Cybersecurity researchers have created what is actually the very first completely undetectable cloud-dependent cryptocurrency miner leveraging the Microsoft Azure Automation company devoid of racking up any expenses.
Cybersecurity firm SafeBreach mentioned it learned three various procedures to run the miner, which includes just one that can be executed on a victim’s atmosphere without having attracting any interest.
“Even though this study is considerable because of its prospective affect on cryptocurrency mining, we also feel it has severe implications for other locations, as the tactics could be utilised to obtain any undertaking that demands code execution on Azure,” security researcher Ariel Gamrian stated in a report shared with The Hacker Information.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The review largely set out to identify an “greatest crypto miner” that gives limitless access to computational sources, even though concurrently requiring very little-to-no upkeep, is charge-free of charge, and undetectable.

Which is the place Azure Automation will come in. Made by Microsoft, it’s a cloud-based mostly automation services that permits people to automate the development, deployment, monitoring, and servicing of assets in Azure.
SafeBreach reported it discovered a bug in the Azure pricing calculator that produced it probable to execute an infinite amount of work thoroughly free of charge of demand, though it relates to the attacker’s setting itself. Microsoft has because issued a deal with for the issue.
An alternate strategy entails creating a take a look at-work for mining, adopted by location its status as “Failed,” and then making a further dummy test-career by taking advantage of the fact that only a single take a look at can run at the identical time.
The finish result of this movement is that it completely hides code execution inside of the Azure natural environment.
A risk actor could leverage these strategies by setting up a reverse shell to an external server and authenticating to the Automation endpoint to realize their objectives.
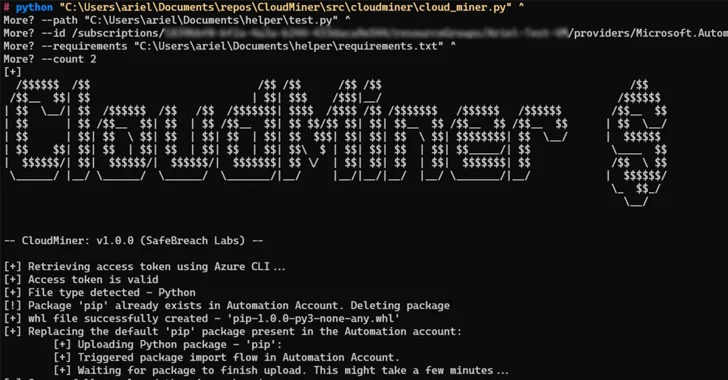
Also, it was observed that code execution could be accomplished by leveraging Azure Automation’s function that lets users to upload customized Python offers.
“We could make a malicious deal named ‘pip’ and add it to the Automation Account,” Gamrian defined.
“The add move would substitute the current pip in the Automation account. After our tailor made pip was saved in the Automation account, the company applied it every single time a offer was uploaded.”

SafeBreach has also created obtainable a evidence-of-idea dubbed CoinMiner which is intended to get cost-free computing electric power within just Azure Automation service by applying the Python package deal upload system.
Microsoft, in response to the disclosures, has characterised the conduct as “by design and style,” indicating the technique can continue to be exploited without finding charged.
Even though the scope of the research is confined to the abuse of Azure Automation for cryptocurrency mining, the cybersecurity firm warned that the exact same techniques could be repurposed by risk actors to accomplish any activity that necessitates code execution on Azure.
“As cloud company buyers, particular person corporations need to proactively check each individual solitary useful resource and each individual motion becoming performed in just their environment,” Gamrian reported.
“We remarkably recommend that companies teach by themselves about the methods and flows malicious actors may use to build undetectable resources and proactively check for code execution indicative of these kinds of habits.”
Discovered this write-up fascinating? Abide by us on Twitter and LinkedIn to read a lot more exclusive articles we write-up.
Some components of this short article are sourced from:
thehackernews.com

 WhatsApp Introduces New Privacy Feature to Protect IP Address in Calls
WhatsApp Introduces New Privacy Feature to Protect IP Address in Calls