A new piece of analysis from lecturers at ETH Zurich has discovered a number of critical security issues in the MEGA cloud storage service that could be leveraged to break the confidentiality and integrity of consumer facts.
In a paper titled “MEGA: Malleable Encryption Goes Awry,” the researchers position out how MEGA’s method does not secure its people from a malicious server, thus enabling a rogue actor to fully compromise the privacy of the uploaded documents.
“In addition, the integrity of person info is ruined to the extent that an attacker can insert malicious files of their preference which go all authenticity checks of the consumer,” ETH Zurich’s Matilda Backendal, Miro Haller, and Kenneth G. Paterson said in an evaluation of the service’s cryptographic architecture.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
MEGA, which advertises itself as the “privacy enterprise” and statements to present person-controlled conclusion-to-end encrypted cloud storage, has far more than 10 million every day active customers, with above 122 billion files uploaded to the system to day.

Chief between the weaknesses is an RSA Vital Recovery Attack that helps make it feasible for MEGA (alone acting maliciously) or a resourceful country-point out adversary in management of its API infrastructure to recuperate a user’s RSA non-public vital by tampering with 512 login tries and decrypt the saved content material.
“As soon as a qualified account had produced ample effective logins, incoming shared folders, MEGAdrop files and chats could have been decryptable,” Mathias Ortmann, MEGA’s chief architect, mentioned in response to the results. “Data files in the cloud drive could have been successively decrypted for the duration of subsequent logins.”
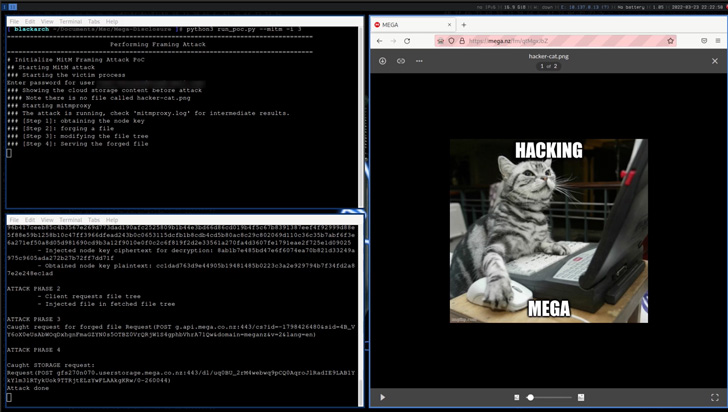
The recovered RSA key can then be extended to make way for four other attacks –
- Plaintext Restoration Attack, which allows MEGA to decrypt node keys — an encryption crucial affiliated with every single uploaded file and are encrypted with a user’s learn important — and use them to decrypt all person conversation and data files.
- Framing Attack, whereby MEGA can insert arbitrary documents into the user’s file storage that are indistinguishable from genuinely uploaded types.
- Integrity Attack, a significantly less stealthy variant of the Framing Attack that can be exploited to forge a file in the identify of the target and spot it in the target’s cloud storage, and
- Guess-and-Purge (Hole) Bleichenbacher attack, a variant of the Adaptive selected-ciphertext attack devised by Swiss cryptographer Daniel Bleichenbacher in 1998 that could be exploited to decrypt RSA ciphertexts.
“Each consumer has a public RSA important made use of by other consumers or MEGA to encrypt details for the operator, and a personal vital used by the consumer them selves to decrypt data shared with them,” the researchers described. “With this [GaP Bleichenbacher attack], MEGA can decrypt these RSA ciphertexts, albeit requiring an impractical range of login attempts.”
In a nutshell, the attacks could be weaponized by MEGA or any entity managing its core infrastructure to upload lookalike documents and decrypt all documents and folders owned by or shared with the victim as well as the chat messages exchanged.

The shortcomings are extreme as they undermine MEGA’s intended security assures, prompting the corporation to issue updates to address the to start with a few of the five issues. The fourth vulnerability related to the breach of integrity is anticipated to be tackled in an future launch.
As for the Bleichenbacher-style attack from MEGA’s RSA encryption mechanism, the company famous the attack is “complicated to accomplish in observe as it would require close to 122,000 client interactions on normal” and that it would get rid of the legacy code from all of its shoppers.
MEGA further emphasized that it’s not conscious of any user accounts that may possibly have been compromised by the aforementioned attack procedures.
“The reported vulnerabilities would have demanded MEGA to grow to be a negative actor towards sure of its customers, or otherwise could only be exploited if a further party compromised MEGA’s API servers or TLS connections with out getting seen,” Ortmann pointed out.
“The attacks […] come up from surprising interactions concerning seemingly independent factors of MEGA’s cryptographic architecture,” the researchers elaborated. “They hint at the trouble of retaining huge-scale methods utilizing cryptography, especially when the technique has an evolving established of features and is deployed throughout numerous platforms.”
“The attacks offered right here display that it is possible for a inspired party to come across and exploit vulnerabilities in actual entire world cryptographic architectures, with devastating final results for security. It is conceivable that programs in this class attract adversaries who are ready to make investments major sources to compromise the support by itself, rising the plausibility of substantial-complexity attacks.”
Found this article interesting? Abide by THN on Fb, Twitter and LinkedIn to examine a lot more special content material we write-up.
Some sections of this post are sourced from:
thehackernews.com


 #InfosecurityEurope2022: The Critical Yet Often Invisible Role Cryptography Plays in Our Lives
#InfosecurityEurope2022: The Critical Yet Often Invisible Role Cryptography Plays in Our Lives