed that file add leading to remote code execution is attainable when the exterior device integration environment is enabled, which is on by default in some installations of PaperCut.

Previously this April, yet another remote code execution vulnerability in the exact merchandise (CVE-2023-27350, CVSS score: 9.8) and an information disclosure flaw (CVE-2023–27351) arrived beneath common exploitation in the wild to supply Cobalt Strike and ransomware. Iranian country-point out actors have been also spotted abusing the bugs to acquire original access to goal networks.
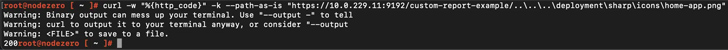
“When compared to CVE-2023-27350, CVE-2023-39143 also does not involve attackers to have any prior privileges to exploit, and no user conversation is necessary,” Sunkavally pointed out. “CVE-2023-39143 is additional elaborate to exploit, involving various issues that should be chained with each other to compromise a server. It is not a ‘one-shot’ RCE vulnerability.”
Also remediated by PaperCut in edition 22.1.3 is a security flaw that could enable an unauthenticated attacker with direct server IP obtain to add arbitrary data files into a goal directory, primary to a likely denial-of-service (CVE-2023-3486, CVSS rating: 7.4). Tenable has been credited with getting and reporting the issue.
Found this article exciting? Observe us on Twitter and LinkedIn to read extra unique material we publish.
Some areas of this article are sourced from:
thehackernews.com


 NYC Couple Pleads Guilty to Money Laundering in $3.6 Billion Bitfinex Hack
NYC Couple Pleads Guilty to Money Laundering in $3.6 Billion Bitfinex Hack