Aspects have emerged about a previously undocumented malware marketing campaign carried out by the Iranian MuddyWater sophisticated persistent menace (APT) team concentrating on Turkish private businesses and governmental establishments.
“This campaign utilizes malicious PDFs, XLS files and Windows executables to deploy malicious PowerShell-centered downloaders performing as first footholds into the target’s business,” Cisco Talos researchers Asheer Malhotra and Vitor Ventura stated in a recently revealed report.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The advancement arrives as the U.S. Cyber Command, earlier this thirty day period, joined the APT to the Iranian Ministry of Intelligence and Security (MOIS).
The intrusions, which are believed to have been operational as not too long ago as November 2021, were directed towards Turkish government entities, which includes the Scientific and Technological Exploration Council of Turkey (TÜBİTAK), working with weaponized Excel documents and PDF files hosted on attacker-controlled or media-sharing internet sites.

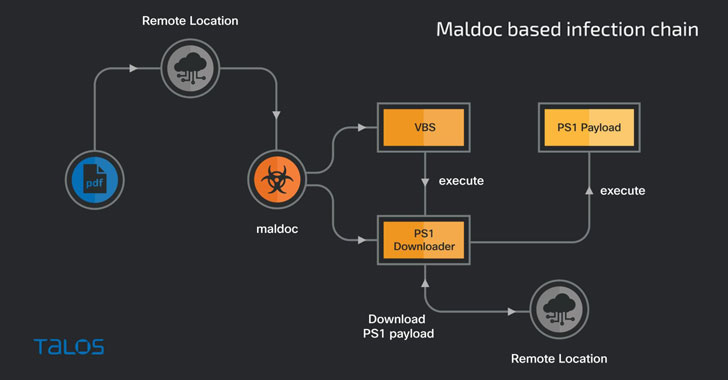
These maldocs masqueraded as genuine paperwork from the Turkish Overall health and Inside Ministries, with the attacks setting up by executing malicious macros embedded in them to propagate the infection chain and fall PowerShell scripts to the compromised process.
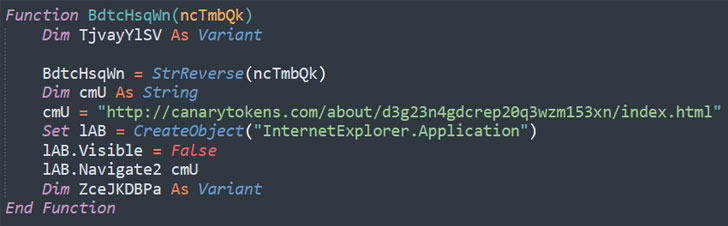
A new addition to the group’s arsenal of methods, approaches and techniques (TTPs) is the use of canary tokens in the macro code, a system the researchers suspect is being utilized to observe profitable infection of targets, thwart examination, and detect if the payload servers are being blocked at the other finish.
Canary tokens, also recognised as honeytokens, are identifiers embedded in objects like documents, web pages and e-mails, which, when opened, triggers an warn in the form of an HTTP ask for, alerting the operator that the item was accessed.
The PowerShell script subsequently downloads and executes the up coming payload, also a PowerShell script that resides in the metadata of the maldoc, which, in switch, acts as the downloader for a 3rd, unknown PowerShell code which is eventually operate on the contaminated endpoint.
In a second variant of the attacks noticed by Talos, the PDF paperwork with embedded back links have been found pointing to Windows executables as a substitute of the Excel data files, which then instrumented the an infection chain to deploy the PowerShell downloaders.
What is actually far more, the scientists claimed they found at minimum two diverse versions of the executable sent by the adversary targeting the telecommunications sector in Armenia in June 2021 and Pakistani entities in August 2021, boosting the chance that MuddyWater may perhaps have engaged in numerous attacks as part of a person very long steady campaign.
The disclosure also follows the release of a Non-public Sector Notification (PIN) by the U.S. Federal Bureau of Investigation (FBI) final 7 days, detailing the destructive cyber routines of an Iran-dependent cyber organization named Emennet Pasargad, which was tied to a complex affect marketing campaign orchestrated to interfere in the 2020 presidential elections.
“These actors are remarkably capable and motivated to execute their espionage actions,” the scientists concluded. “With new methods these kinds of as canary tokens applied to observe thriving infection of targets, MuddyWater has demonstrated their adaptability and unwillingness to refrain by themselves from attacking other nations.”
Found this short article appealing? Abide by THN on Fb, Twitter and LinkedIn to browse extra exceptional material we article.
Some elements of this write-up are sourced from:
thehackernews.com



 New SureMDM Vulnerabilities Could Expose Companies to Supply Chain Attacks
New SureMDM Vulnerabilities Could Expose Companies to Supply Chain Attacks